While troubleshooting connectivity issues to a router, these details are noticed:
✑ Standard pings to all router interfaces, including loopbacks, are successful.
✑ Data traffic is unaffected.
✑ SNMP connectivity is intermittent.
✑ SSH is either slow or disconnects frequently.
Which command must be configured first to troubleshoot this issue?
A

Refer to the exhibit. Why is user authentication being rejected?
D
Reference:
https://www.cisco.com/c/en/us/support/docs/security-vpn/terminal-access-controller-access-control-system-tacacs-/13864-tacacs-pppdebug.html

Refer to the exhibit. Which control plane policy limits BGP traffic that is destined to the CPU to 1 Mbps and ignores BGP traffic that is sent at higher rate?
D
Which statement about IPv6 RA Guard is true?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/ipv6_fhsec/configuration/xe-16/ip6f-xe-16-book/ip6-ra-guard.pdf
An engineer must configure a Cisco router to initiate secure connections from the router to other devices in the network but kept failing.
Which two actions resolve the issue? (Choose two.)
BC
When configuring Control Plane Policing on a router to protect it from malicious traffic, an engineer observes that the configured routing protocols start flapping on that device.
Which action in the Control Plane Policy prevents this problem in a production environment while achieving the security objective?
B
In which two ways does the IPv6 First-Hop Security Binding Table operate? (Choose two.)
BC
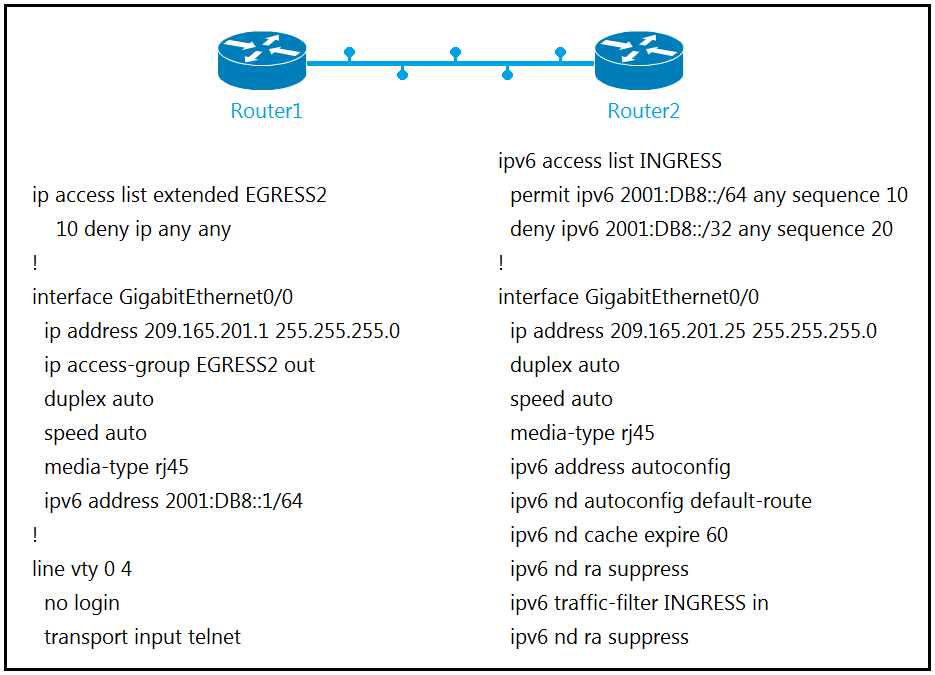
Refer to the exhibit. The engineer configured and connected Router2 to Router1. The link came up but could not establish a Telnet connection to Router1 IPv6 address of 2001:DB8::1.
Which configuration allows Router2 to establish a Telnet connection to Router1?
C
An engineer configured Reverse Path Forwarding on an interface and noticed that the routes are dropped when a route lookup fails on that interface for a prefix that is available in the routing table.
Which interface configuration resolves the issue?
C

Refer to the exhibit. When monitoring an IPv6 access list, an engineer notices that the ACL does not have any hits and is causing unnecessary traffic through the interface
Which command must be configured to resolve the issue?
C
Reference:
https://www.cisco.com/c/en/us/support/docs/ip/ip-version-6/113126-ipv6-acl-00.html