Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
C
Which list identifies the information that the client sends to the server in the negotiation phase of the TLS handshake?
C

Refer to the exhibit. Which type of log is displayed?
D
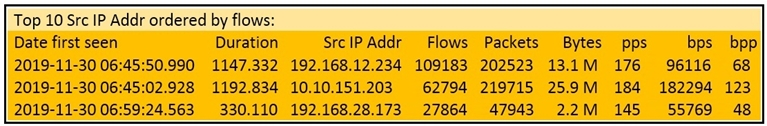
Refer to the exhibit. What information is depicted?
B
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
D

Refer to the exhibit. Which type of log is displayed?
B
How is NetFlow different from traffic mirroring?
A
What makes HTTPS traffic difficult to monitor?
D
How does an attacker observe network traffic exchanged between two users?
B
Which type of data consists of connection level, application-specific records generated from network traffic?
A