Which Cisco product is open, scalable, and built on IETF standards to allow multiple security products from Cisco and other vendors to share data and interoperate with each other?
A
Reference:
https://www.cisco.com/c/en/us/products/security/pxgrid.html
Which compliance status is shown when a configured posture policy requirement is not met?
D
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
B
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network. What action will resolve this issue?
B
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
B
Drag and drop the solutions from the left onto the solution's benefits on the right.
Select and Place: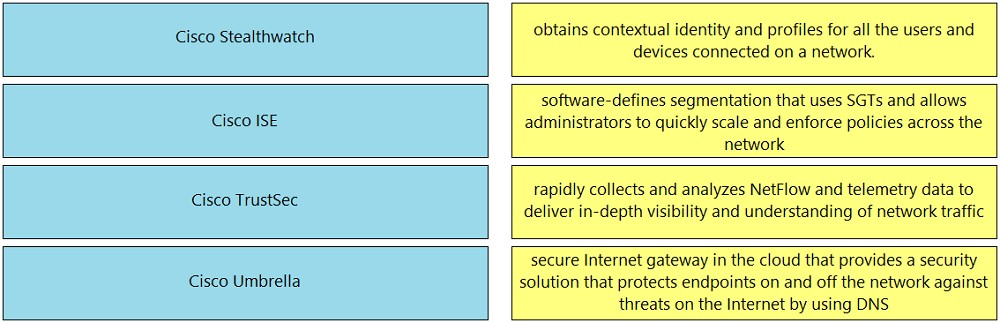
A network engineer must monitor user and device behavior within the on-premises network. This data must be sent to the Cisco Stealthwatch Cloud analytics platform for analysis. What must be done to meet this requirement, using the Ubuntu-based VM appliance deployed in a VMware-based hypervisor?
C
An organization wants to provide visibility and to identify active threats in its network using a VM. The organization wants to extract metadata from network packet flow while ensuring that payloads are not retained or transferred outside the network. Which solution meets these requirements?
B
What is a benefit of performing device compliance?
B
Which type of DNS abuse exchanges data between two computers even when there is no direct connection?
D