HOTSPOT -
You have a Microsoft 365 E5 subscription.
Users and device objects are added and removed daily. Users in the sales department frequently change their device.
You need to create three following groups: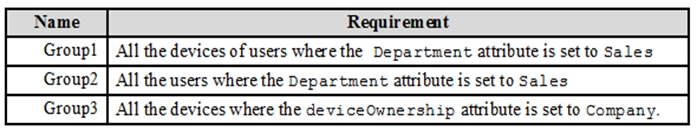
The solution must minimize administrative effort.
What is the minimum number of groups you should create for each type of membership? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
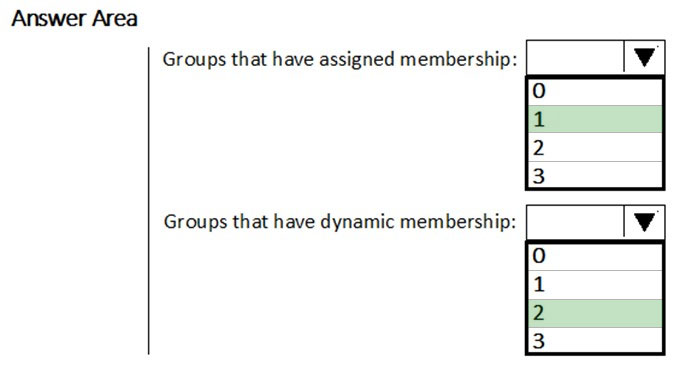
Group 1 has to be assigned because you can't create a device group based on the device owners' attributes.
Group 2 can be dynamic because a user does have a department attribute.
Group 3 can be dynamic because a device does have a deviceownership attribute.
Your company has a main office and a Microsoft 365 subscription.
You need to enforce Microsoft Azure Multi-Factor Authentication (MFA) by using conditional access for all users who are NOT physically present in the office.
What should you include in the configuration?
Answer:
C
References:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
HOTSPOT -
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.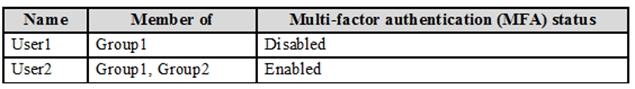
You create and enforce an Azure AD Identity Protection user risk policy that has the following settings:
✑ Assignments: Include Group1, Exclude Group2
✑ Conditions: User risk of Low and above
✑ Access: Allow access, Require password change
You need to identify how the policy affects User1 and User2.
What occurs when User1 and User2 sign in from an unfamiliar location? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: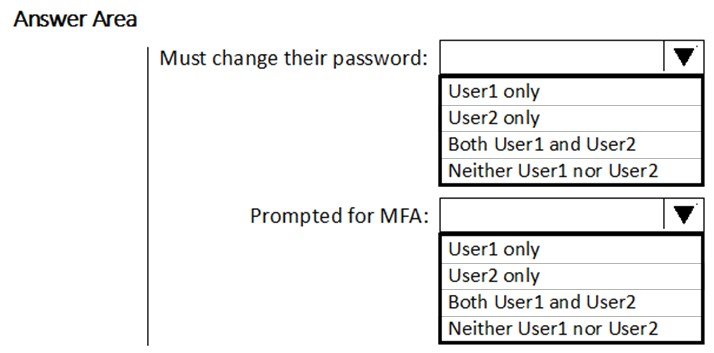
Answer:
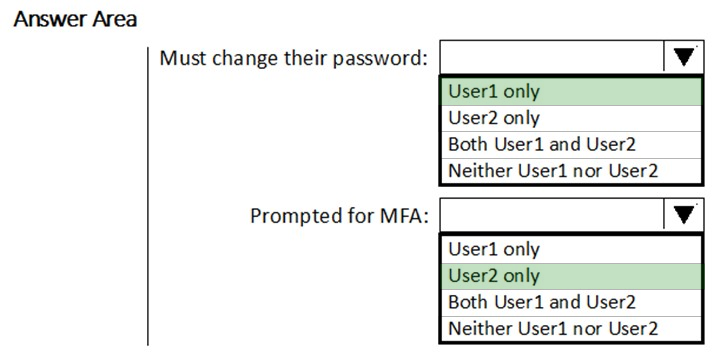
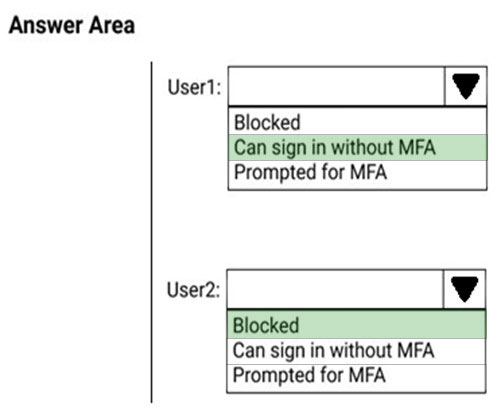
Box 1: User1 only -
The Azure AD Identity Protection user risk policy is excluded from Group2. Exclusion overrides inclusion. Therefore, the policy will not affect User2. Thus, only
User 1 needs to change the Password.
Box 2: User2 only -
MFA will be triggered for User 2.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-risk-policies
HOTSPOT -
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.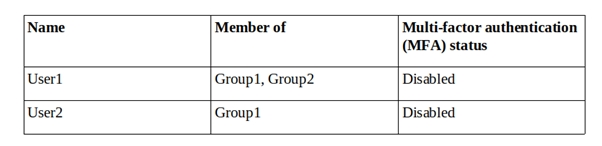
You create and enforce an Azure AD Identity Protection sign-in risk policy that has the following settings:
✑ Assignments: Include Group1, Exclude Group2
✑ Conditions: Sign-in risk of Low and above
✑ Access: Allow access, Require multi-factor authentication
You need to identify how the policy affects User1 and User2.
What occurs when each user signs in from an anonymous IP address? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: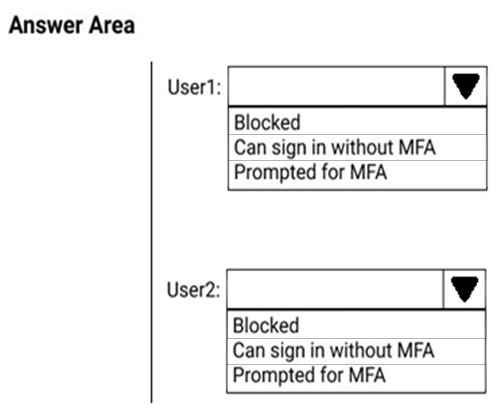
Answer:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
Solution: You use the Security event log on Server1.
Does that meet the goal?
Answer:
B
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
Solution: You use the Directory Service event log on Server1.
Does that meet the goal?
Answer:
B
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
Solution: You use the System event log on Server1.
Does that meet the goal?
Answer:
B
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises Active Directory domain named contoso.com.
You install and run Azure AD Connect on a server named Server1 that runs Windows Server.
You need to view Azure AD Connect events.
Solution: You use the Application event log on Server1.
Does that meet the goal?
Answer:
A
References:
https://support.pingidentity.com/s/article/PingOne-How-to-troubleshoot-an-AD-Connect-Instance
You have a Microsoft 365 E5 subscription.
Some users are required to use an authenticator app to access Microsoft SharePoint Online.
You need to view which users have used an authenticator app to access SharePoint Online. The solution must minimize costs.
What should you do?
Answer:
D
The user sign-ins report provides information on the sign-in pattern of a user, the number of users that have signed in over a week, and the status of these sign- ins.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. From the Enterprise applications blade of the Azure Active Directory admin center, view the sign-ins.
2. From the Azure Active Directory admin center, view the sign-ins.
Other incorrect answer options you may see on the exam include the following:
1. From the Enterprise applications blade of the Azure Active Directory admin center, view the audit logs.
2. From the Azure Active Directory admin center, view the audit logs.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-sign-ins
HOTSPOT -
You have a Microsoft 365 subscription that contains the users shown in the following table.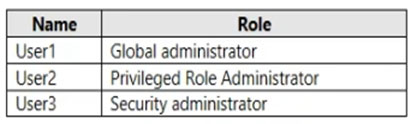
You implement Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
From PIM, you review the Application Administrator role and discover the users shown in the following table.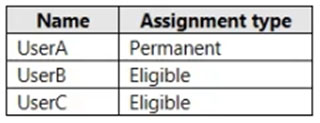
The Application Administrator role is configured to use the following settings in PIM:
✑ Activation maximum duration (hours): 1 hour
✑ Require justification on activation: No
✑ Require ticket information on activation: No
✑ On activation, require Azure MFA: No
✑ Require approval to activate: Yes
✑ Approvers: None
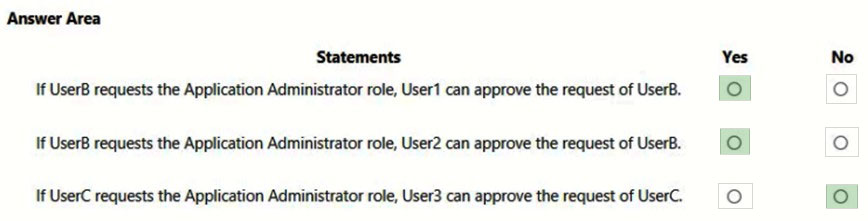
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: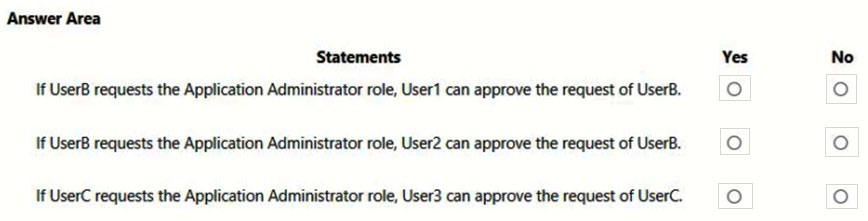
Answer: