DRAG DROP -
You have a Microsoft 365 E5 subscription.
You plan to implement Azure Sentinel to create incidents based on:
✑ Azure Active Directory (Azure AD) Identity Protection alerts
✑ Correlated events from the DeviceProcessEvents table
Which analytic rule types should you use for each incident type? To answer, drag the appropriate rule types to the correct incident types. Each rule type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: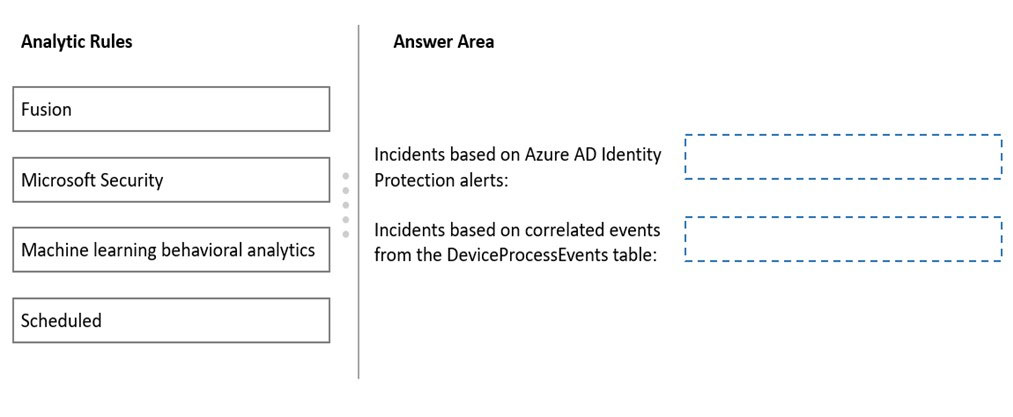
Answer:
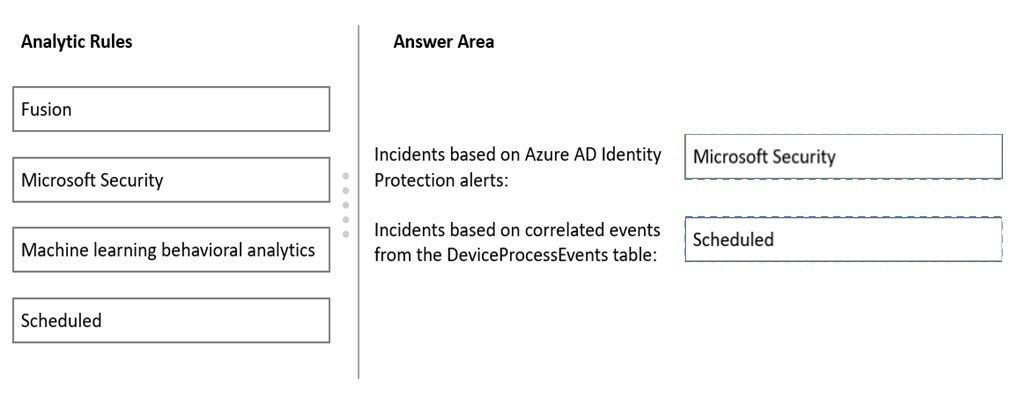
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts https://docs.microsoft.com/en-us/azure/sentinel/detect-threats-custom
You have a Microsoft 365 E5 subscription.
You need to use Attack simulation training to launch a credential harvest simulation.
For which Microsoft 365 workloads can you create a payload?
Answer:
A
Create a payload, select a payload type.
On the Select type page, the only value that you can currently select is Email.
Incorrect:
Not A, Not B, Not C: Payloads cannot be created for Microsoft Exchange Online.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulation-training-payloads
HOTSPOT -
You have a Microsoft Sentinel workspace that has an Azure Active Directory (Azure AD) connector and an Office 365 connector.
From the workspace, you plan to create an analytics rule that will be based on a custom query and will run a security playbook.
You need to ensure that you can add the security playbook and the custom query to the rule.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: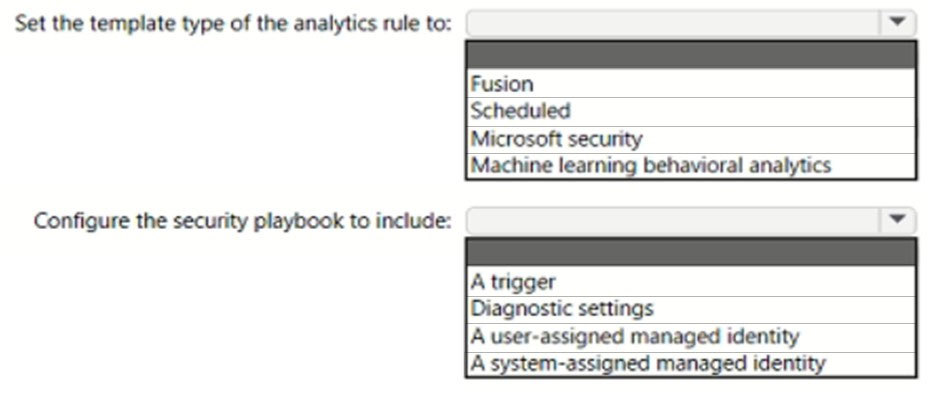
Answer:
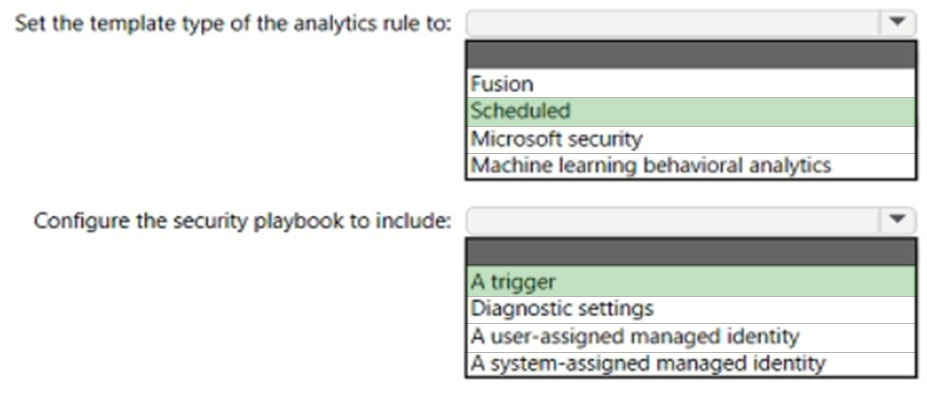
Box 1: Scheduled -
Create a custom analytics rule with a scheduled query
1. From the Microsoft Sentinel navigation menu, select Analytics.
2. In the action bar at the top, select +Create and select Scheduled query rule. This opens the Analytics rule wizard.
3. Etc.
Box 2: A trigger -
Use triggers and actions in Microsoft Sentinel playbooks.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/detect-threats-custom https://docs.microsoft.com/en-us/azure/sentinel/playbook-triggers-actions#microsoft-sentinel-triggers-summary
You have a Microsoft 365 Enterprise E5 subscription.
You use Microsoft Defender for Endpoint.
You need to integrate Microsoft Defender for Office 365 and Microsoft Defender for Endpoint.
Where should you configure the integration?
Answer:
D
To integrate Microsoft Defender for Office 365 with Microsoft Defender for Endpoint
Integrating Microsoft Defender for Office 365 with Microsoft Defender for Endpoint is set up in both Defender for Endpoint and Defender for Office 365.
1. Go to the Microsoft 365 Defender portal (https://security.microsoft.com) and sign in.
2. Go to Email & collaboration > Explorer.
3. On the Explorer page, in the upper right corner of the screen, select MDE Settings.
4. In the Microsoft Defender for Endpoint connection flyout that appears, turn on Connect to Microsoft Defender for Endpoint (Toggle on.) and then select Close.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/integrate-office-365-ti-with-mde?view=o365-worldwide
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Cloud Apps enabled.
You need to create an alert in Defender for Cloud Apps when source code is shared externally.
Which type of policy should you create?
Answer:
D
Detect externally shared source code
Detect when files that contain content that might be source code are shared publicly or are shared with users outside of your organization.
Prerequisites -
You must have at least one app connected using app connectors.
Steps -
1. On the Policies page, create a new File policy.
2. Select and apply the policy template Externally shared source code
3. Optional: Customize the list of file Extensions to match your organization's source code file extensions.
4. Optional: Set the Governance actions to be taken on files when a violation is detected. The governance actions available vary between services. For example, in Box, Send policy-match digest to file owner and Put in admin quarantine.
5. Select and apply the policy template
Reference:
https://docs.microsoft.com/en-us/defender-cloud-apps/policies-information-protection#detect-externally-shared-source-code
You have a Microsoft 365 E5 subscription and a hybrid Microsoft Exchange Server organization.
Each member of a group named Executive has an on-premises mailbox. Only the Executive group members have multi-factor authentication (MFA) enabled. Each member of a group named Research has a mailbox in Exchange Online.
You need to use Microsoft 365 Attack simulation training to model a spear-phishing attack that targets the Research group members. The email addresses that you intend to spoof belong to the Executive group members.
What should you do first?
Answer:
D
Module 6 - Lab 1 - Exercise 1 - Conduct a Spear phishing attack
Holly Dickson is concerned that some users in her organization may require education about phishing attacks. In this lab you will use the Microsoft 365 Attack simulator to determine your users' susceptibility to phishing attacks.
Task 1: Enable Mulit-factor authentication for Holly Dickson
1. On LON-CL1, Go to the Office 365 Security & Compliance center https://protection.office.com and login as Holly Dickson.
2. Click Threat management, and then click Attack simulator.
3. Notice the warning that you must enable multi-factor authentication (MFA). You are about to do a simulated attack and the system wants to confirm your credentials. This is a requirement of the attack simulator. Let's enable MFA for Holly Dickson.
4. Etc.
Reference:
https://microsoftlearning.github.io/MS-500-Microsoft-365-Security/Instructions/Labs/MS500T00/LAB_AK_06_Lab1_Ex1_Phishing_attack.html
DRAG DROP -
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint and contains a Windows 10 device named Device1.
You have a PowerShell script named script1 that collects forensic data and saves the results as a file on the device from which the script is run.
You receive a Microsoft Defender for Endpoint alert for suspicious activities on Device1.
You need to run script1 on Device1 and retrieve the output file of the script.
Which four actions should you perform in sequence in Microsoft 365 Defender portal? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Answer:
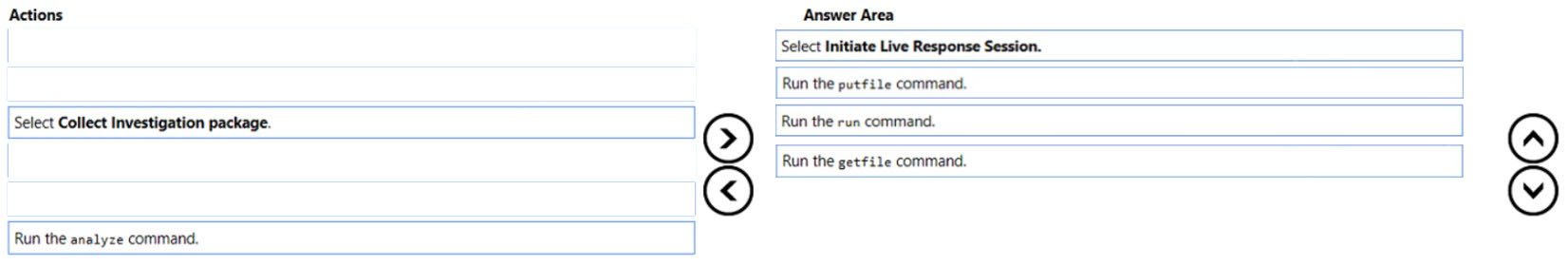
Step 1: Select Initiate Live Response Session.
Initiate a live response session on a device
1. Sign in to Microsoft 365 Defender portal.
2. Navigate to Endpoints > Device inventory and select a device to investigate. The devices page opens.
3. Launch the live response session by selecting Initiate live response session. A command console is displayed. Wait while the session connects to the device.
4. Use the built-in commands to do investigative work.
5. After completing your investigation, select Disconnect session, then select Confirm.
Note: Initiate live response Session
Live response is a capability that gives you instantaneous access to a device by using a remote shell connection. This gives you the power to do in-depth investigative work and take immediate response actions to promptly contain identified threats in real time.
Live response is designed to enhance investigations by enabling you to collect forensic data, run scripts, send suspicious entities for analysis, remediate threats, and proactively hunt for emerging threats.
Step 2: Run the putfile command -
putfile - Puts a file from the library to the device. Files are saved in a working folder and are deleted when the device restarts by default.
Step 3: Run the run command -
run - Runs a PowerShell script from the library on the device.
Step 4: Run the getfile command -
getfile <file_path> - Downloads a file.
For scenarios when you'd like get a file from a device you're investigating, you can use the getfile command. This allows you to save the file from the device for further investigation.
Incorrect:
* Select Collect Investigation package.
Collect investigation package from devices
As part of the investigation or response process, you can collect an investigation package from a device. By collecting the investigation package, you can identify the current state of the device and further understand the tools and techniques used by the attacker.
* Run the analyze command
Analyze - Analyses the entity with various incrimination engines to reach a verdict.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/live-response https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/respond-machine-alerts
HOTSPOT -
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com.
OneDrive stores files that are shared with external users. The files are configured as shown in the following table.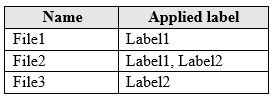
You create a data loss prevention (DLP) policy that applies to the content stored in OneDrive accounts. The policy contains the following three rules:
Rule1:
✑ Conditions: Label1, Detect content that's shared with people outside my organization
✑ Actions: Restrict access to the content for external users
✑ User notifications: Notify the user who last modified the content
✑ User overrides: On
✑ Priority: 0
Rule2:
✑ Conditions: Label1 or Label2
✑ Actions: Restrict access to the content
✑ Priority: 1
Rule3:
✑ Conditions: Label2, Detect content that's shared with people outside my organization
✑ Actions: Restrict access to the content for external users
✑ User notifications: Notify the user who last modified the content
✑ User overrides: On
✑ Priority: 2
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
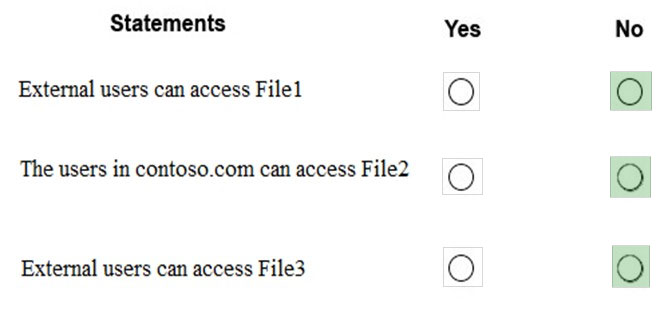
When content is evaluated against rules, the rules are processed in priority order. If content matches multiple rules, the rules are processed in priority order and the most restrictive action is enforced. In this scenario rule 2 is the most restrictive.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/data-loss-prevention-policies?view=o365-worldwide
You have a Microsoft 365 subscription for a company named Contoso, Ltd. All data is in Microsoft 365.
Contoso works with a partner company named Litware, Inc. Litware has a Microsoft 365 subscription. Microsoft OneDrive has the default settings.
You need to allow users at Contoso to share files from Microsoft OneDrive to specific users at Litware.
Which two actions should you perform from the OneDrive admin center? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
AE
You have a Microsoft 365 subscription.
Some users access Microsoft SharePoint Online from unmanaged devices.
You need to prevent the users from downloading, printing, and syncing files.
What should you do?
Answer:
A
As a SharePoint or global admin in Microsoft 365, you can use the Access control page of the SharePoint admin center or the Set-SPOTenant -
ConditionalAccessPolicy cmdlet to block or limit access to SharePoint and OneDrive content from unmanaged devices.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. Run the Set-SPOTenant cmdlet and specify the
-ConditionalAccessPolicy parameter.
2. From the SharePoint admin center, configure the Access control settings.
Other incorrect answer options you may see on the exam include the following:
1. From the Microsoft Azure portal, create an Azure Active Directory (Azure AD) Identity Protection user risk policy.
2. From the Microsoft Azure portal, create an Azure Active Directory (Azure AD) conditional access policy
Reference:
https://docs.microsoft.com/en-us/powershell/module/sharepoint-online/set-spotenant?view=sharepoint-ps https://docs.microsoft.com/en-us/sharepoint/control-access-from-unmanaged-devices