Which configuration feature should be used to block rogue router advertisements instead of using the IPv6 Router Advertisement Guard feature?
B
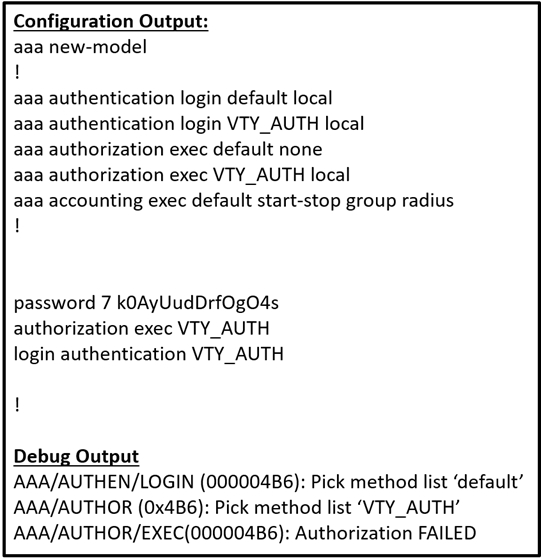
Refer to the exhibit.
Which action resolves the failed authentication attempt to the router?
A
Reference:
https://community.cisco.com/t5/network-access-control/console-authorization-issue/td-p/2492619
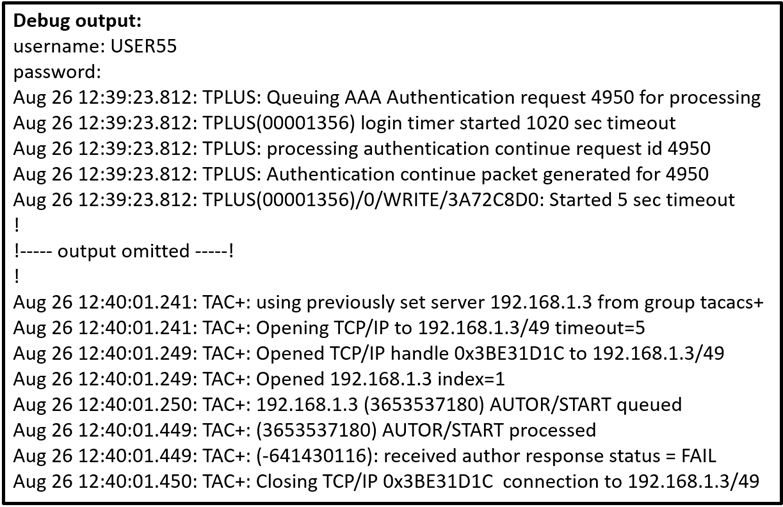
Refer to the exhibit. A network administrator logs into the router using TACACS+ username and password credentials, but the administrator cannot run any privileged commands.
Which action resolves the issue?
D
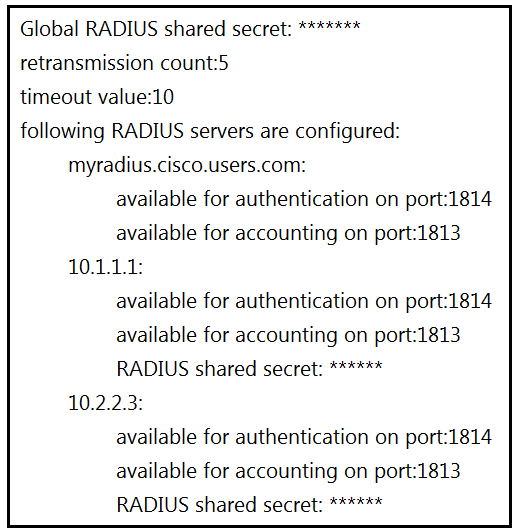
Refer to the exhibit. AAA server 10.1.1.1 is configured with the default authentication and accounting settings, but the switch cannot communicate with the server.
Which action resolves this issue?
B
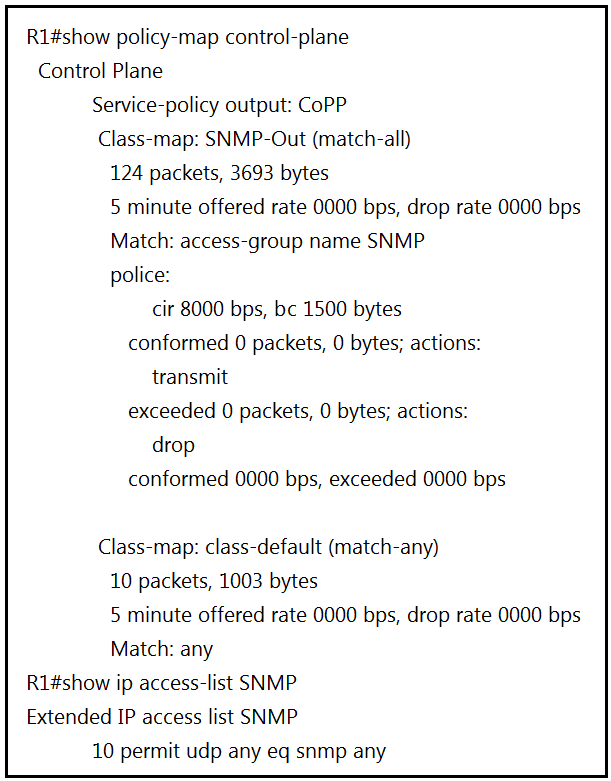
Refer to the exhibit. R1 is being monitored using SNMP and monitoring devices are getting only partial information.
What action should be taken to resolve this issue?
B
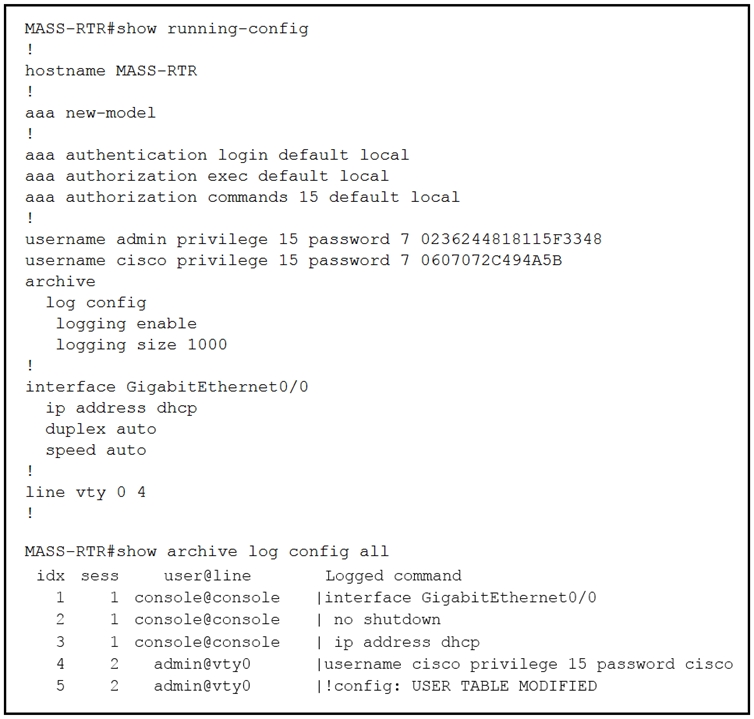
Refer to the exhibit. A client is concerned that passwords are visible when running this show archive log config all.
Which router configuration is needed to resolve this issue?
D
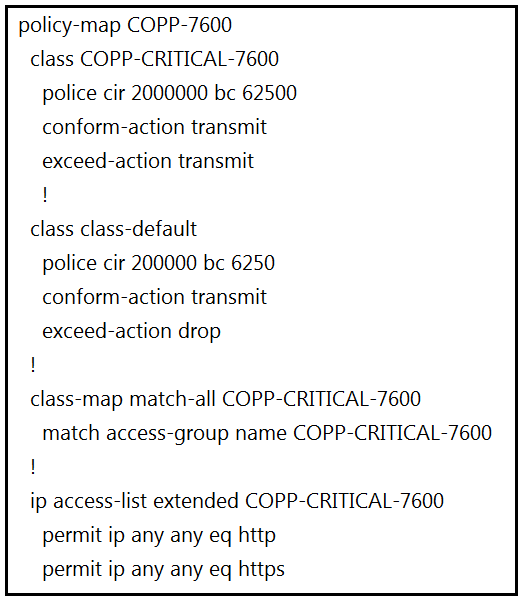
Refer to the exhibit. BGP is flapping after the CoPP policy is applied.
What are the two solutions to fix the issue? (Choose two.)
BC
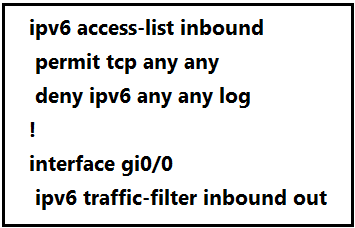
Refer to the exhibit. A network administrator configured an IPv6 access list to allow TCP return traffic only, but it is not working as expected.
Which changes resolve this issue?
A.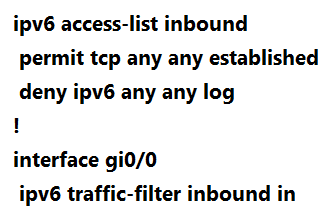
B.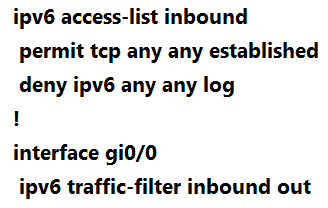
C.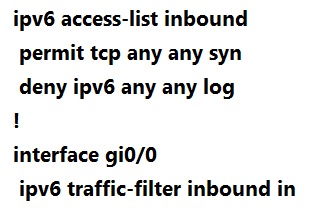
D.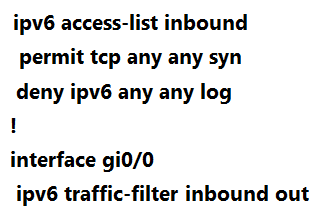
A
What are two functions of IPv6 Source Guard? (Choose two.)
BC
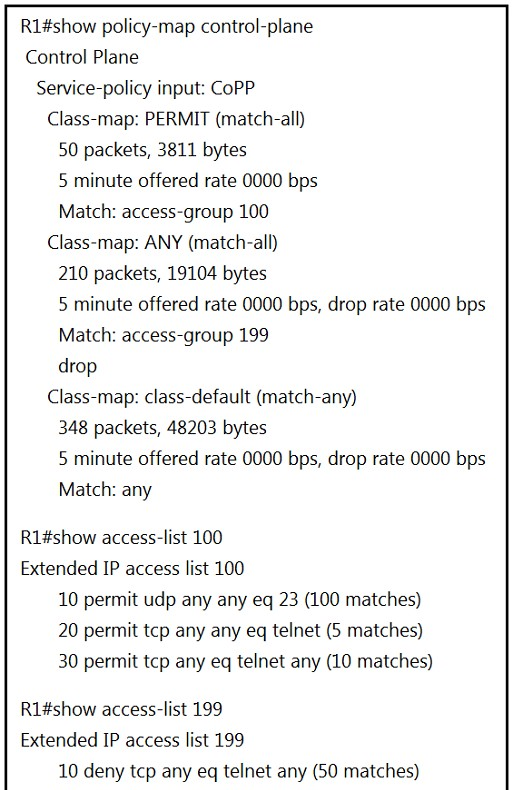
Refer to the exhibit. Which two actions restrict access to router R1 by SSH? (Choose two.)
AC