How is data sent out to the attacker during a DNS tunneling attack?
A
Reference:
https://www.infoblox.com/glossary/dns-tunneling/
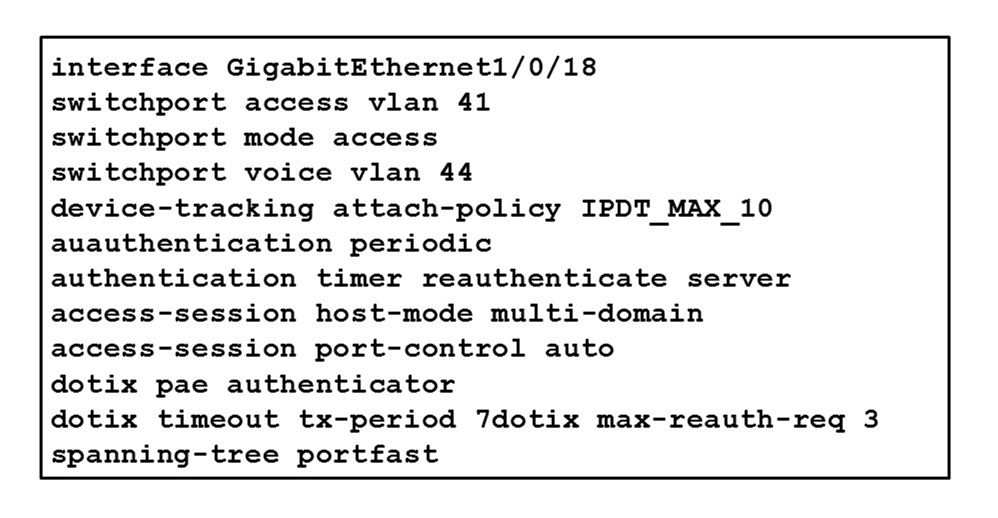
Refer to the exhibit. A Cisco ISE administrator adds a new switch to an 802. 1X deployment and has difficulty with some endpoints gaining access. Most PCs and
IP phones can connect and authenticate using their machine certificate credentials; however, printers and video cameras cannot. Based on the interface configuration provided, what must be done to get these devices onto the network using Cisco ISE for authentication and authorization while maintaining security controls?
D
Cisco SensorBase gathers threat information from a variety of Cisco products and services and performs analytics to find pattern on threats. Which term describes this process?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/security/security_management/cisco_security_manager/security_manager/414/user/guide/CSMUserGuide/ ipsglobe.html
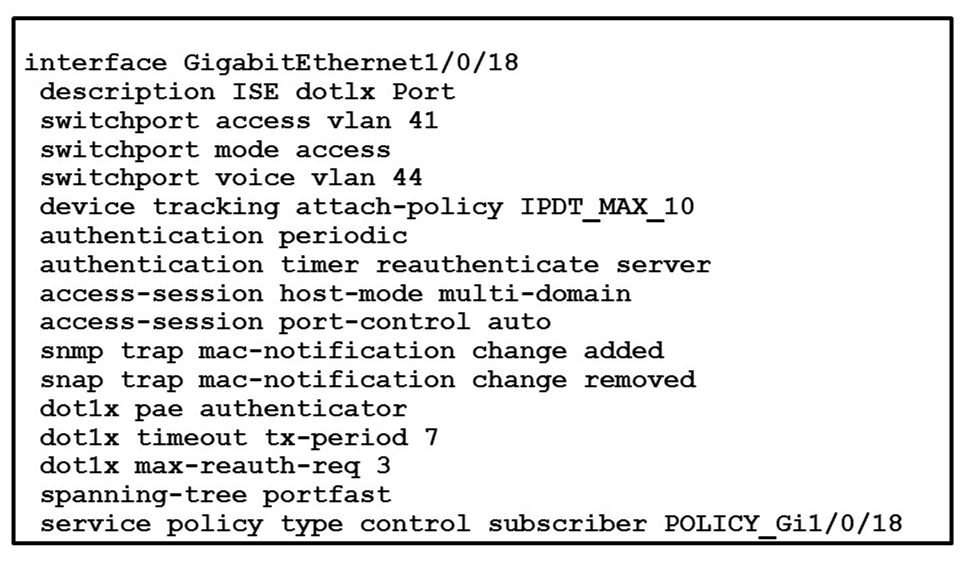
Refer to the exhibit. What will occur when this device tries to connect to the port?
D
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
C
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view of activity?
D
Reference:
https://developer.cisco.com/docs/ios-xe/#!streaming-telemetry-quick-start-guide
What two mechanisms are used to redirect users to a web portal to authenticate to ISE for guest services? (Choose two.)
BE
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-2/admin_guide/b_ise_admin_guide_22/b_ise_admin_guide_22_chapter_01110.html
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
C
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the corporate network. The endpoints must have the corporate antivirus application installed and be running the latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the network?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect46/administration/guide/b_AnyConnect_Administrator_Guide_4-6/ configure-posture.html
Using Cisco Cognitive Threat Analytics, which platform automatically blocks risky sites, and test unknown sites for hidden advanced threats before allowing users to click them?
C