What are two things to consider when using PAC files with the Cisco WSA? (Choose two.)
BC
Which IETF attribute is supported for the RADIUS CoA feature?
A
When a transparent authentication fails on the Web Security Appliance, which type of access does the end user get?
C
What are two ways that Cisco Container Platform provides value to customers who utilize cloud service providers? (Choose two.)
AE
DRAG DROP -
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
Select and Place: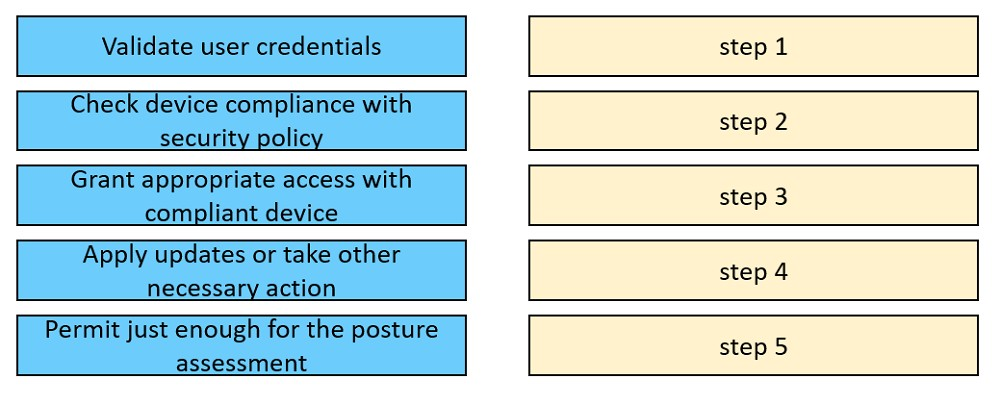
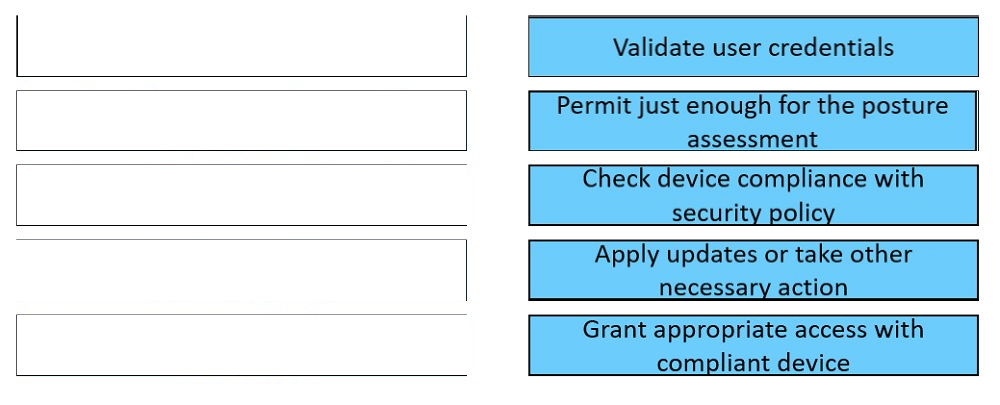

Refer to the exhibit.
What does the API key do while working with https://api.amp.cisco.com/v1/computers?
C
Which statement describes a serverless application?
B
What is a description of microsegmentation?
B
Which Cisco WSA feature supports access control using URL categories?
A
Which technology limits communication between nodes on the same network segment to individual applications?
B