What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
BE
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
C
Which step in the incident response process researches an attacking host through logs in a SIEM?
A
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
D
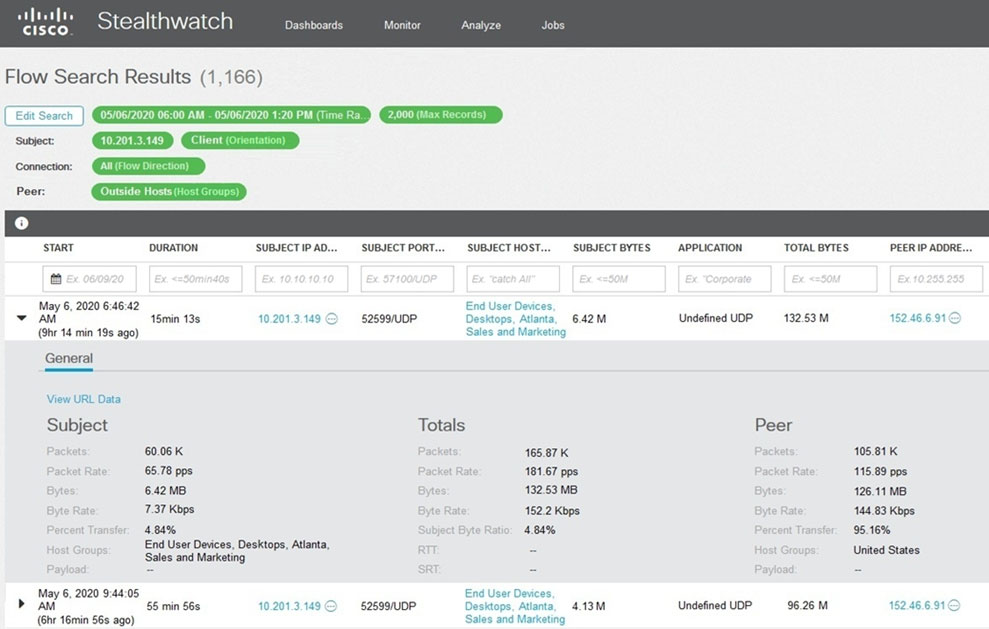
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
D
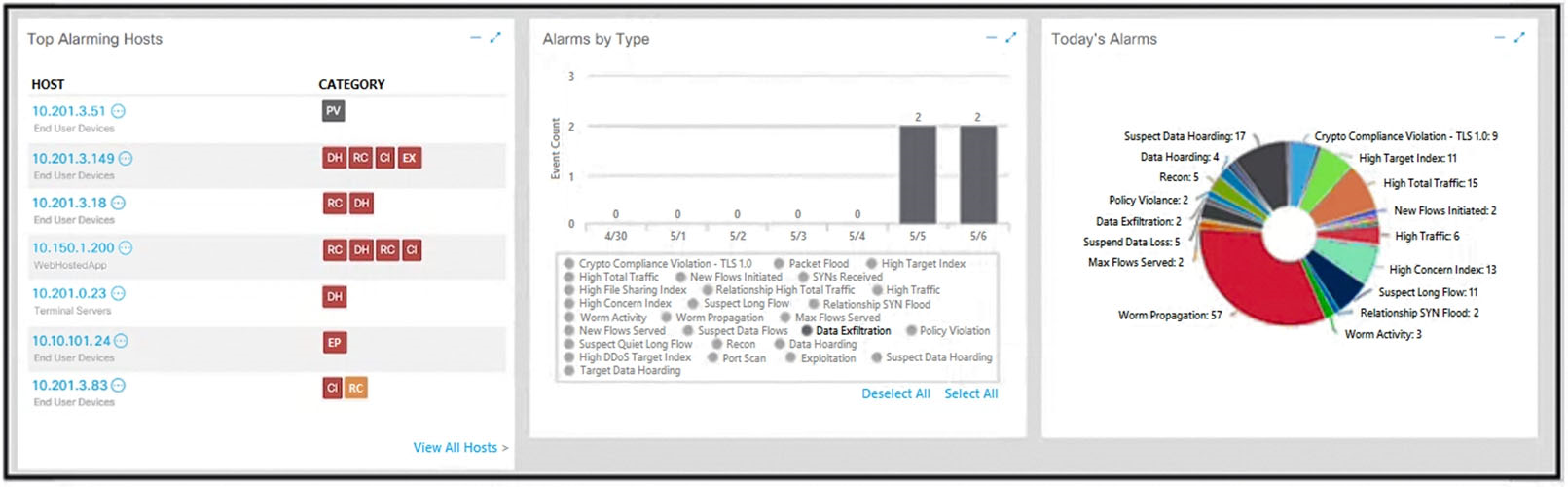
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
C
Which security technology allows only a set of pre-approved applications to run on a system?
C
An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
B
Which piece of information is needed for attribution in an investigation?
C
What does cyber attribution identify in an investigation?
D