How does DNS Tunneling exfiltrate data?
A
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
A
A user has a device in the network that is receiving too many connection requests from multiple machines. Which type of attack is the device undergoing?
A
Which two preventive measures are used to control cross-site scripting? (Choose two.)
BD
Which threat involves software being used to gain unauthorized access to a computer system?
D
Which two capabilities does TAXII support? (Choose two.)
AB
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two.)
CE
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_vpnav/configuration/15-mt/sec-vpn-availability-15-mt-book/sec-state-fail-ipsec.html
Which algorithm provides encryption and authentication for data plane communication?
A
DRAG DROP -
Drag and drop the capabilities from the left onto the correct technologies on the right.
Select and Place: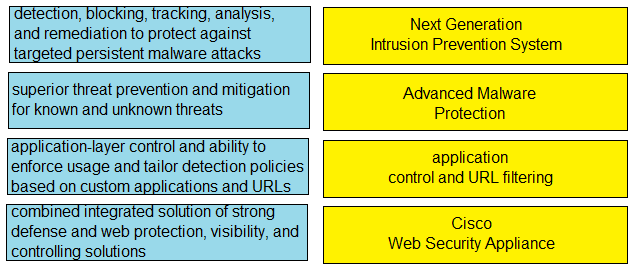
Which two key and block sizes are valid for AES? (Choose two.)
CD
Reference:
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard