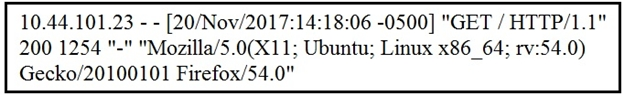
Refer to the exhibit. What does the message indicate?
C
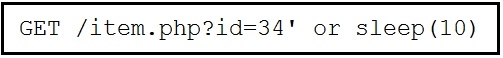
Refer to the exhibit. This request was sent to a web application server driven by a database.
Which type of web server attack is represented?
D
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions.
Which identifier tracks an active program?
D
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
B
Which system monitors local system operation and local network access for violations of a security policy?
C
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
C
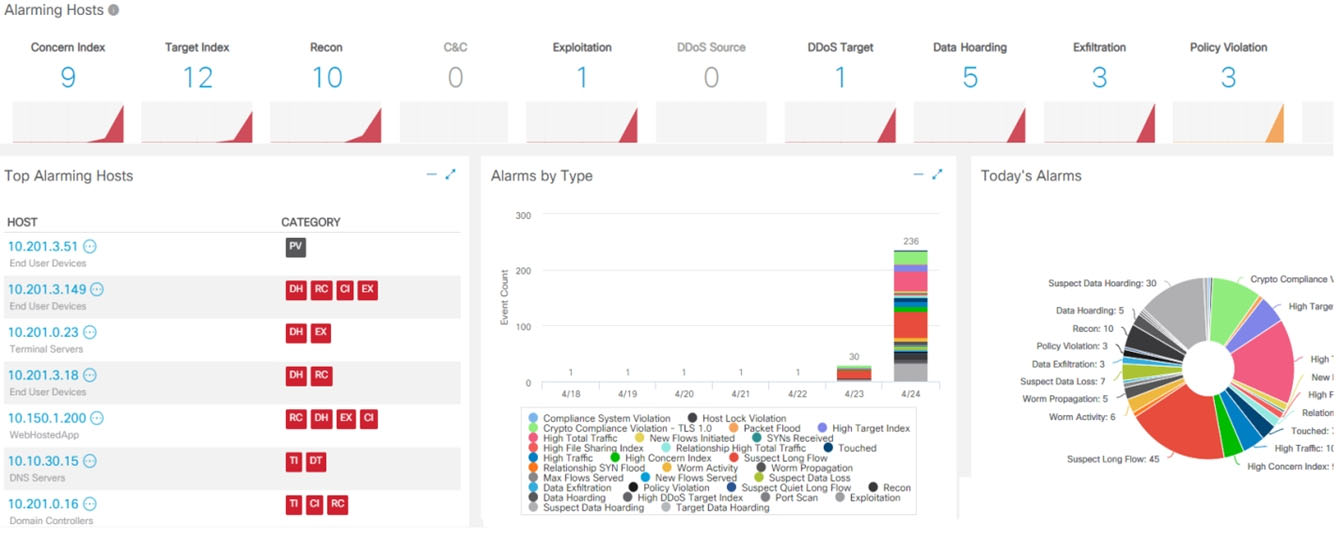
Refer to the exhibit. What is the potential threat identified in this Stealthwatch dashboard?
B
What is a difference between tampered and untampered disk images?
C
What is a sandbox interprocess communication service?
C
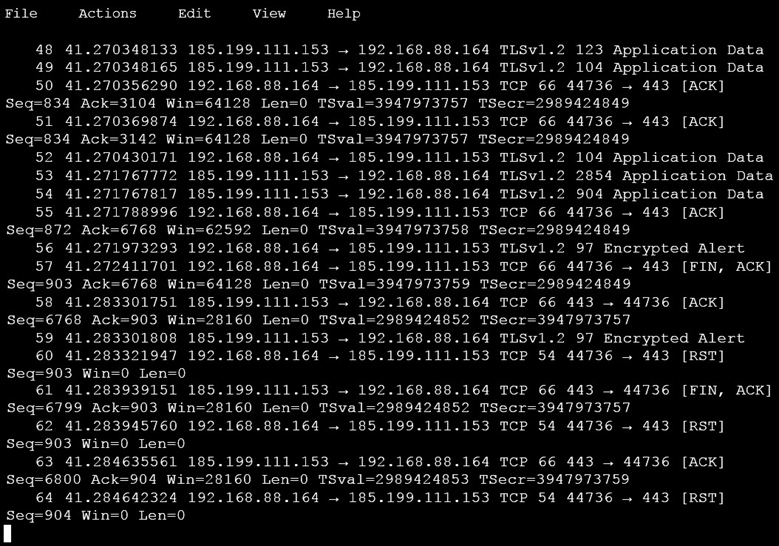
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
Which obfuscation technique is the attacker using?
B