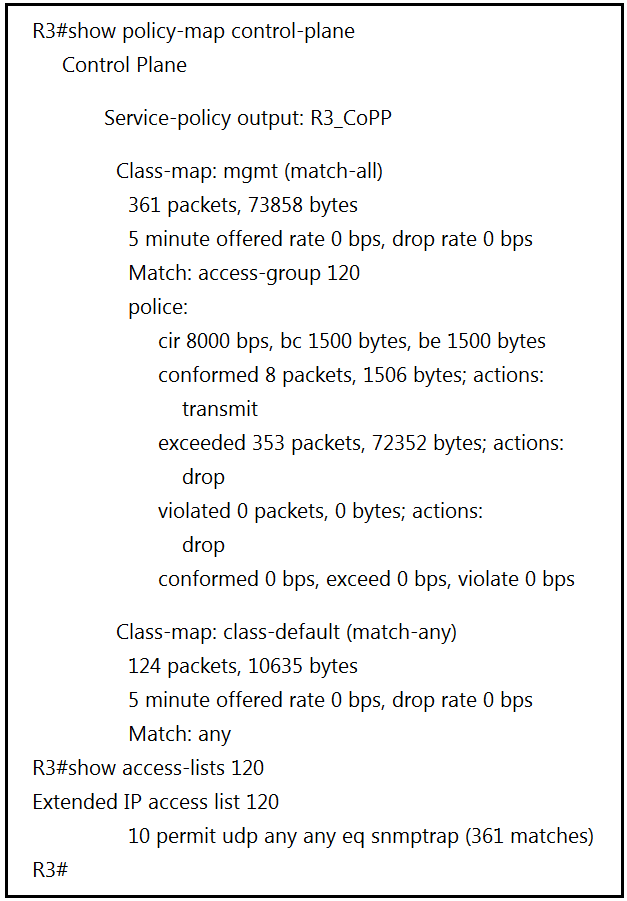
Refer to the exhibit. Which action resolves intermittent connectivity observed with the SNMP trap rackets?
B
DRAG DROP -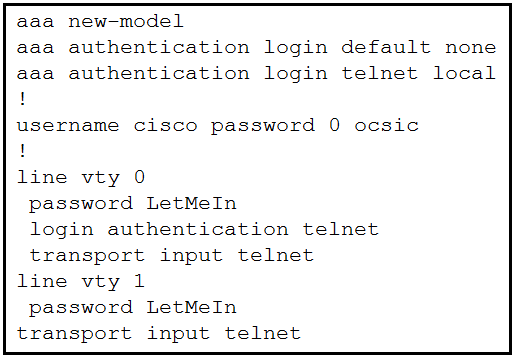
Refer to the exhibit. Drag and drop the credentials from the left onto the remote login information on the right to resolve a failed login attempt to vtys. Not all credentials are used.
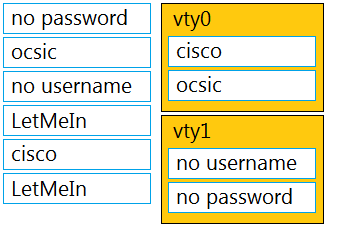
Select and Place: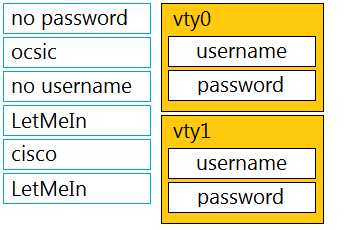
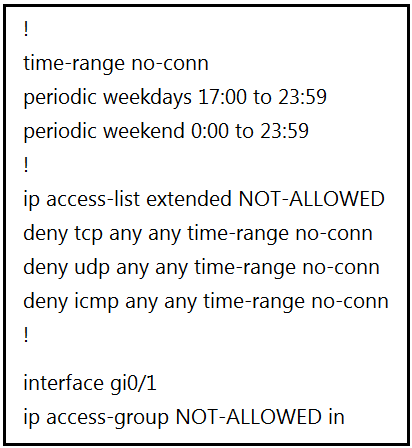
Refer to the exhibit. A network administrator wants to block all traffic toward the Internet after business hours and on weekends. When the administrator applies an access list on interface Gi0/1, all traffic is blocked and there is no access to the Internet at any time.
Which action resolves the issue?
B
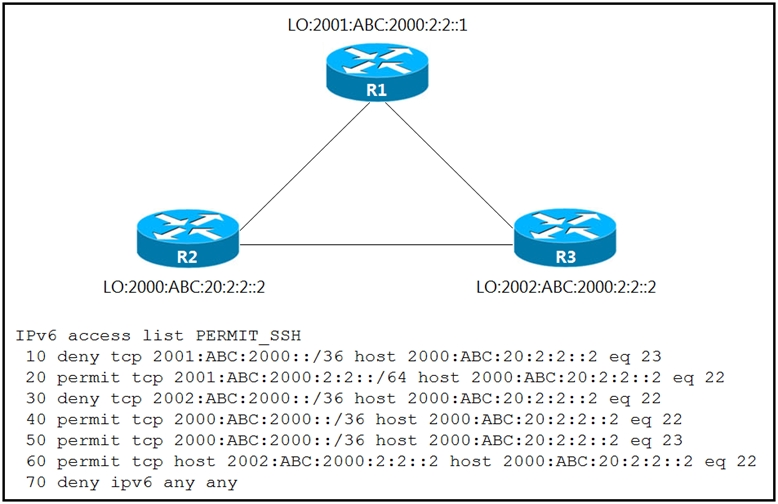
Refer to the exhibit. An IPv6 network was newly deployed in the environment, and the help desk reports that R3 cannot SSH to the R2s Loopback interface.
Which action resolves the issue?
C
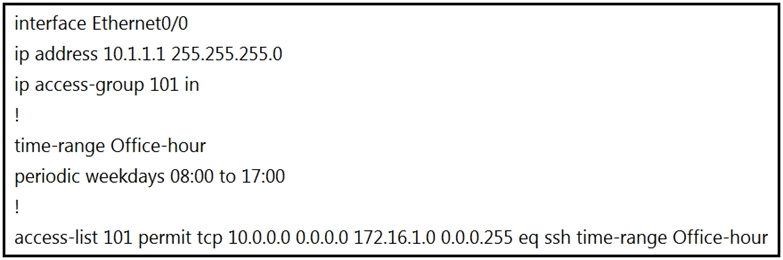
Refer to the exhibit. An IT staff member comes into the office during normal office hours and cannot access devices through SSH.
Which action should be taken to resolve this issue?
C
Refer to the exhibit.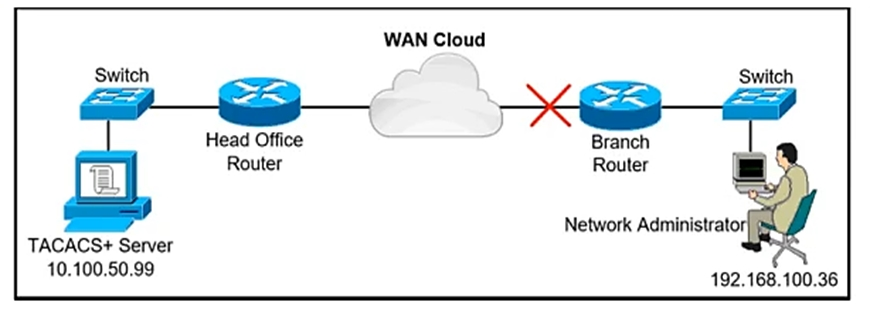
A network administrator is trying to access a branch router using TACACS+ username and password credentials, but the administrator cannot log in to the router because the WAN connectivity is down. The branch router has following AAA configuration: aaa new-model aaa authorization commands 15 default group tacacs+ aaa accounting commands 1 default stop-only group tacacs+ aaa accounting commands 15 default stop-only group tacacs+ tacacs-server host 10.100.50.99 tacacs-server key Ci$co123
Which command will resolve this problem when WAN connectivity is down?
B
Reference:
https://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controller-access-control-system-tacacs-/200606-aaa-authentication-login- default-local.html
Refer to the exhibit.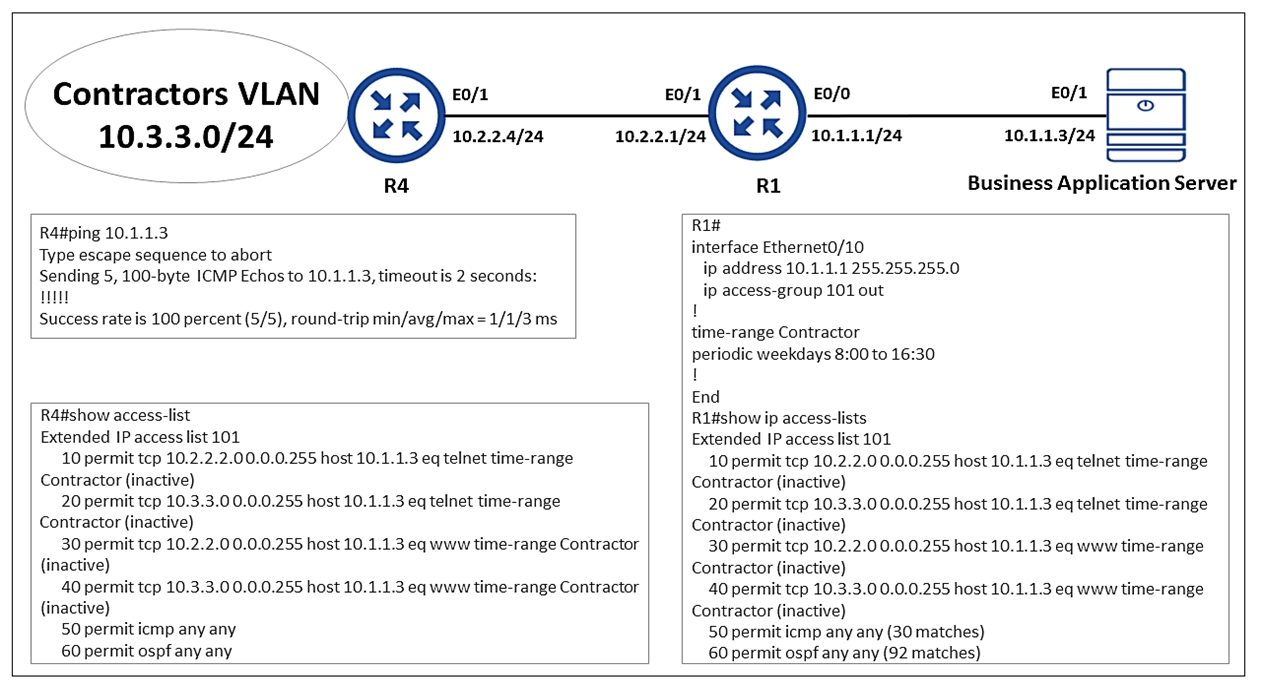
An engineer is troubleshooting failed access by contractors to the business application server via Telnet or HTTP during the weekend.
Which configuration resolves the issue?
B
What are two characteristics of IPv6 Source Guard? (Choose two.)
AD
DRAG DROP -
Drag and drop the IPv6 first hop security device roles from the left onto the corresponding descriptions on the right.
Select and Place: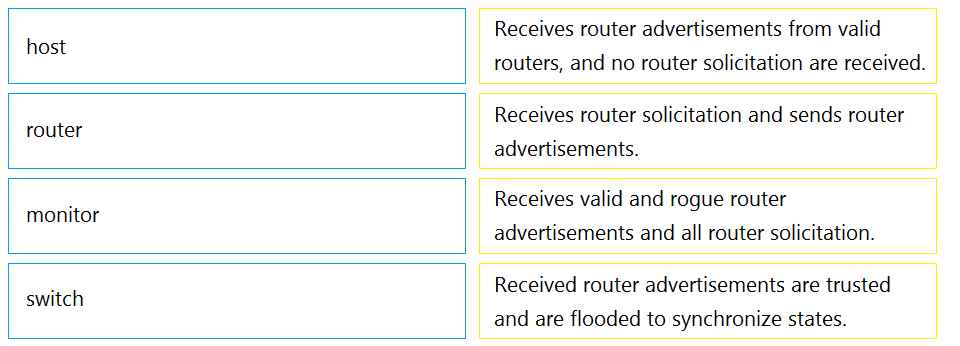
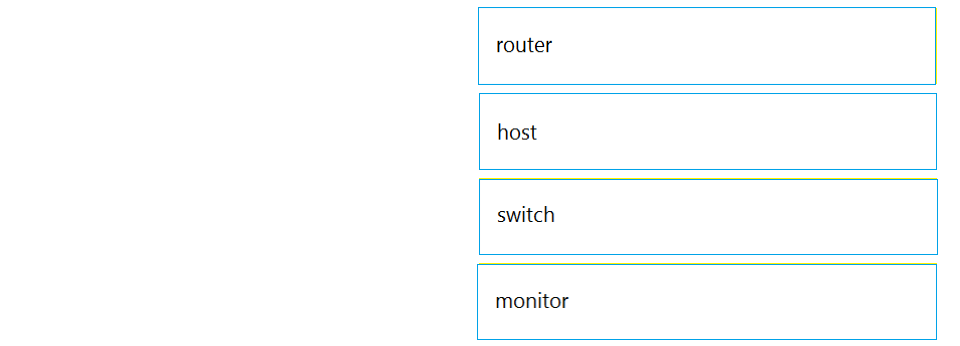
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/nexus9000/sw/7-x/security/configuration/guide/b_Cisco_Nexus_9000_Series_NX-
OS_Security_Configuration_Guide_7x/b_Cisco_Nexus_9000_Series_NX-OS_Security_Configuration_Guide_7x_chapter_011011.pdf
The network administrator configured R1 for Control Plane Policing so that the inbound Telnet traffic is policed to 100 kbps. This policy must not apply to traffic coming in from 10.1.1.1/32 and 172.16.1.1/32. The administrator has configured this: access-list 101 permit tcp host 10.1.1.1 any eq 23 access-list 101 permit tcp host 172.16.1.1 any eq 23
!
class-map CoPP-TELNET
match access-group 101
!
policy-map PM-CoPP
class CoPP-TELNET
police 100000 conform transmit exceed drop
!
control-plane
service-policy input PM-CoPP
The network administrator is not getting the desired results.
Which set of configurations resolves this issue?
A