HOTSPOT -
You have two workgroup computers named Computer1 and Computer2 that run Windows 10. The computers contain the local security principals shown in the following table.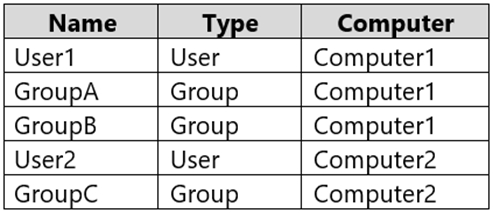
Which security principals can be members of GroupA and GroupC? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: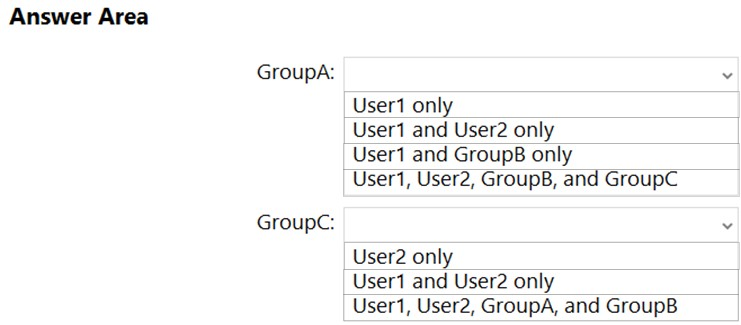
Answer:
A user purchases a new computer that has Windows 10 Home preinstalled. The computer has a biometric fingerprint reader.
You need to ensure that the user can use the fingerprint reader to sign in to the computer by using an Azure Active Directory (Azure AD) account.
What should you do first?
Answer:
B
HOTSPOT -
Your network contains an Active Directory domain. The domain contains three computers named Computer1, Computer2, and Computer3 that run Windows 10.
The computers are on the same network and have network connectivity.
Windows Defender Firewall on Computer1 has the server-to-server connection security rule shown in the following table.
Windows Defender Firewall on Computer2 has the server-to-server connection security rule shown in the following table.
Windows Defender Firewall on Computer3 has the server-to-server connection security rule shown in the following table.
All the connection security rules are enabled and configured to use only the Computer (Kerberos V5) authentication method.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/create-an-authentication-request-rule
HOTSPOT -
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.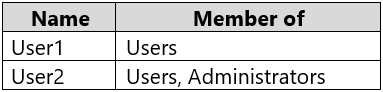
[1]
Computer1 has the Local Computer\Administrators Policy shown in the following table.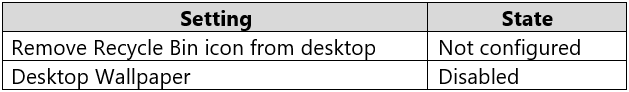
Computer1 has the Local Computer\Non-Administrators Policy shown in the following table.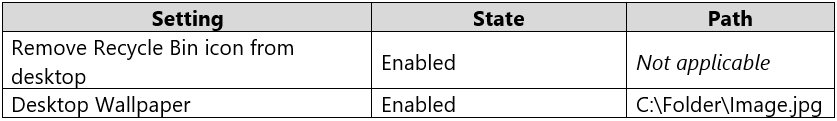
Computer1 has the local computer policy shown in the following table.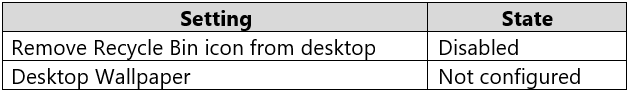
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: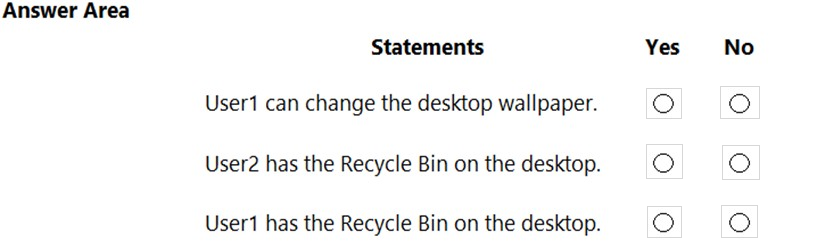
Answer:
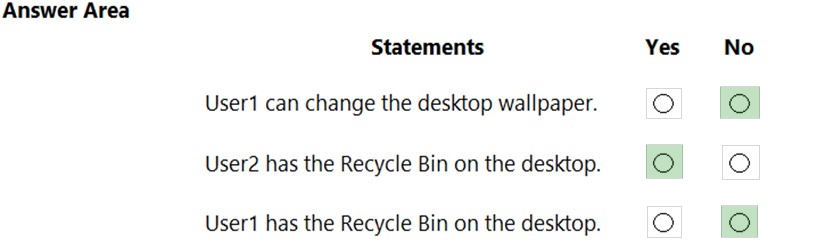
Box 1: No -
The Desktop Wallpaper setting in the Local Computer\Non-Administrators Policy specifies the path to the wallpaper image. Therefore, User1 will not be able to change the wallpaper.
Box 2: Yes -
The Remove Recycle Bin from desktop setting in the Local Computer\Administrators Policy is Not Configured which means it will not overwrite the setting in the
Local Computer Policy. The Remove Recycle Bin from desktop setting in the Local Computer Policy is Disabled. Therefore, the Recycle Bin icon is not removed.
In other words, it will be visible on the desktop.
Box 3: No -
The Remove Recycle Bin from desktop setting in the Local Computer\Non-Administrators Policy is enabled. Therefore, the Recycle Bin will be removed for User1.
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You configure Microsoft Edge settings by using domain and local Group Policy Objects (GPOs).
You need to generate a report that contains all the Microsoft Edge policy settings applied to a computer.
What should you do?
Answer:
C
The Get-GPOReport cmdlet would generate a report for all domain group policy objects. However, this would not display the settings that are applied by local group policy objects.
To display the settings applied by both domain and local GPOs, you would have to open Microsoft Edge and enter edge://policy in the address bar.
HOTSPOT -
You have a computer named Computer1 that runs Windows 10.
You need to modify the Security Settings of Computer1 to meet the following requirements:
✑ A local group named Branch_Admins must be able to view and clear the Security log.
✑ Local users must be prompted to change their password three days before the password expires.
Which two nodes of the Local Group Policy Editor should you access to configure the settings? To answer, select the appropriate nodes in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: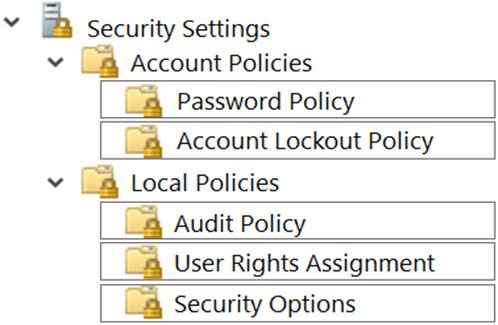
Answer:
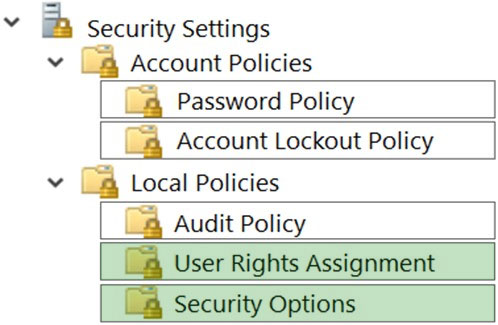
User Rights Assignment > Manage auditing and security log.
Security Options > Interactive Logon: Prompt user to change password before expiration: 3 days.
You have a computer that runs Windows 10 Pro. The computer contains the users shown in the following table.
You need to use a local Group Policy Object (GPO) to configure one group of settings for all the members of the local Administrators group and another group of settings for all non-administrators.
What should you do?
Answer:
B
Add the Group Policy Object Editor snap-in twice. Select Browse > Users > Administrators when you add the first snap-in and select Browse > Users > Non-
Administrators when you add the second snap-in.
Your network contains an Active Directory domain. The domain contains 1,000 computers that run Windows 10.
You configure Microsoft Edge settings by using domain and local Group Policy Objects (GPOs).
You need to generate a report that contains all the Microsoft Edge policy settings applied to a computer.
What should you do?
Answer:
C
The Get-GPOReport cmdlet would generate a report for all domain group policy objects. However, this would not display the settings that are applied by local group policy objects.
To display the settings applied by both domain and local GPOs, you would have to open Microsoft Edge and enter edge://policy in the address bar.
HOTSPOT -
Your network contains an Active Directory forest. The forest contains a root domain named contoso.com and a child domain named corp.contoso.com.
You have a computer named Computer1 that runs Windows 10. Computer1 is joined to the corp.contoso.com domain.
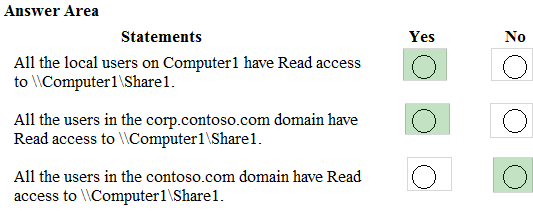
Computer1 contains a folder named Folder1. In the Security settings of Folder1, Everyone is assigned the Full control permission.
On Computer1, you share Folder1 as Share1 and assign the Read permissions for Share1 to the local Users group.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
Reference:
https://www.techrepublic.com/article/learn-the-basic-differences-between-share-and-ntfs-permissions/
HOTSPOT -
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup.
Computer1 contains the folders shown in the following table.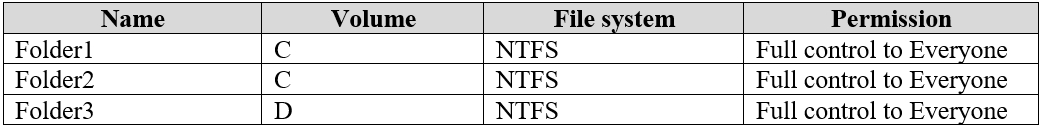
On Computer1, you create the users shown in the following table.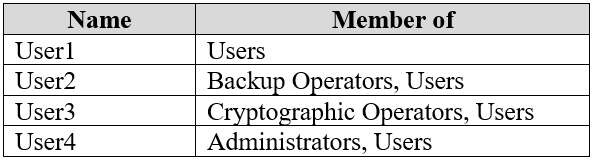
User1 encrypts a file named File1.txt that is in a folder named C:\Folder1.
What is the effect of the configuration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: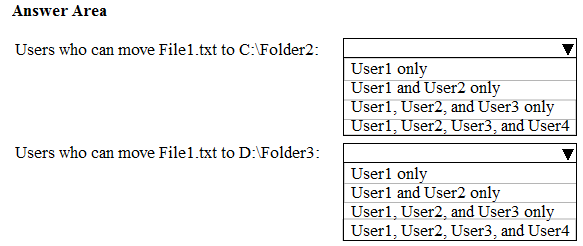
Answer:
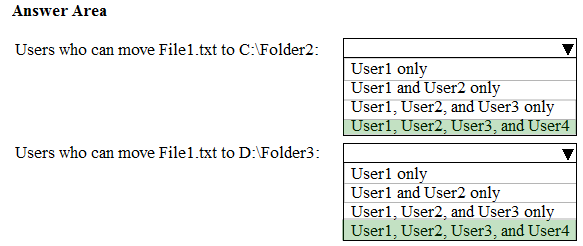
Reference:
https://support.microsoft.com/en-za/help/310316/how-permissions-are-handled-when-you-copy-and-move-files-and-folders