Refer to the exhibit.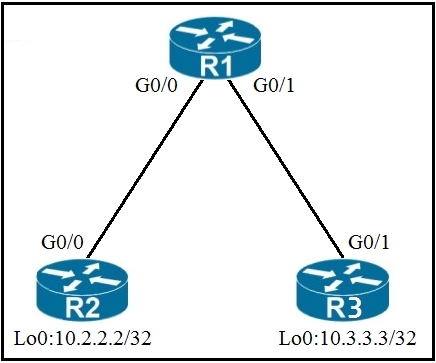
An engineer must deny Telnet traffic from the loopback interface of router R3 to the loopback interface of router R2 during the weekend hours. All other traffic between the loopback interfaces of routers R3 and R2 must be allowed at all times.
Which command set accomplishes this task?
B
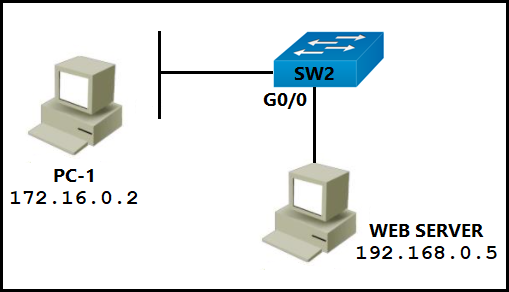
Refer to the exhibit. PC-1 must access the web server on port 8080. To allow this traffic, which statement must be added to an access control list that is applied on
SW2 port G0/0 in the inbound direction?
C
What is the result of applying this access control list?
ip access-list extended STATEFUL
10 permit tcp any any established
20 deny ip any any
C
Which outbound access list, applied to the WAN interface of a router, permits all traffic except for http traffic sourced from the workstation with IP address
10.10.10.1?
D
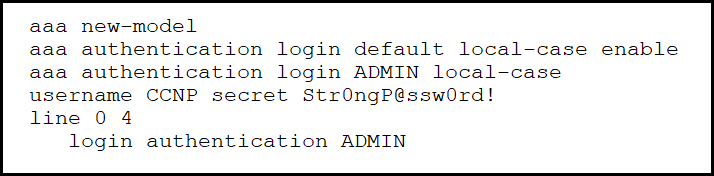
Refer to the exhibit. An engineer must create a configuration that executes the show run command and then terminates the session when user CCNP logs in.
Which configuration change is required?
D
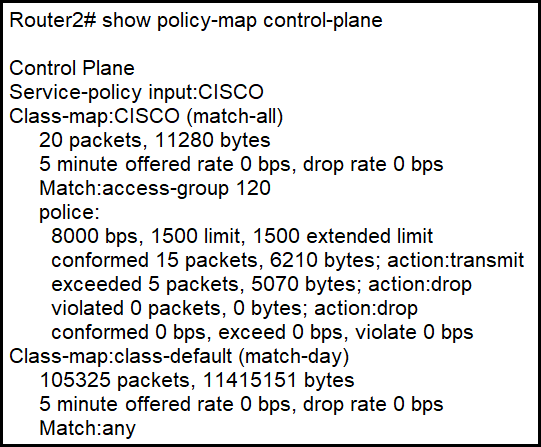
Refer to the exhibit. An engineer configures CoPP and enters the show command to verify the implementation. What is the result of the configuration?
A
DRAG DROP -
Drag and drop the threat defense solutions from the left onto their descriptions on the right.
Select and Place: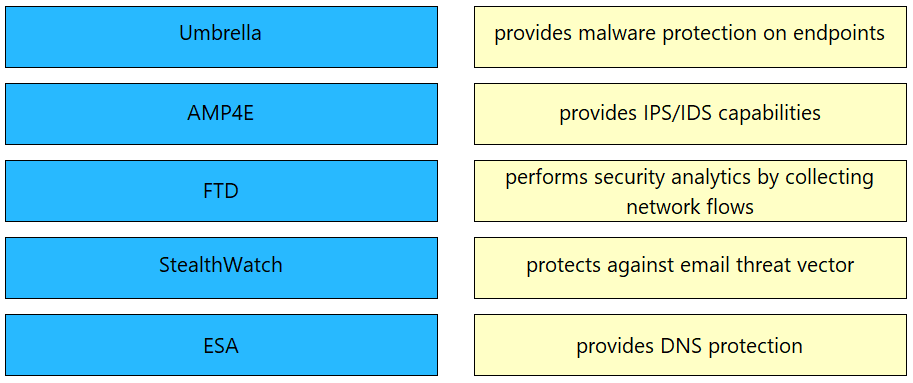
Refer to the exhibit.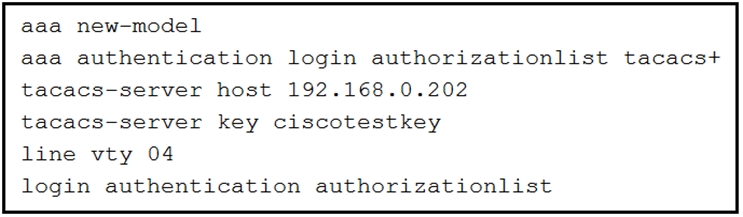
What is the effect of this configuration?
B
Which deployment option of Cisco NGFW provides scalability?
C
DRAG DROP -
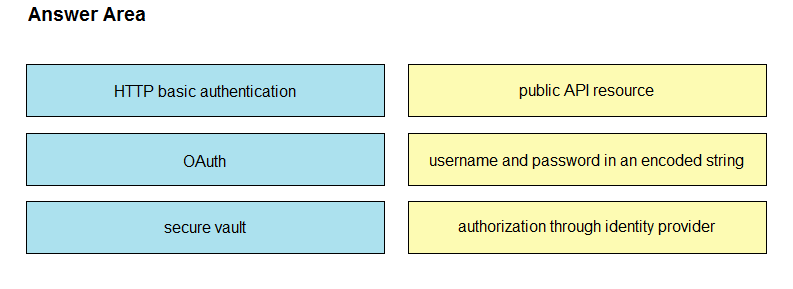
Drag and drop the REST API authentication methods from the left onto their descriptions on the right.
Select and Place: