Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
D
Which regular expression matches "color" and "colour"?
C
Which artifact is used to uniquely identify a detected file?
D
A security engineer deploys an enterprise-wide host/endpoint technology for all of the company's corporate PCs. Management requests the engineer to block a selected set of applications on all PCs.
Which technology should be used to accomplish this task?
A
Which utility blocks a host portscan?
C
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
A
DRAG DROP -
Drag and drop the technology on the left onto the data type the technology provides on the right.
Select and Place: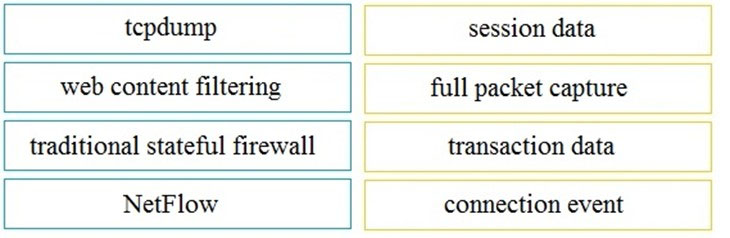
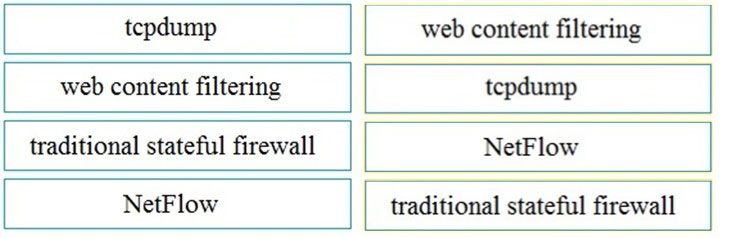
Refer to the exhibit. Which application protocol is in this PCAP file?
B
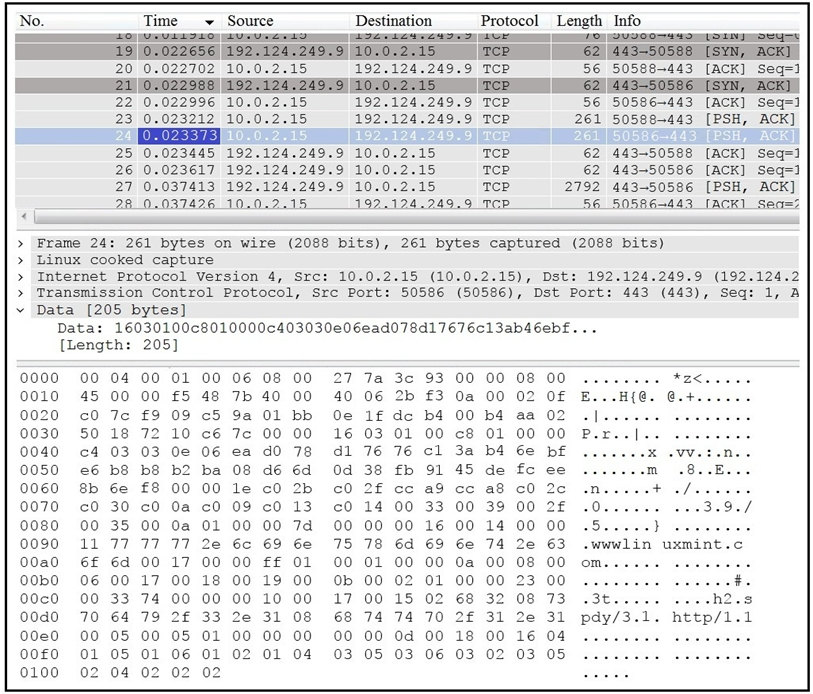
DRAG DROP -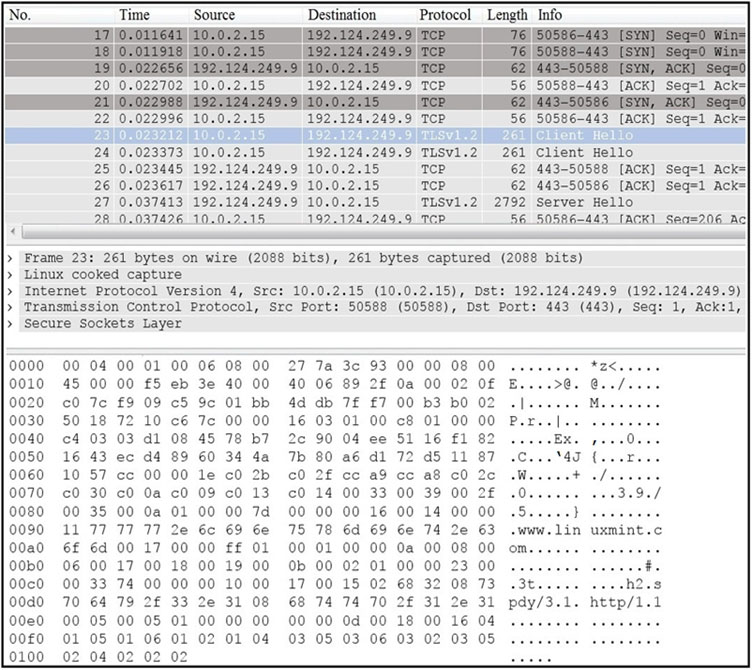
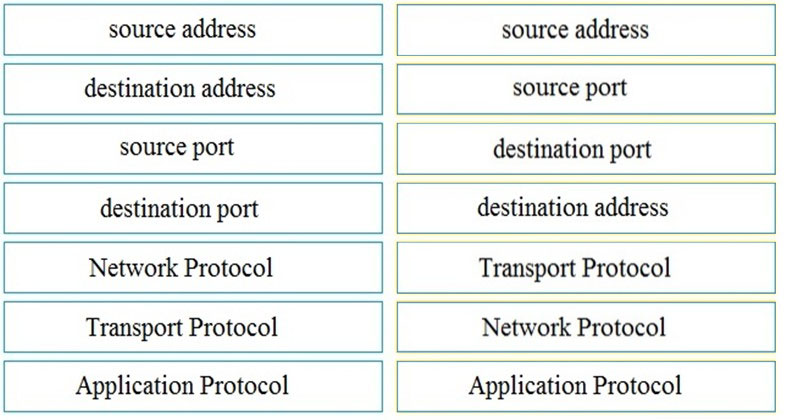
Refer to the exhibit. Drag and drop the element name from the left onto the appropriate piece of the PCAP file on the right.
Select and Place: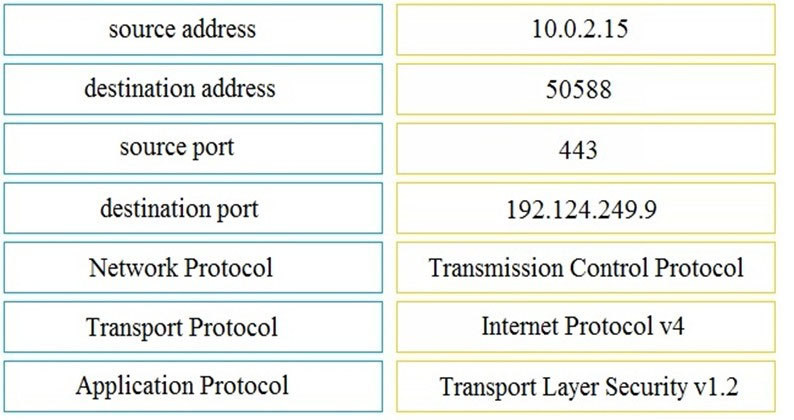
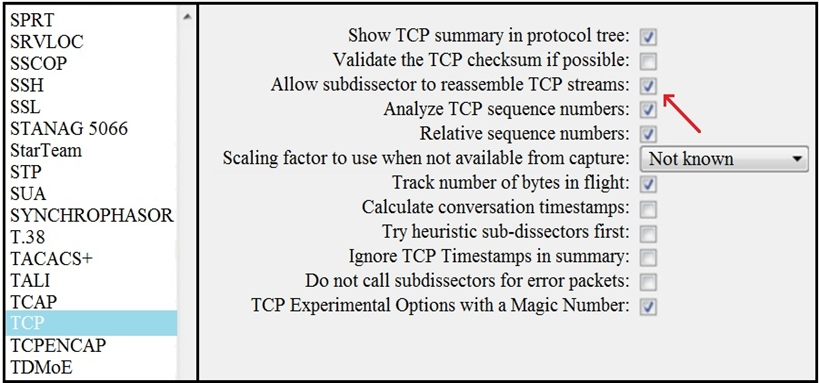
Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
D