In a Cisco SD-Access solution, what is the role of the Identity Services Engine?
A
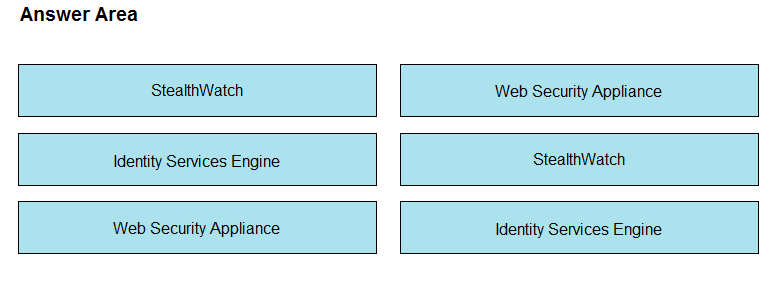
DRAG DROP -
Drag and drop the solutions that compromise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
Select and Place: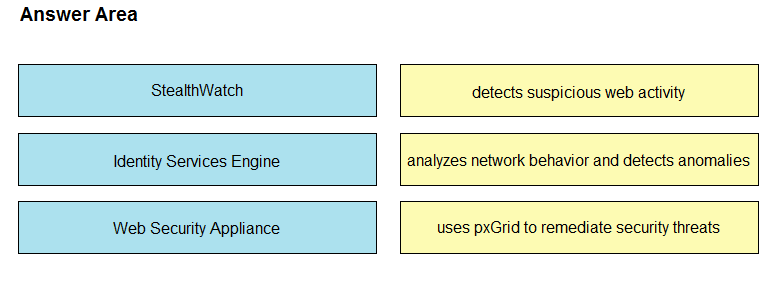
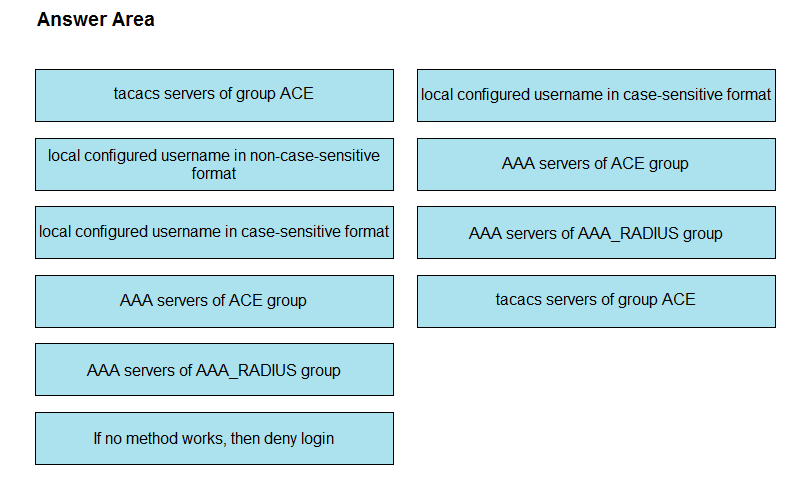
DRAG DROP -
An engineer creates the configuration below. Drag and drop the authentication methods from the left into the order of priority on the right. Not all options are used.
R1#sh run | i aaa -
aaa new-model
aaa authentication login default group ACE group AAA_RADIUS local-case aaa session-id common
R1#
Select and Place: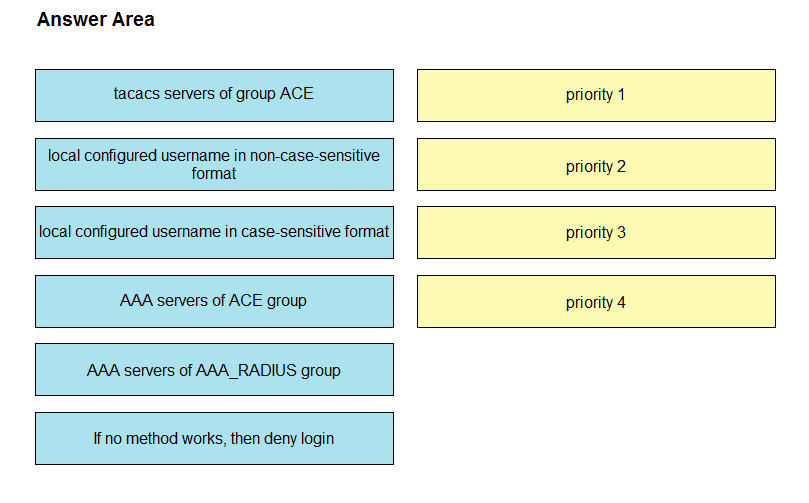
What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
B
An engineer must configure an ACL that permits packets which include an ACK in the TCP header. Which entry must be included in the ACL?
C
A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web server.
Which statement allows this traffic?
D
Which standard access control entry permits traffic from odd-numbered hosts in the 10.0.0.0/24 subnet?
B
Refer to the exhibit.
An engineer must modify the access control list EGRESS to allow all IP traffic from subnet 10.1.10.0/24 to 10.1.2.0/24. The access control list is applied in the outbound direction on router interface GigabitEthernet 0/1.
Which configuration command set will allow this traffic without disrupting existing traffic flows?
A.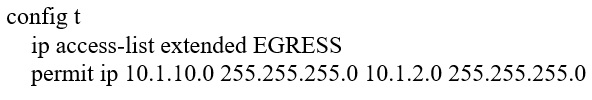
B.
C.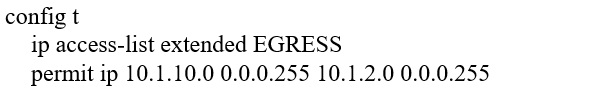
D.
D
Which configuration restricts the amount of SSH traffic that a router accepts to 100 kbps?
A.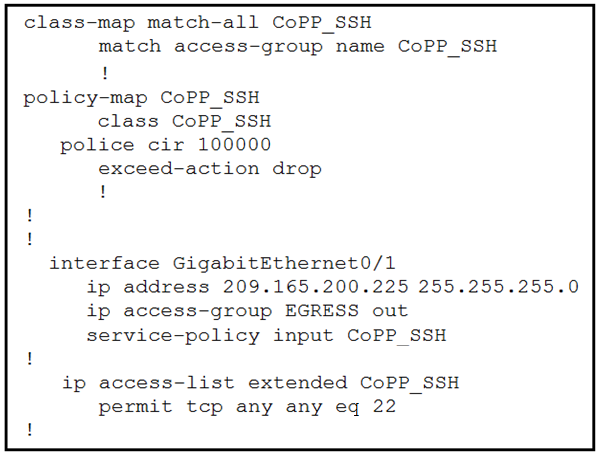
B.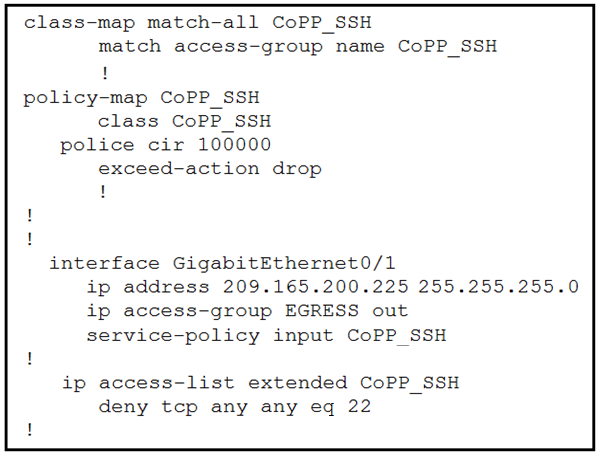
C.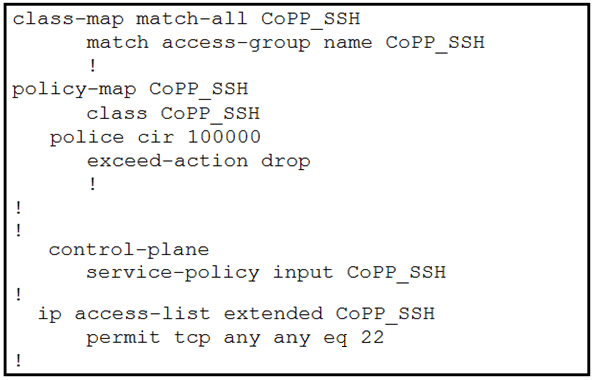
D.
C
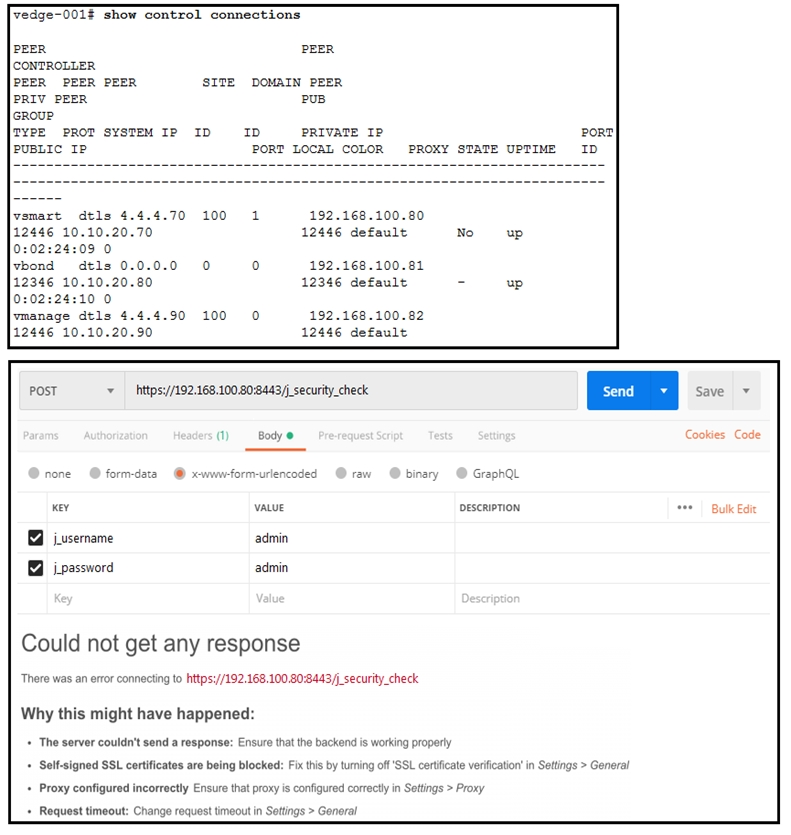
Refer to the exhibit. What step resolves the authentication issue?
D