Which regex matches only on all lowercase letters?
A
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
D
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
A
What is the impact of false positive alerts on business compared to true positive?
D
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
D

Refer to the exhibit. Which technology generates this log?
D
Which filter allows an engineer to filter traffic in Wireshark to further analyze the PCAP file by only showing the traffic for LAN 10.11.x.x, between workstations and servers without the Internet?
B
Which tool provides a full packet capture from network traffic?
D
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
D
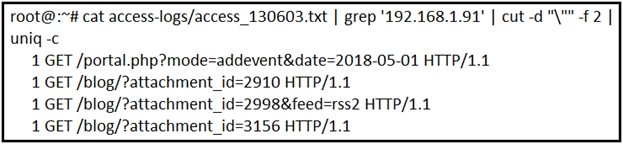
Refer to the exhibit. What is depicted in the exhibit?
B