HOTSPOT -
You have a computer named Computer1 that runs Windows 10 and is joined to an Active Directory domain named adatum.com.
A user named Admin1 signs in to Computer1 and runs the whoami command as shown in the following exhibit.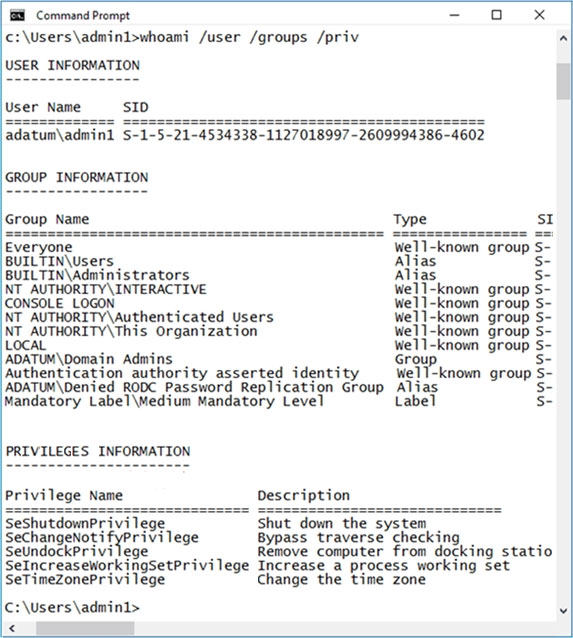
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: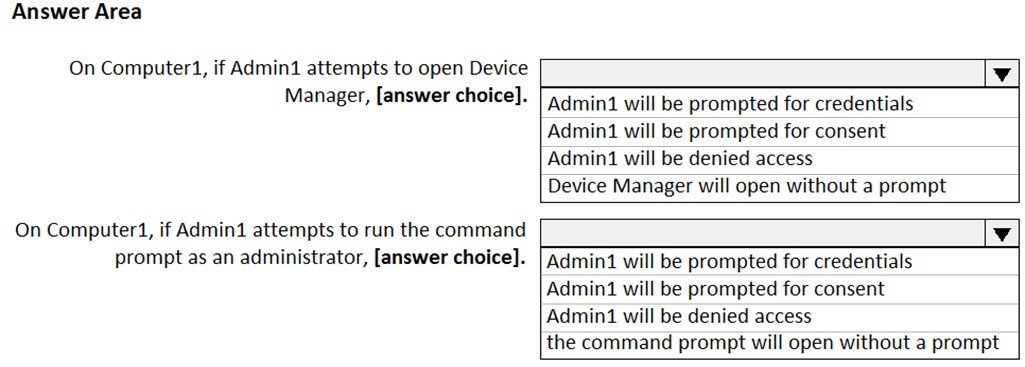
Answer:
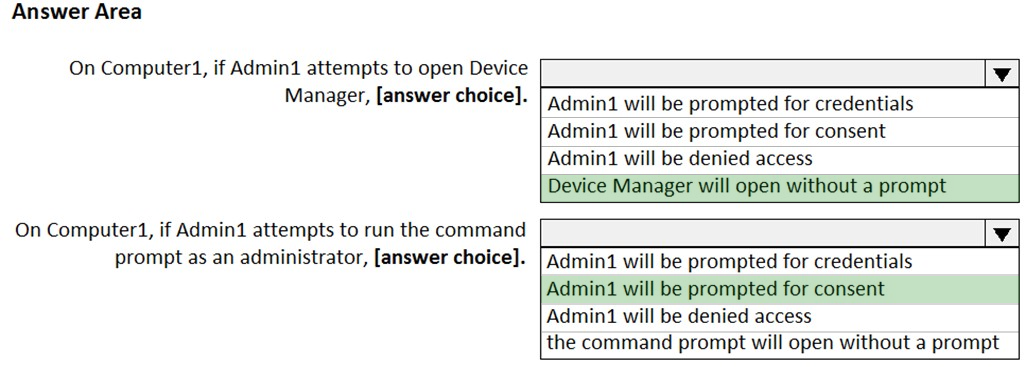
Reference:
https://docs.microsoft.com/en-us/windows/win32/secauthz/mandatory-integrity-control
Your network contains an Active Directory domain. The domain contains a computer named Computer1 that runs Windows 10.
The domain contains the users shown in the following table.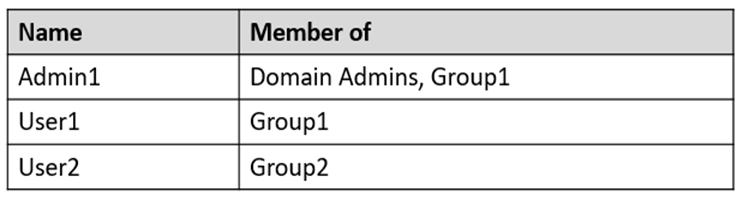
Computer1 has four printers as shown in the following table.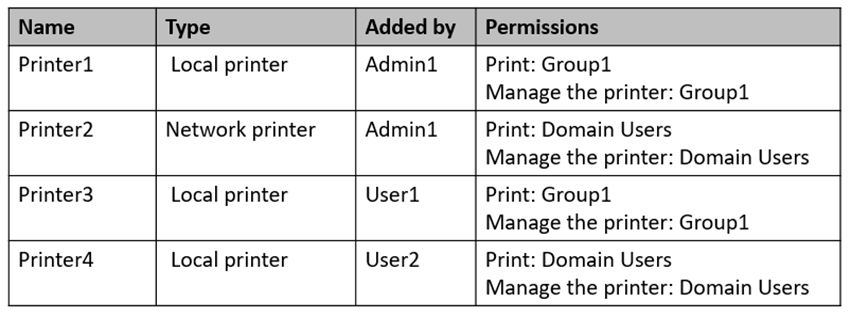
Which printers will be available to User1 when the user signs in to Computer1?
Answer:
E
HOTSPOT -
Your network contains an Active Directory domain. The domain contains the users shown in the following table.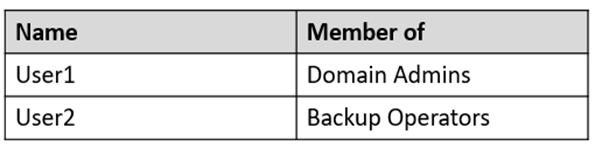
The domain contains a computer named Computer1. Computer1 contains the users shown in the following table.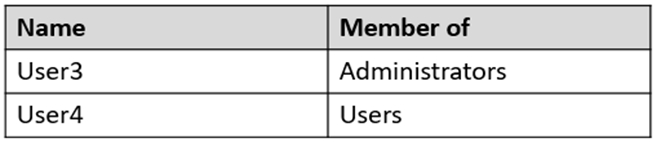
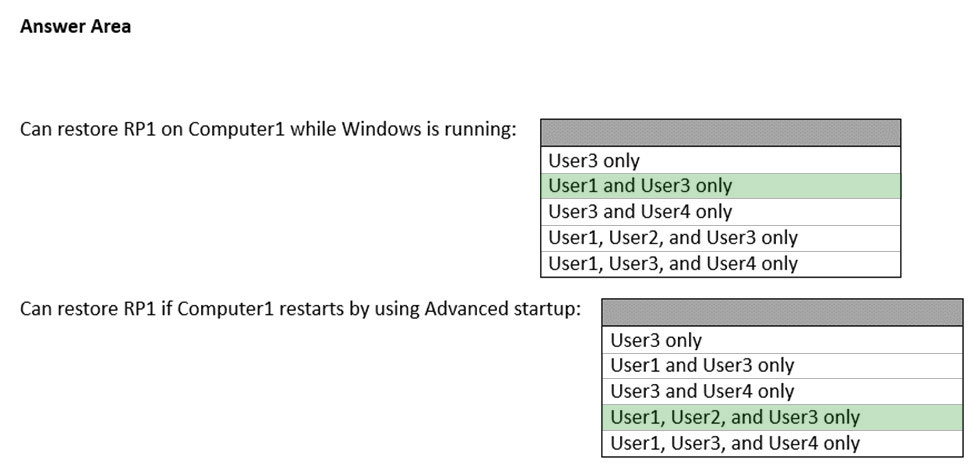
On Computer1, you create a restore point named RP1.
Which users can restore RP1 on Computer1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: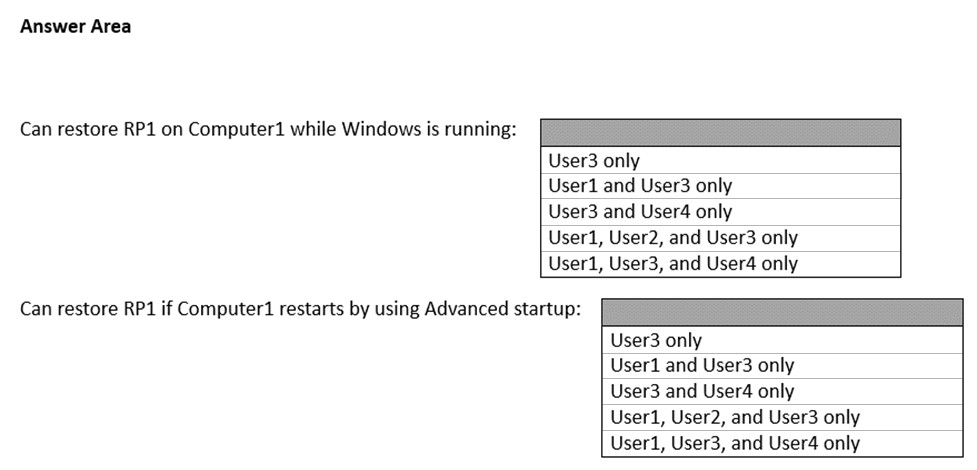
Answer:
Reference:
https://ss64.com/nt/syntax-security_groups.html
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a computer that runs Windows 10. The computer contains a folder. The folder contains sensitive data.
You need to log which user reads the contents of the folder and modifies and deletes files in the folder.
Solution: From the properties of the folder, you configure the Auditing settings and from the Audit Policy in the local Group Policy, you configure Audit privilege use.
Does this meet the goal?
Answer:
B
Files and folders are objects and are audited through object access, not though privilege use.
Reference:
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
HOTSPOT -
Your network contains an Active Directory domain named contoso.com. The domain contains a computer named Computer1 that runs Windows 10.
Several user settings are configured in a Default Domain Policy Group Policy Object (GPO).
Users sign in to Computer1 as shown in the following table.
You configure the following GPOs on Computer1:
✑ Local Computer
✑ Local Computer\User2
✑ Local Computer\Administrators
Local Computer\Non-Administrators
Each GPO has different user settings configured.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: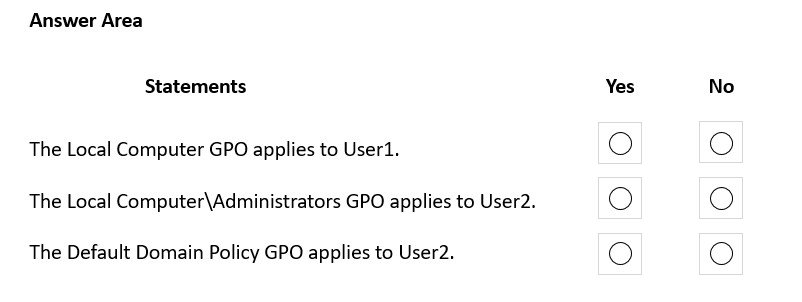
Answer:
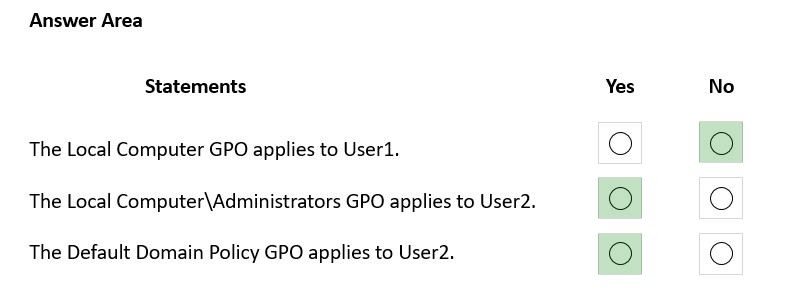
Box 1: No -
Box 2: Yes -
Box 3: Yes -
All account policies settings applied by using Group Policy are applied at the domain level. Default values are present in the built-in default domain controller policy for Password Policy settings, Account Lockout Policy settings, and Kerberos Policy settings. The domain account policy becomes the default local account policy of any device that is a member of the domain.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account-policies
You have a Windows 10 device.
You need to ensure that a remote administrator can connect to the device by using Quick Assist.
What should you do first?
Answer:
D
How it works -
Both the helper and the sharer start Quick Assist.
1. The helper selects Assist another person. Quick Assist on the helper's side contacts the Remote Assistance Service to obtain a session code. An RCC chat session is established and the helper's Quick Assist instance joins it. The helper then provides the code to the sharer.
2. After the sharer enters the code in their Quick Assist app, Quick Assist uses that code to contact the Remote Assistance Service and join that specific session.
The sharer's Quick Assist instance joins the RCC chat session.
3. The helper is prompted to select View Only or Full Control.
4. Etc.
Reference:
https://docs.microsoft.com/en-us/windows/client-management/quick-assist
HOTSPOT -
You have a computer that runs Windows 10.
You need to configure the local computer policy to meet the following requirements:
✑ An event must be created in the Security log when changes are made to local users or groups.
✑ The local administrator and guest accounts must be renamed.
Which Security Settings should you modify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: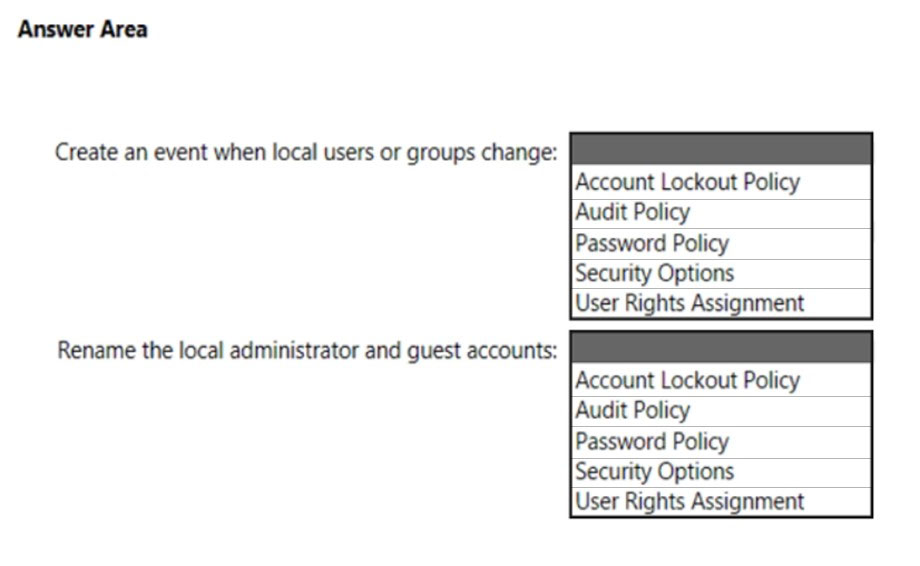
Answer:
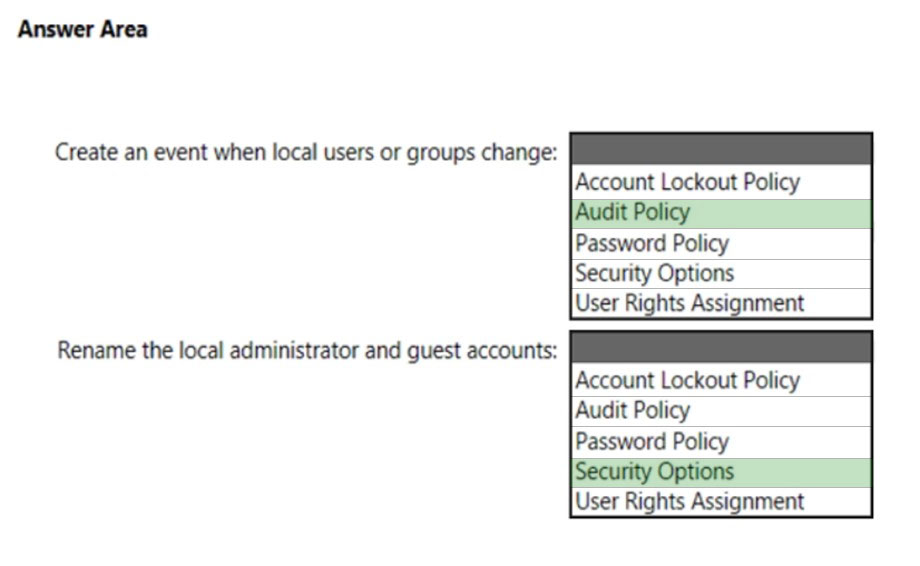
Box 1: Audit Policy -
An event must be created in the Security log when changes are made to local users or groups.
The Audit Policy Provides information about basic audit policies that are available in Windows and links to information about each setting.
The basic audit policy settings under Security Settings\Local Policies\Audit Policy are:
Audit account logon events -
Audit account management -
Audit directory service access -
Audit logon events -
Audit object access -
Audit policy change -
Audit privilege use -
Audit process tracking -
Audit system events -
Box 2: Security options -
Rename the administrator and guest accounts.
1. Start the Active Directory Users and Computers snap-in.
2. In the console tree, right-click your domain or the organizational unit that contains the Group Policy that you want, and then click Properties.
3. Click the Group Policy tab, click the Group Policy object that you want, and then click Edit. For example, click the Rename Administrator and Guest accounts
Group Policy object, and then click Edit.
4. Expand Computer Configuration, expand Windows Settings, expand Security Settings, expand Local Policies, and then click Security Options.
5. In the right pane, double-click Accounts: Rename administrator account.
6. Click to select the Define this policy setting check box, and then type the new name that you want to use for the administrator account.
7. Click OK.
8. Double-click Accounts: Rename guest account.
9. Click to select the Define this policy setting check box, and then type the new name that you want to use for the guest account.
10.Click OK, and then quit the Group Policy Object Editor snap-in.
11.Quit the Active Directory Users and Computers snap-in.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/audit-policy
You have a computer that runs Windows 11 and has Windows Sandbox enabled.
You need to create a custom Windows Sandbox configuration file.
Which file extension should you use?
Answer:
D
DRAG DROP
-
You have a computer that runs Windows 11 and has Windows Sandbox enabled.
You need to configure a Windows Sandbox environment. The solution must meet the following requirements:
• Support a virtual GPU.
• Mount the C:\Temp folder as read only.
• Prevent users from copying files to the sandbox by using the clipboard.
How should you complete the configuration file? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Answer:

Your network contains an Active Directory domain. The domain contains computers that run Windows 10.
All users use Roaming User Profiles.
You have a user named Public1 that is used to sign-in to a public computer.
You need to prevent changes to the user settings of Public1 from being saved to the user profile.
What should you do?
Answer:
D