
Refer to the exhibit. Which event is occurring?
C
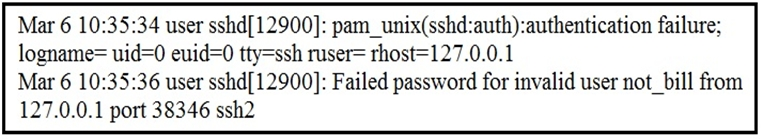
Refer to the exhibit. In which Linux log file is this output found?
D
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
BE
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
D
What causes events on a Windows system to show Event Code 4625 in the log messages?
B
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
D
What is rule-based detection when compared to statistical detection?
B
A user received a malicious attachment but did not run it.
Which category classifies the intrusion?
D
Which process is used when IPS events are removed to improve data integrity?
B
An analyst is investigating an incident in a SOC environment.
Which method is used to identify a session from a group of logs?
C