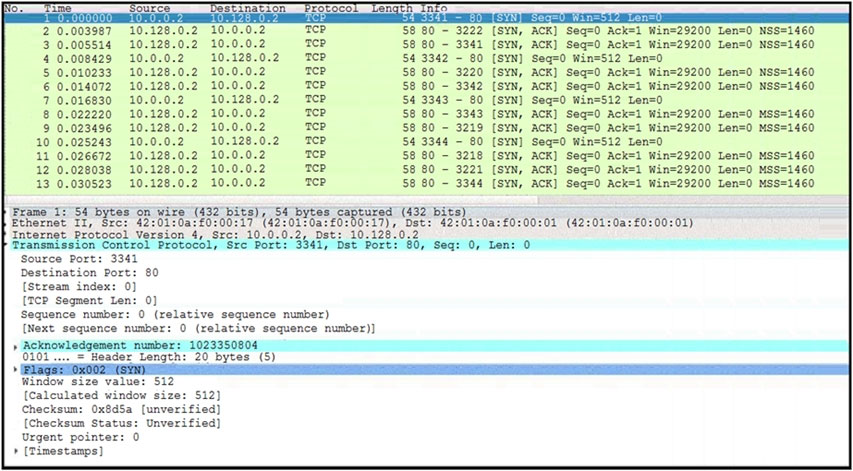
Refer to the exhibit. What is occurring in this network traffic?
D
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
DE
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
B
An engineer is investigating a case of the unauthorized usage of the `Tcpdump` tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
A
At a company party a guest asks questions about the company's user account format and password complexity. How is this type of conversation classified?
D
Which security monitoring data type requires the largest storage space?
D
What are two denial of service attacks? (Choose two.)
CE
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
B
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
B
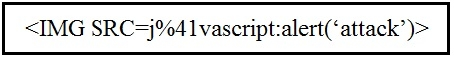
Refer to the exhibit. Which kind of attack method is depicted in this string?
A