Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
C
An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web
Policy.
Which device presents the web authentication for the WLAN?
D
Which method does the enable secret password option use to encrypt device passwords?
A
Reference:
https://www.cisco.com/c/en/us/support/docs/security-vpn/remote-authentication-dial-user-service-radius/107614-64.html
On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A
What is the difference between the enable password and the enable secret password when service password encryption is enabled on an IOS device?
A
Which access control list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
D
A network administrator applies the following configuration to an IOS device: aaa new-model aaa authentication login default local group tacacs+
What is the process of password checks when a login attempt is made to the device?
D
Reference:
https://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controller-access-control-system-tacacs-/200606-aaa-authentication-login- default-local.html
Refer to the exhibit.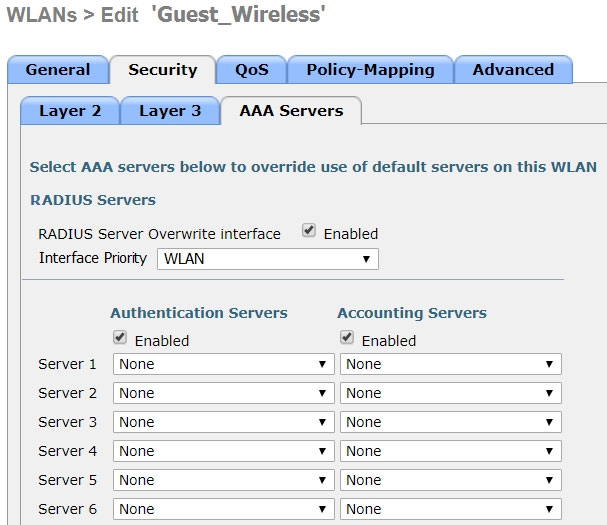
Assuming the WLC's interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
C
Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
B
An engineer must protect their company against ransomware attacks.
Which solution allows the engineer to block the execution stage and prevent file encryption?
B