HOTSPOT -
You have a Microsoft 365 E5 subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com.
Azure AD Identity Protection alerts for contoso.com are configured as shown in the following exhibit.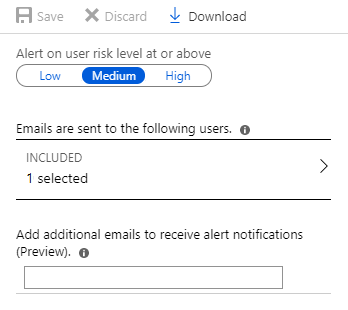
A user named User1 is configured to receive alerts from Azure AD Identity Protection.
You create users in contoso.com as shown in the following table.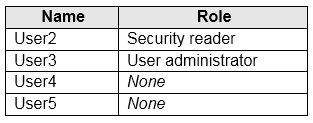
The users perform the sign-ins shown in the following table.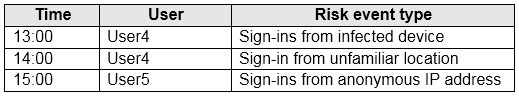
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
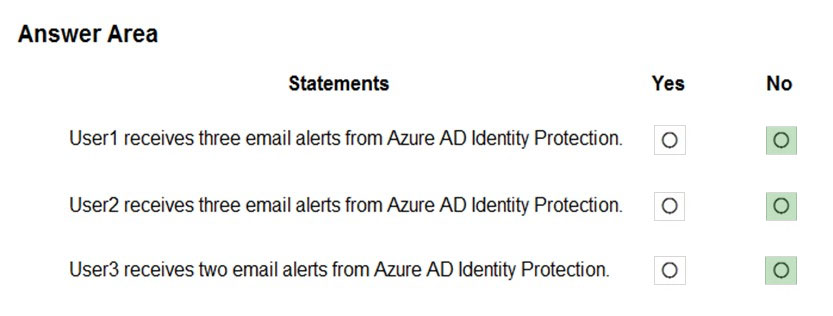
Box 1: No -
User1 will receive the two alerts classified as medium or higher.
Sign-ins from infected device is classified as low. This risk detection identifies IP addresses, not user devices. If several devices are behind a single IP address, and only some are controlled by a bot network, sign-ins from other devices my trigger this event unnecessarily, which is why this risk detection is classified as
Low.
Box 2: No -
User2 will receive the two alerts classified as medium or higher.
Email alerts are sent to all global admins, security admins and security readers
Sign-ins from infected device is classified as low. This risk detection identifies IP addresses, not user devices. If several devices are behind a single IP address, and only some are controlled by a bot network, sign-ins from other devices my trigger this event unnecessarily, which is why this risk detection is classified as
Low.
Box 3: No -
User3 will not receive alters.
Email alerts are sent to all global admins, security admins and security readers.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/overview-identity-protection https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-policies
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector.
You need to assign built-in role-based access control (RBAC) roles to achieve the following tasks:
✑ Create and run playbooks.
✑ Manage incidents.
The solution must use the principle of least privilege.
Which two roles should you assign? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
DE
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/roles
Your company uses Microsoft Azure Advanced Threat Protection (ATP).
You enable the delayed deployment of updates for an Azure ATP sensor named Sensor1.
How long after the Azure ATP cloud service is updated will Sensor1 be updated?
Answer:
B
Note: The delay period was 24 hours. In ATP release 2.62, the 24 hour delay period has been increased to 72 hours.
DRAG DROP -
You have a Microsoft 365 E5 subscription. All users use Microsoft Exchange Online.
Microsoft 365 is configured to use the default policy settings without any custom rules.
You manage message hygiene.
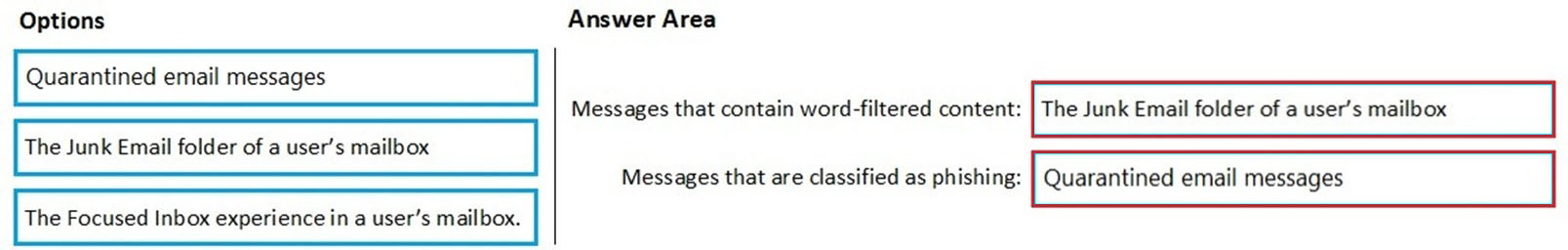
Where are suspicious email messages placed by default? To answer, drag the appropriate location to the correct message types. Each option may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place: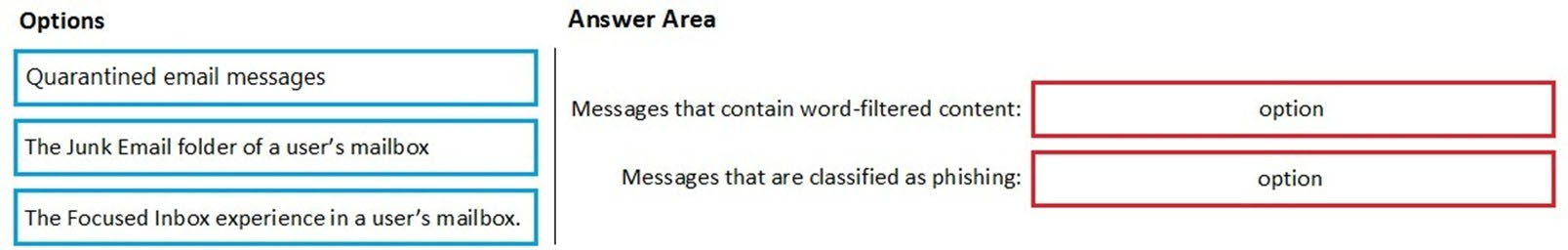
Answer:
You have a Microsoft 365 subscription.
You create a Microsoft Defender for Office 365 safe attachments policy.
You need to configure the retention duration for the attachments in quarantine.
Which type of threat management policy should you create?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/manage-quarantined-messages-and-files#BKMK_ModQuarantineTime
Your company has 500 computers.
You plan to protect the computers by using Microsoft Defender for Endpoint. Twenty of the computers belong to company executives.
You need to recommend a remediation solution that meets the following requirements:
✑ Microsoft Defender for Endpoint administrators must manually approve all remediation for the executives
✑ Remediation must occur automatically for all other users
What should you recommend doing from Microsoft Defender Security Center?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/machine-groups-windows-defender-advanced-threat-protection
You have a Microsoft 365 Enterprise E5 subscription.
You use Microsoft Defender for Endpoint.
You need to integrate Microsoft Defender for Office 365 and Microsoft Defender for Endpoint.
Where should you configure the integration?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/integrate-office-365-ti-with-mde?view=o365-worldwide
Your network contains an on-premises Active Directory domain. The domain contains servers that run Windows Server and have advanced auditing enabled.
The security logs of the servers are collected by using a third-party SIEM solution.
You purchase a Microsoft 365 subscription and plan to deploy Microsoft Defender for Identity by using standalone sensors.
You need to ensure that you can detect when sensitive groups are modified and when malicious services are created.
What should you do?
Answer:
D
Note:
There are several versions of this question in the exam. The questions in the exam have two different correct answers:
✑ Integrate SIEM and Microsoft Defender for Identity
Configure Event Forwarding on the domain controllers
Other incorrect answer options you may see on the exam include the following:
✑ Configure Microsoft Defender for Identity notifications
✑ Modify the Domain synchronizer candidate settings on the Microsoft Defender for Identity sensors
✑ Enable the Audit account management Group Policy setting for the servers
✑ Configure auditing in the Microsoft 365 Defender portal
Reference:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/configure-event-forwarding
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector.
You need to use a Fusion rule template to detect multistage attacks in which users sign in by using compromised credentials, and then delete multiple files from
Microsoft OneDrive.
Based on the Fusion rule template, you create an active rule that has the default settings.
What should you do next?
Answer:
B
Reference:
https://docs.microsoft.com/en-gb/azure/azure-monitor/platform/workbooks-overview
You have a Microsoft 365 subscription that uses a default domain name of fabrikam.com.
You create a safe links policy, as shown in the following exhibit.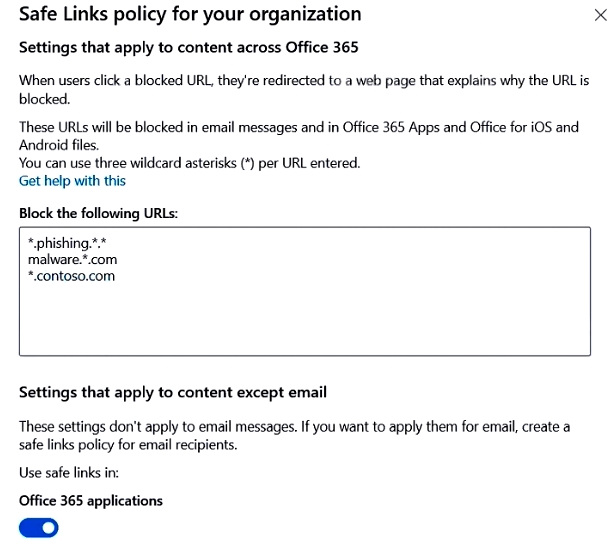
Which URL can a user safely access from Microsoft Word Online?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/configure-global-settings-for-safe-links