Which two components reduce the attack surface on an endpoint? (Choose two.)
AD
What is an attack surface as compared to a vulnerability?
B
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email. When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
A
What are two social engineering techniques? (Choose two.)
CE
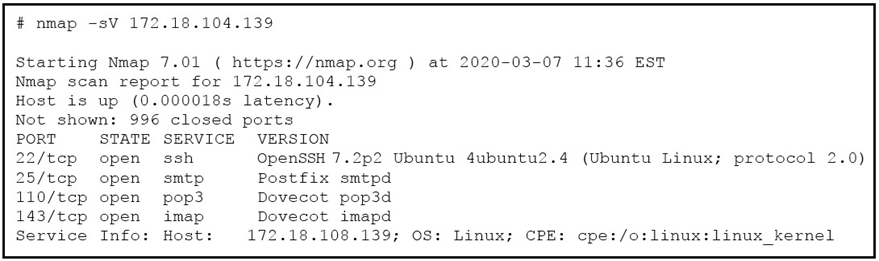
Refer to the exhibit. What does the output indicate about the server with the IP address 172.18.104.139?
C
How does certificate authority impact a security system?
B
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications Which technology should be used to accomplish the task?
B
Reference:
https://en.wikipedia.org/wiki/Cipher_suite
What is indicated by an increase in IPv4 traffic carrying protocol 41?
B
Reference:
https://simple.wikipedia.org/wiki/Protocol_41
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
C
Reference:
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/enterprise-network-security/white-paper-c11-736595.html
Which attack represents the evasion technique of resource exhaustion?
C
Reference:
https://www.ciscopress.com/articles/article.asp?p=3100055&seqNum=3