An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network.
What is the impact of this traffic?
D
What is an example of social engineering attacks?
B
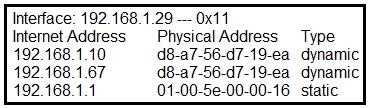
Refer to the exhibit. What is occurring in this network?
A
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
C
Which action prevents buffer overflow attacks?
C
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
D
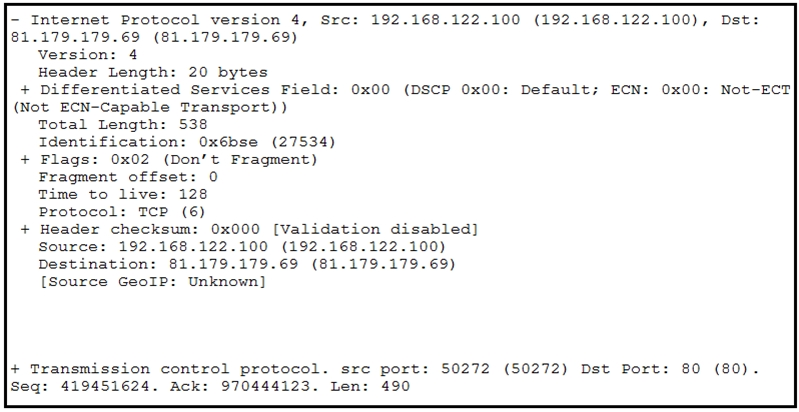
Refer to the exhibit. What should be interpreted from this packet capture?
B
What are the two characteristics of the full packet captures? (Choose two.)
CE
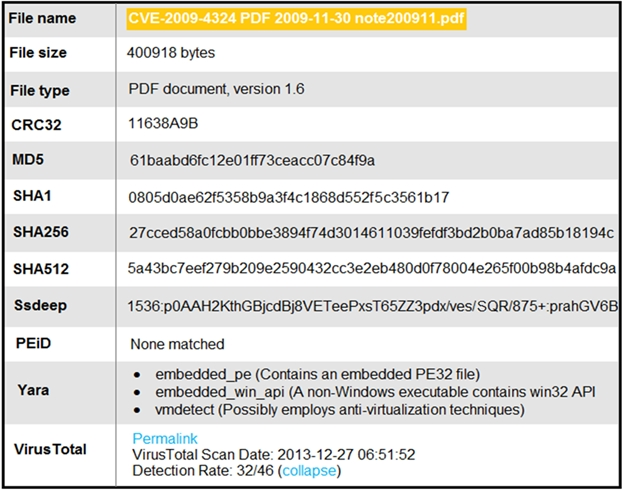
Refer to the exhibit. An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
C
DRAG DROP -
Drag and drop the technology on the left onto the data type the technology provides on the right.
Select and Place: