How does Cisco Stealthwatch Cloud provide security for cloud environments?
A
Reference:
https://www.content.shi.com/SHIcom/ContentAttachmentImages/SharedResources/FBLP/Cisco/Cisco-091919-Simple-IT-Whitepaper.pdf
Which Cisco security solution protects remote users against phishing attacks when they are not connected to the VPN?
A
What must be used to share data between multiple security products?
A
Which two characteristics of messenger protocols make data exfiltration difficult to detect and prevent? (Choose two.)
AE
Which solution combines Cisco IOS and IOS XE components to enable administrators to recognize applications, collect and send network metrics to Cisco Prime and other third-party management tools, and prioritize application traffic?
B
What provides visibility and awareness into what is currently occurring on the network?
D
How is ICMP used as an exfiltration technique?
C
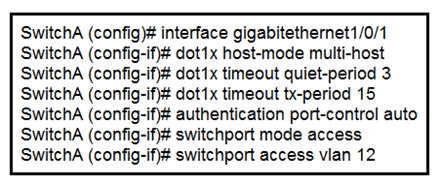
Refer to the exhibit. An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
C
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
A
What are two Detection and Analytics Engines of Cognitive Threat Analytics? (Choose two.)
AB
Reference:
https://www.cisco.com/c/dam/en/us/products/collateral/security/cognitive-threat-analytics/at-a-glance-c45-736555.pdf