A network engineer is configuring Flexible NetFlow and enters these commands. sampler NetFlow1 mode random one-out-of 100 interface fastethernet 1/0 flow-sampler NetFlow1
What are two results of implementing this feature instead of traditional NetFlow? (Choose two.)
BC
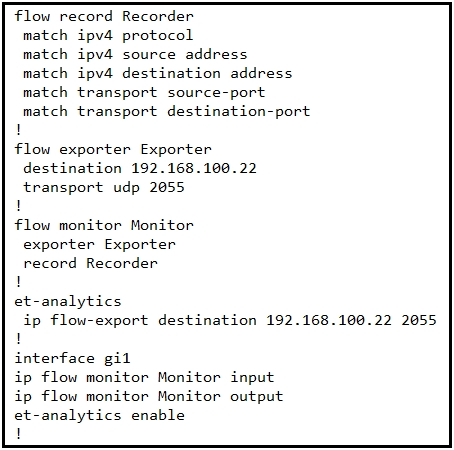
Refer to the exhibit. An engineer must add the SNMP interface table to the NetFlow protocol flow records. Where should the SNMP table option be added?
D
A network administrator is implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process.
Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two.)
BE
When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
C
Reference:
https://tools.ietf.org/html/rfc5425
Refer to this output.
R1# *Feb 14 37:09:53.129: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
What is the logging severity level?
A
An engineer reviews a router's logs and discovers the following entry. What is the event's logging severity level?
Router# *Jan 01 38:24:04.401: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to up
A
Refer to the exhibit.
An engineer must configure a SPAN session.
What is the effect of the configuration?
A
Refer to the exhibit.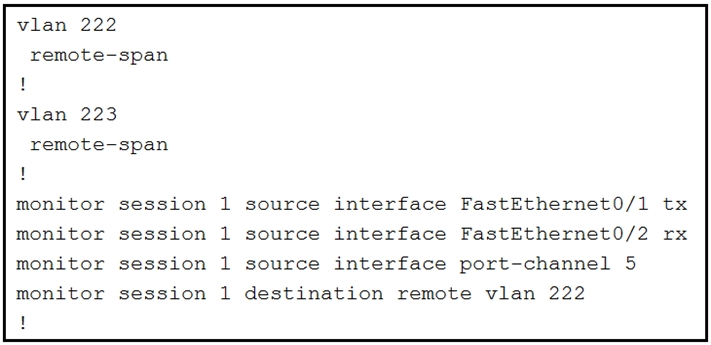
These commands have been added to the configuration of a switch.
Which command flags an error if it is added to this configuration?
B
Which method does Cisco DNA Center use to allow management of non-Cisco devices through southbound protocols?
A
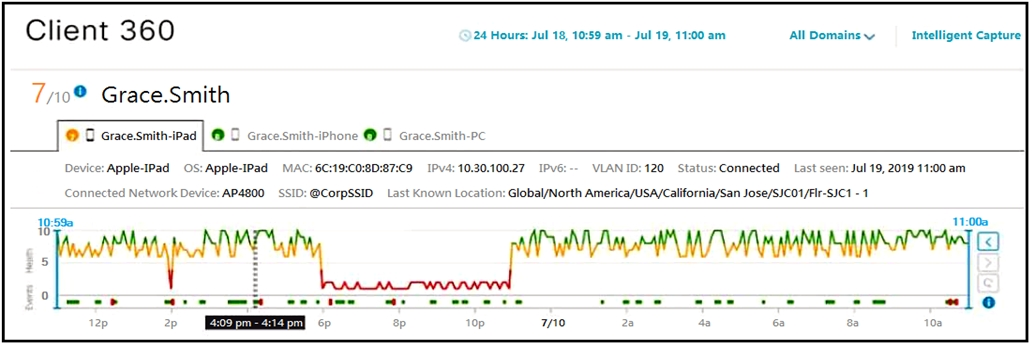
Refer to the exhibit. Cisco DNA Center has obtained the username of the client and the multiple devices that the client is using on the network. How is Cisco DNA
Center getting these context details?
C