SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab.
But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password -
Use the following login credentials as needed:
To enter your password, place your cursor in the Enter password box and click on the password below.
Username: Contoso/Administrator -
Password: Passw0rd!
The following information is for technical support purposes only:
Lab Instance: 11145882 -
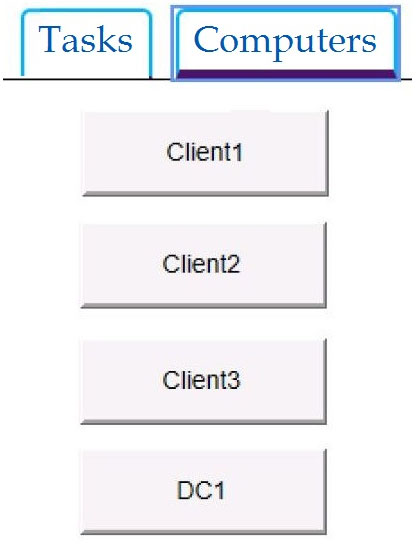
You have already prepared Client1 for remote management.
You need to forward all events from the Application event log on Client1 to DC1.
To complete this task, sign in to the required computer or computers.
Answer:
See explanation below.
Configuring the event source computer
1. Run the following command from an elevated privilege command prompt on the Windows Server domain controller to configure Windows Remote Management: winrm qc -q
2. Start group policy by running the following command:
%SYSTEMROOT%\System32\gpedit.msc
3. Under the Computer Configuration node, expand the Administrative Templates node, then expand the Windows Components node, then select the Event
Forwarding node.
4. Right-click the SubscriptionManager setting, and select Properties. Enable the SubscriptionManager setting, and click the Show button to add a server address to the setting. Add at least one setting that specifies the event collector computer. The SubscriptionManager Properties window contains an Explain tab that describes the syntax for the setting.
5. After the SubscriptionManager setting has been added, run the following command to ensure the policy is applied: gpupdate /force
Configuring the event collector computer
1. Run the following command from an elevated privilege command prompt on the Windows Server domain controller to configure Windows Remote Management: winrm qc -q
2. Run the following command to configure the Event Collector service: wecutil qc /q
3. Create a source initiated subscription. This can either be done programmatically, by using the Event Viewer, or by using Wecutil.exe. If you use Wecutil.exe, you must create an event subscription XML file and use the following command: wecutil cs configurationFile.xml
Reference:
https://docs.microsoft.com/en-us/windows/win32/wec/setting-up-a-source-initiated-subscription#forwarding-the-security-log
Your company has a wireless access point that uses WPA2-Enterprise.
You need to configure a computer to connect to the wireless access point.
What should you do first?
Answer:
B
Reference:
https://support.microsoft.com/en-za/help/17137/windows-setting-up-wireless-network
A user named User1 has a computer named Computer1 that runs Windows 10.
User1 connects to a Microsoft Azure virtual machine named VM1 by using Remote Desktop.
User1 creates a VPN connection named VPN1 to connect to a partner organization.
When the VPN1 connection is established, User1 cannot connect to VM1. When User1 disconnects from VPN1, the user can connect to VM1.
You need to ensure that User1 can connect to VM1 while connected to VPN1.
What should you do?
Answer:
B
Reference:
https://www.stevejenkins.com/blog/2010/01/using-the-local-default-gateway-with-a-windows-vpn-connection/
Your network contains an Active Directory domain. The domain contains a user named Admin1. All computers run Windows 10.
You enable Windows PowerShell remoting on the computers.
You need to ensure that Admin1 can establish remote PowerShell connections to the computers. The solution must use the principle of least privilege.
To which group should you add Admin1?
Answer:
D
Reference:
https://4sysops.com/wiki/enable-powershell-remoting/
You have 200 computers that run Windows 10 and are joined to an Active Directory domain.
You need to enable Windows Remote Management (WinRM) on all the computers by using Group Policy.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
ACD
Reference:
http://www.mustbegeek.com/how-to-enable-winrm-via-group-policy/
Your network contains an Active Directory domain. The domain contains the objects shown in the following table.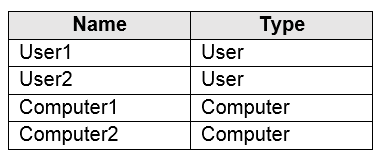
The domain is configured to store BitLocker Drive Encryption (BitLocker) recovery passwords.
User1 encrypts an external disk on Computer1 by using BitLocker to Go.
User2 moves the external disk to Computer2 and unlocks the disk.
You need to view the BitLocker recovery password.
Which objects are used to store the recovery password?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-and-adds-faq
A user has a computer that runs Windows 10.
When the user connects the computer to the corporate network, the user cannot access the internal corporate servers. The user can access servers on the
Internet.
You run the ipconfig command and receive the following output.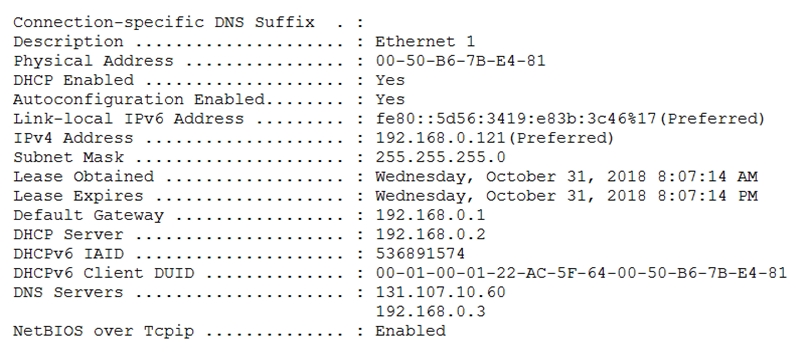
You send a ping request and successfully ping the default gateway, the DNS servers, and the DHCP server.
Which configuration on the computer causes the issue?
Answer:
A
You have a computer named Computer1 that runs Windows 10. Computer1 is joined to an Active Directory domain named adatum.com. The domain contains two groups named Group1 and Group2.
Computer1 contains a folder named C:\Folder1 that has the file permissions shown in the following table.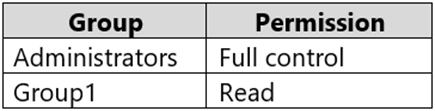
You need to share C:\Folder1. The solution must ensure that the members of Group2 can access all the files in the share.
What should you do?
Answer:
D
Reference:
https://techgenix.com/net-share-command-30/
You are troubleshooting the network connectivity of a computer that runs Windows 10. The computer is connected physically to the network but rejects network traffic from an external source.
You need to reinstall the TCP/IP stack on the computer.
What should you run?
Answer:
A
Reference:
https://howtofix.guide/reset-tcp-ip/
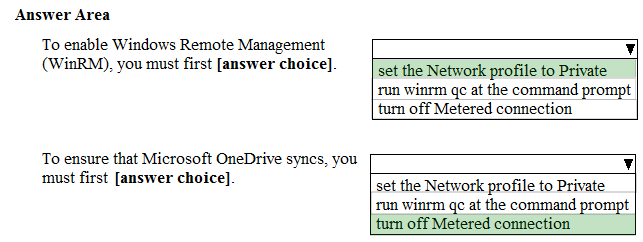
HOTSPOT -
You have a computer that runs Windows 10.
From the Settings app, you view the connection properties shown in the following exhibit.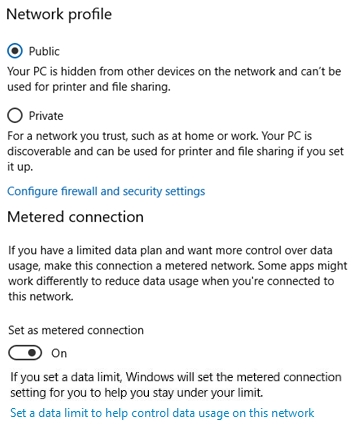
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer: