DRAG DROP -
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Microsoft Defender for Endpoint.
You create a Microsoft Defender for Endpoint device group named DeviceGroup1.
You need to enable delegation for the security settings of the computers in DeviceGroup1.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: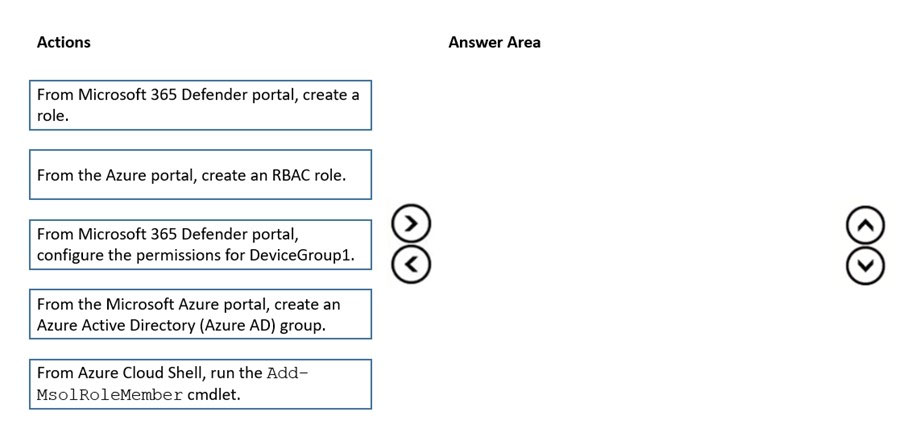
Answer:
You have a hybrid Microsoft Exchange Server organization. All users have Microsoft 365 E5 licenses.
You plan to implement a Microsoft Defender for Office 365 anti-phishing policy.
You need to enable mailbox intelligence for all users.
What should you do first?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/set-up-anti-phishing-policies
HOTSPOT -
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
Four Windows 10 devices are joined to the tenant as shown in the following table.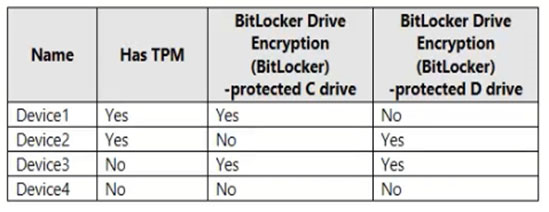
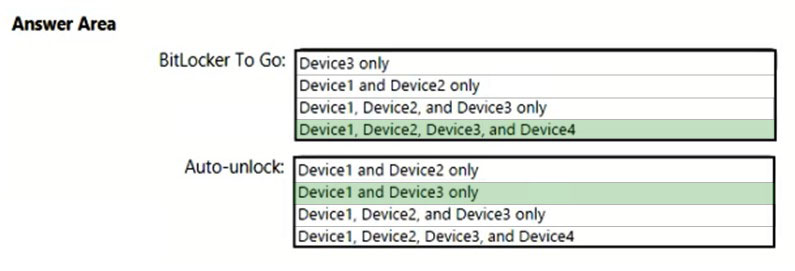
On which devices can you use BitLocker To Go and on which devices can you turn on auto-unlock? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: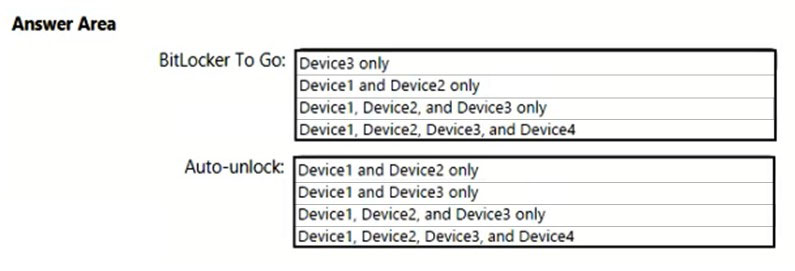
Answer:
HOTSPOT -
You have a Microsoft 365 subscription that contains a user named User1.
You enroll devices in Microsoft Intune as shown in the following table.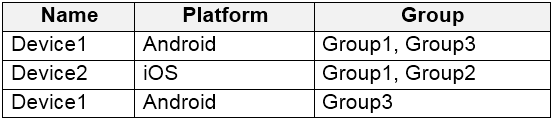
Each device has two line-of-business apps named App1 and App2 installed.
You create application control policies targeted to all the app types in Microsoft Endpoint Manager as shown in the following table.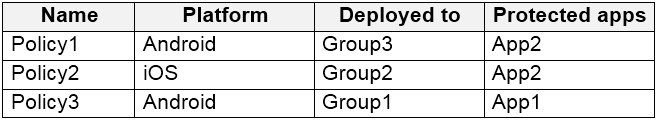
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: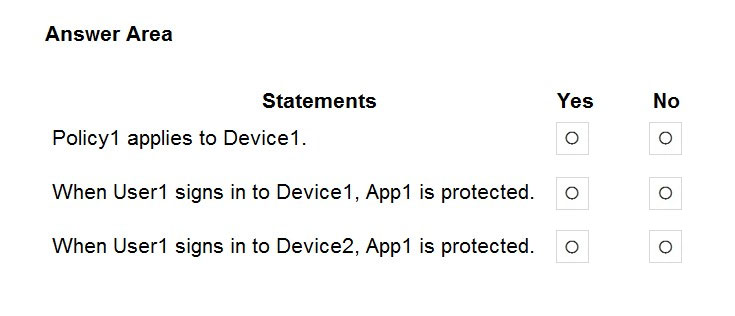
Answer:
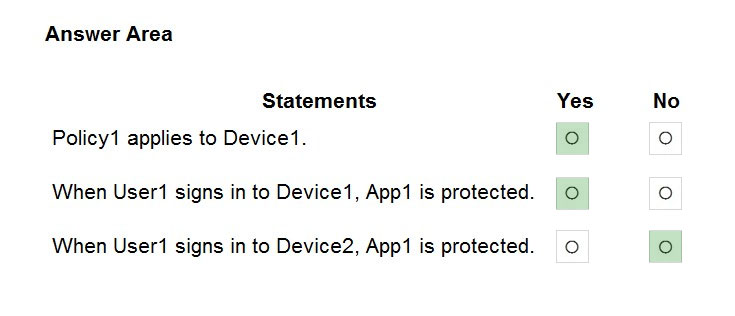
Box 1: Yes -
Device1 is an Android device in Group3 (and Group1). Policy1 applies to Android devices in Group3. Therefore, Policy1 does apply to Device1.
Box 2: Yes -
Policy3 protects App1 for Android devices in Group1. Device1 is in Group1 (and Group3). Therefore, App1 is protected on Device1.
Box 3: No -
Device2 is an iOS device in Group1 and Group2. Policy2 applies to iOS devices in Group2. However, Policy2 only protects App2. It does not protect App1.
Policy3 applies to Group1 and protects App1. However, Policy3 only applies to Android devices in Group1. It does not apply to iOS devices. Therefore, Policy3 does not apply to Device2 so App1 is not protected on Device2.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.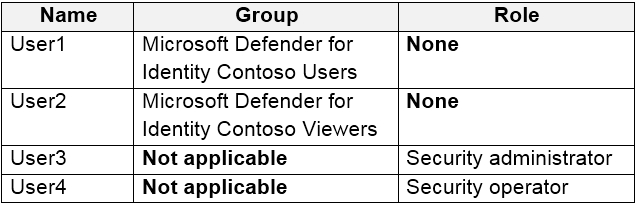
You discover that several security alerts are visible from the Microsoft Defender for Identity portal.
You need to identify which users in contoso.com can close the security alerts.
Which users should you identify?
Answer:
D
You have a Microsoft 365 E5 subscription that contains 1,000 Windows 10 devices. The devices are onboarded to Microsoft Defender for Endpoint.
You need to view a consolidated list of the common vulnerabilities and exposures (CVE) that affect the devices. The solution must minimize administrative effort.
Which Threat & Vulnerability Management page should you use?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/tvm-weaknesses?view=o365-worldwide
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and an Office 365 connector.
From the workspace, you plan to create a scheduled query rule that will use a custom query. The rule will be used to generate alerts when inbound access to
Office 365 from specific user accounts is detected.
You need to ensure that when multiple alerts are generated by the rule, the alerts are consolidated as a single incident per user account.
What should you do?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/map-data-fields-to-entities
DRAG DROP -
You have an Azure Sentinel workspace that has an Office 365 connector.
You are threat hunting events that have suspicious traffic from specific IP addresses.
You need to save the events and the relevant query results for future reference.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: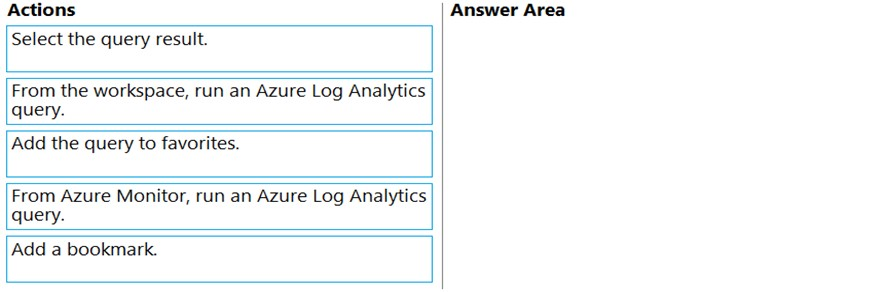
Answer:
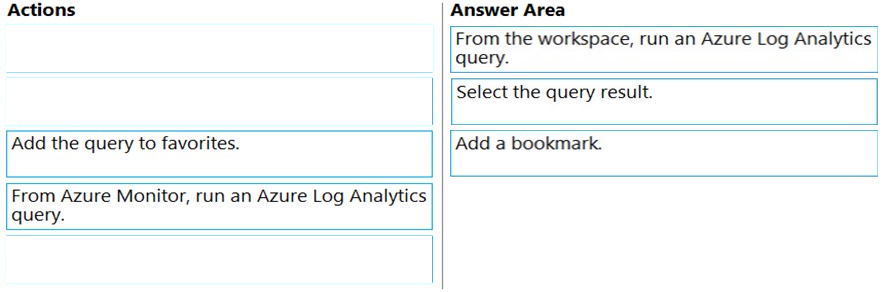
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/bookmarks
You create an Azure Sentinel workspace.
You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD).
In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.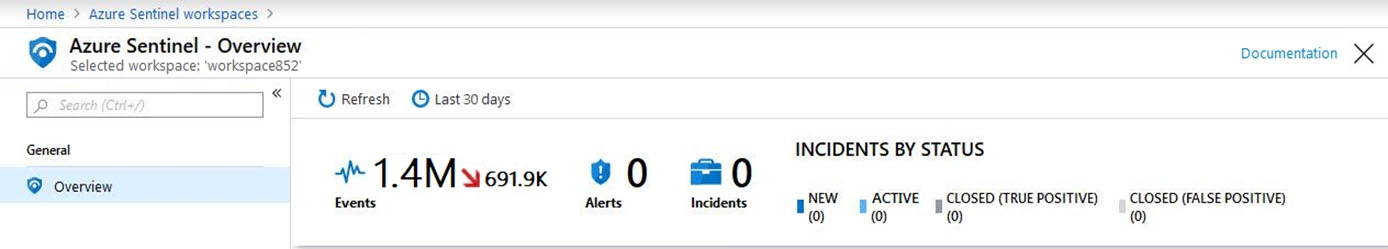
In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace.
What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/detect-threats-custom
You have a Microsoft 365 E5 subscription that has Microsoft 365 Defender enabled.
You plan to deploy a third-party app named App1 that will receive alert data from Microsoft 365 Defender.
Which format will Microsoft 365 Defender use to send the alert data to App1?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/alerts?view=o365-worldwide