A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
C
DRAG DROP -
Drag and drop the type of evidence from the left onto the description of that evidence on the right.
Select and Place: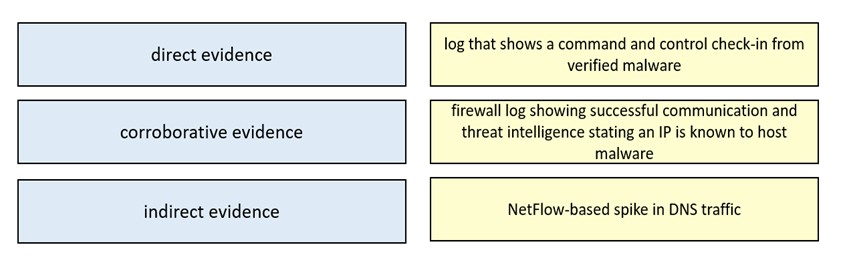

Refer to the exhibit. An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
D
Reference:
https://vwannabe.com/2018/01/02/ccna-cyber-ops-secops-1-0/
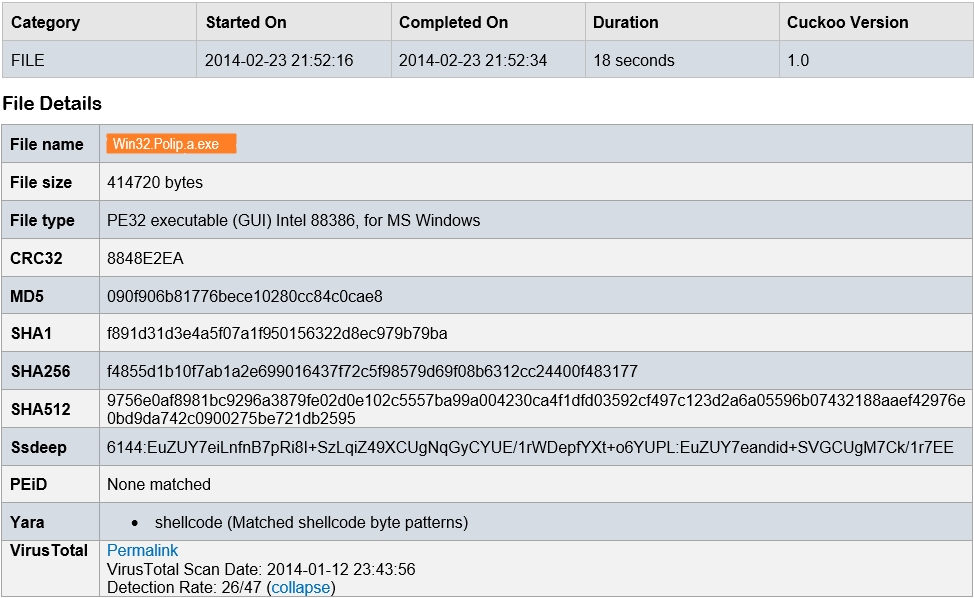
Refer to the exhibit. Which piece of information is needed to search for additional downloads of this file by other hosts?
D
An organization's security team has detected network spikes coming from the internal network. An investigation has concluded that the spike in traffic was from intensive network scanning. How should the analyst collect the traffic to isolate the suspicious host?
B
Which technology on a host is used to isolate a running application from other application?
D
Reference:
https://searchsecurity.techtarget.com/definition/sandbox#:~:text=Sandboxes%20can%20be%20used%20to,be%20run%20inside%20a%20sandbox

Refer to the exhibit. Which type of attack is being executed?
C
Reference:
https://www.w3schools.com/sql/sql_injection.asp
What is a difference between inline traffic interrogation and traffic mirroring?
B
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
B
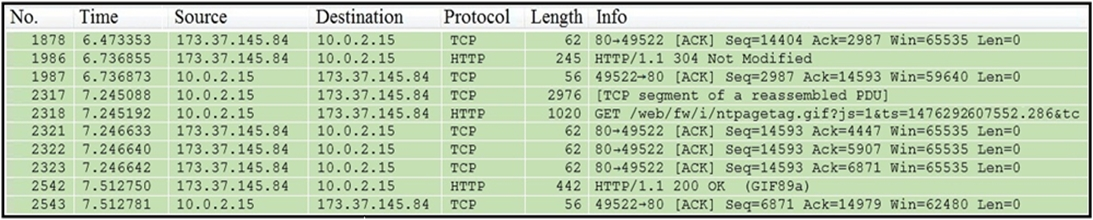
Refer to the exhibit. Which packet contains a file that is extractable within Wireshark?
D