HOTSPOT -
You have a Microsoft 365 tenant.
You create an attack surface reduction policy that uses an application control profile as shown in the following exhibit.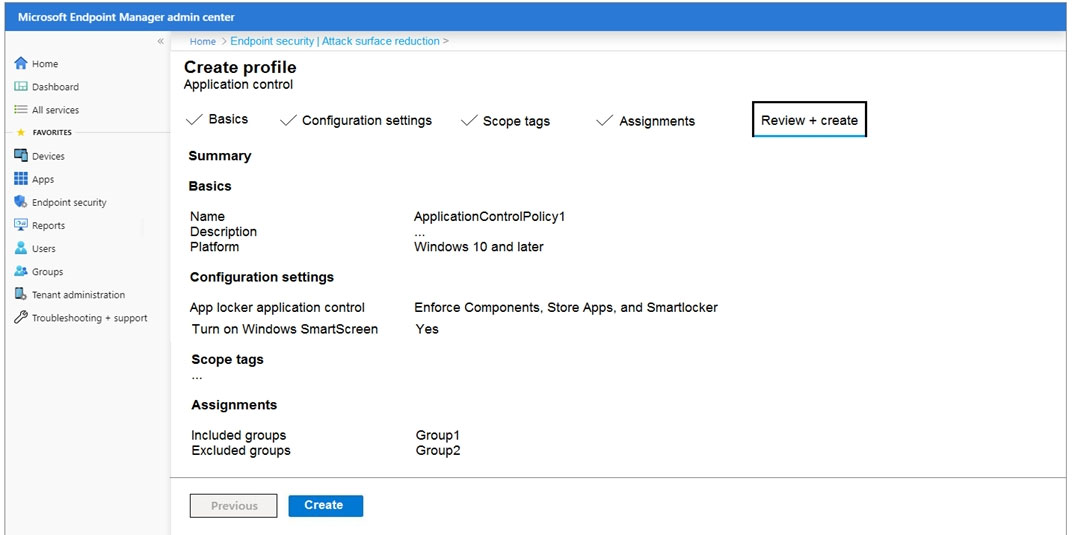
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: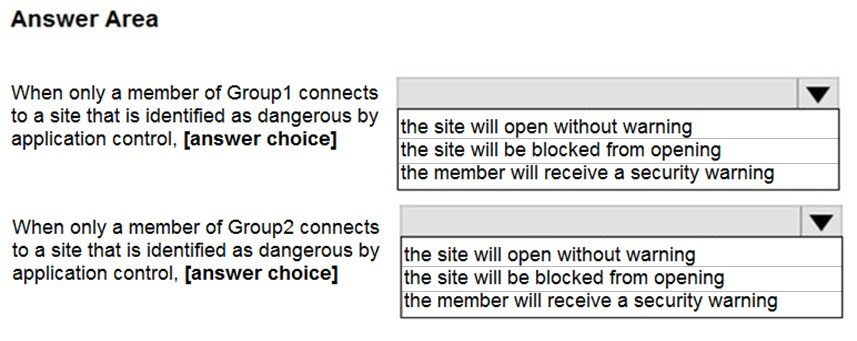
Answer:
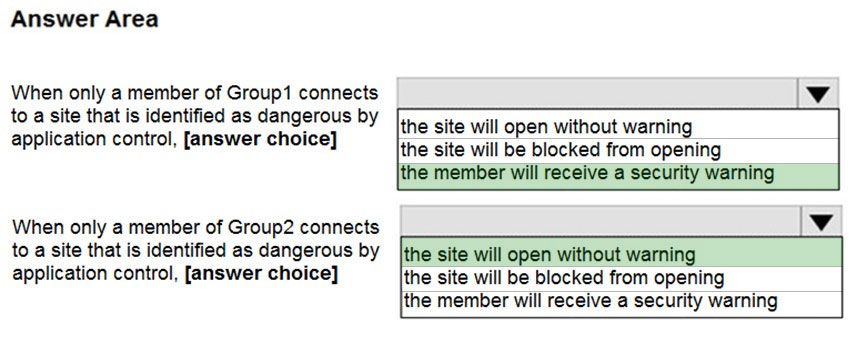
Box 1: the member will receive a security warning.
Group1 is included in the policy so SmartScreen will be enabled. SmartScreen will display a warning.
Box 2: the site will open without warning.
Group2 is excluded from the policy so SmartScreen will not be enabled. Therefore, no warning will be displayed.
DRAG DROP -
You have an on-premises Hyper-V infrastructure that contains the following:
✑ An Active Directory domain
✑ A domain controller named Server1
✑ A member server named Server2
A security policy specifies that Server1 cannot connect to the Internet. Server2 can connect to the Internet.
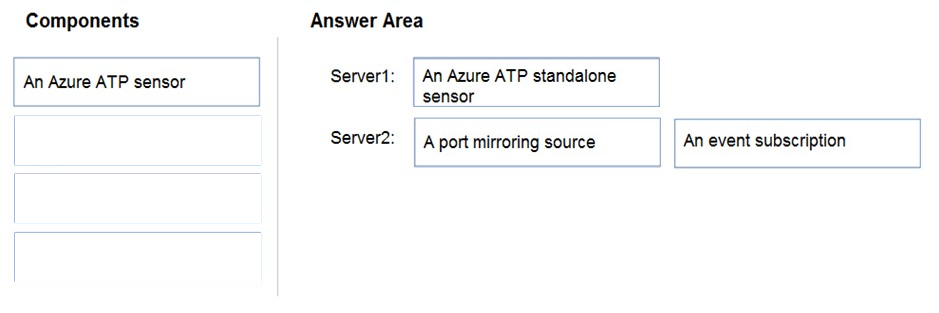
You need to implement Azure Advanced Threat Protection (ATP) to monitor the security of the domain.
What should you configure on each server? To answer, drag the appropriate components to the correct servers. Each component may only be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: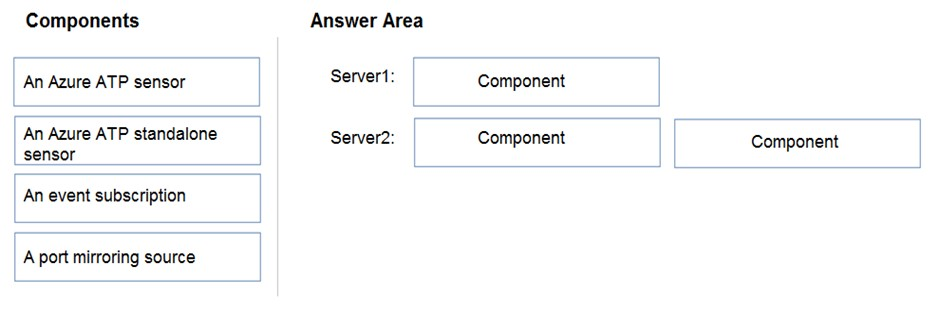
Answer:
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.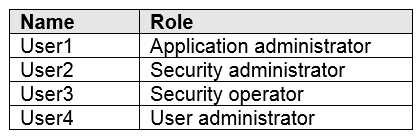
You need to identify which user can enable Microsoft Defender for Endpoint roles.
Which user should you identify?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/rbac
You have an Azure Sentinel workspace.
You need to manage incidents based on alerts generated by Microsoft Cloud App Security.
What should you do first?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/siem-sentinel
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Microsoft Defender for Identity by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
Answer:
A
Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
✑ Integrate SIEM and Microsoft Defender for Identity
✑ Configure Event Forwarding on the domain controllers
Other incorrect answer options you may see on the exam include the following:
✑ Configure Microsoft Defender for Identity notifications
✑ Modify the Domain synchronizer candidate settings on the Microsoft Defender for Identity sensors
✑ Configure auditing in the Microsoft 365 Defender portal
Reference:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/configure-event-forwarding
Several users in your Microsoft 365 subscription report that they received an email message without the attachment.
You need to review the attachments that were removed from the messages.
Which two tools can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
AD
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/manage-quarantined-messages-and-files
You have a hybrid Microsoft 365 deployment that contains the Windows 10 devices shown in the following table.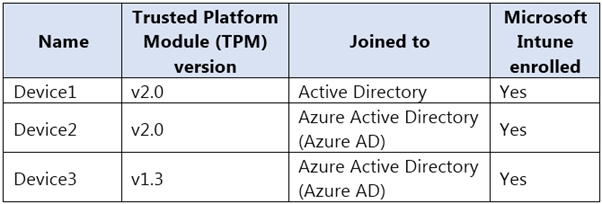
You assign a Microsoft Endpoint Manager disk encryption policy that automatically and silently enables BitLocker Drive Encryption (BitLocker) on all the devices.
Which devices will have BitLocker enabled?
Answer:
B
To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0.
Incorrect Answers:
A: Device1 is not Azure AD Joined or Hybrid Azure AD Joined, and the TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must be Azure
AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0.
C: Device1 is not Azure AD Joined or Hybrid Azure AD Joined. To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined.
D: The TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must contain TPM (Trusted Platform Module) 2.0.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/encrypt-devices
HOTSPOT -
You have an Azure Sentinel workspace.
You configure a rule to generate Azure Sentinel alerts when Azure Active Directory (Azure AD) Identity Protection detects risky sign-ins. You develop an Azure
Logic Apps solution to contact users and verify whether reported risky sign-ins are legitimate.
You need to configure the workspace to meet the following requirements:
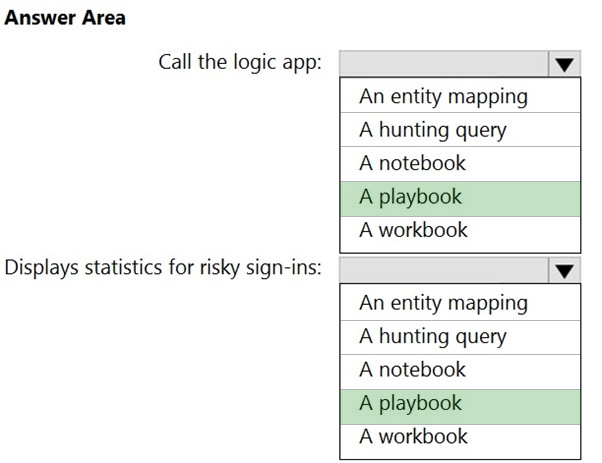
✑ Call the Azure logic app when an alert is triggered for a risky sign-in.
✑ To the Azure Sentinel portal, add a custom dashboard that displays statistics for risky sign-ins that are detected and resolved.
What should you configure in Azure Sentinel to meet each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: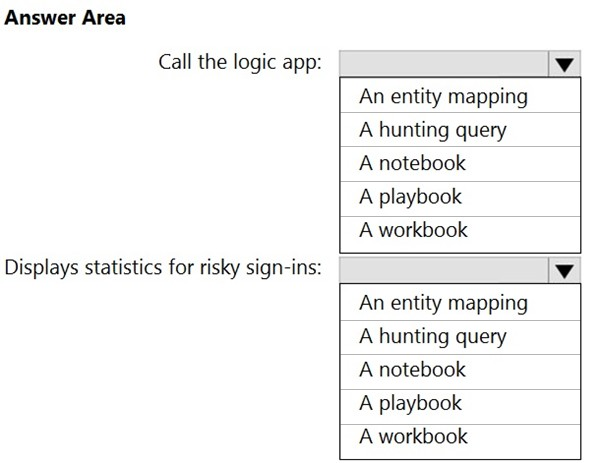
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
DRAG DROP -
You have an Azure subscription and a Microsoft 365 subscription.
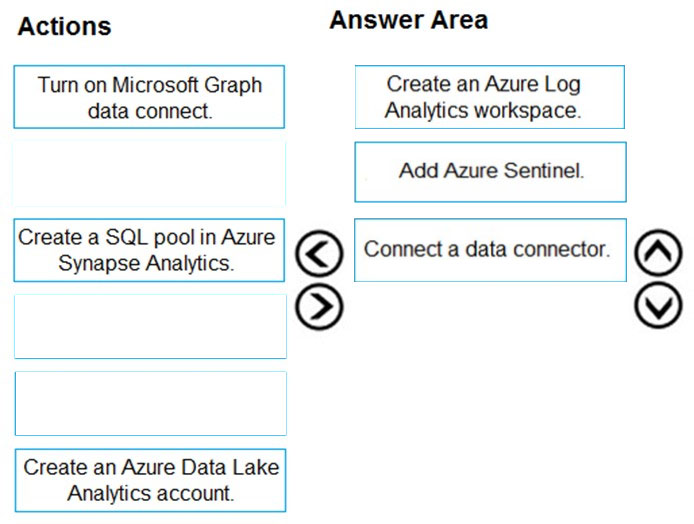
You need to perform the following actions:
✑ Deploy Microsoft Sentinel.
✑ Collect the Office 365 activity log by using Microsoft Sentinel.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/quickstart-onboard https://docs.microsoft.com/en-us/azure/sentinel/connect-office-365
You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager.
You need to enable Microsoft Defender Exploit Guard (Microsoft Defender EG) on the devices.
Which type of device configuration profile should you use?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-windows-10