Which command set configures RSPAN to capture outgoing traffic from VLAN 3 on interface GigabitEthernet 0/3 while ignoring other VLAN traffic on the same interface?
C

Refer to the exhibit. What is required to configure a second export destination for IP address 192.168.10.1?
A
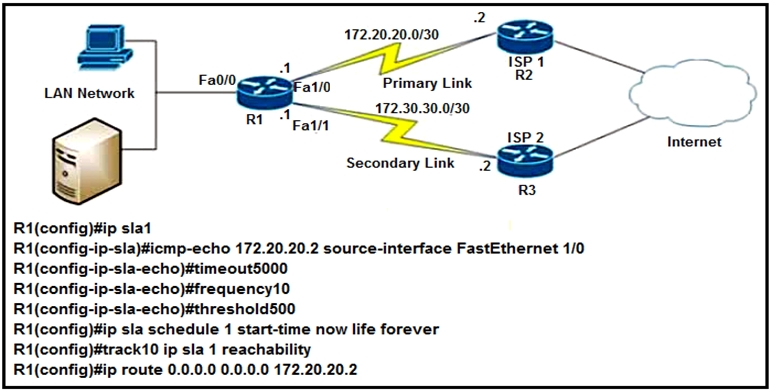
Refer to the exhibit. After implementing the configuration, 172.20.20.2 stops replying to ICMP echos, but the default route fails to be removed. What is the reason for this behavior?
D
Refer to the exhibit.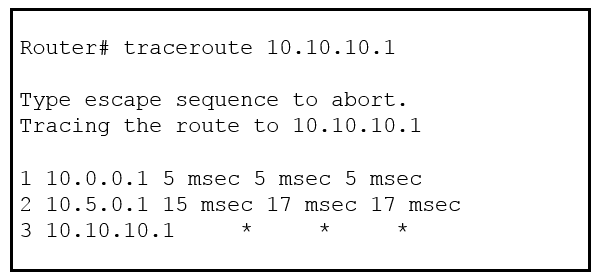
An engineer is troubleshooting a connectivity issue and executes a traceroute. What does the result confirm?
B
In Cisco routers, the codes for a traceroute command reply are:
! ג€" success
* ג€" time out
N ג€" network unreachable -
H ג€" host unreachable -
P ג€" protocol unreachable -
A ג€" admin denied -
Q ג€" source quench received (congestion)
? ג€" unknown (any other ICMP message). In Cisco routers, the codes for a traceroute command reply are:
! ג€" success
* ג€" time out
N ג€" network unreachable -
H ג€" host unreachable -
P ג€" protocol unreachable -
A ג€" admin denied -
Q ג€" source quench received (congestion)
? ג€" unknown (any other ICMP message)
Which Cisco DNA Center application is responsible for group-based access control permissions?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/1-3-1-0/user_guide/ b_cisco_dna_center_ug_1_3_1_0/b_cisco_dna_center_ug_1_3_1_0_chapter_01011.html
An engineer is concerned with the deployment of a new application that is sensitive to inter-packet delay variance. Which command configures the router to be the destination of jitter measurements?
C
Which NGFW mode blocks flows crossing the firewall?
B
Reference:
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/200924-configuring-firepower-threat-defense-int.html
How does Cisco TrustSec enable more flexible access controls for dynamic networking environments and data centers?
D
Reference:
https://www.cisco.com/c/dam/en/us/products/collateral/security/identity-services-engine/at_a_glance_c45-726831.pdf
The login method is configured on the VTY lines of a router with these parameters:
* The first method for authentication is TACACS
* If TACACS is unavailable, login is allowed without any provided credentials
Which configuration accomplishes this task?
A.
B.
C.
D.
D
Which feature does Cisco TrustSec use to provide scalable, secure communication throughout a network?
B
Reference:
https://www.cisco.com/c/dam/en/us/solutions/collateral/borderless-networks/trustsec/C07-730151-00_overview_of_trustSec_og.pdf