A company needs its Amazon Elastic Block Store (Amazon EBS) volumes to be encrypted at all times. During a security incident, EBS snapshots of suspicious instances are shared to a forensics account for analysis. A security engineer attempting to share a suspicious EBS snapshot to the forensics account receives the following error:
`Unable to share snapshot. An error occurred (OperationNotPermitted) when calling the ModifySnapshotAttribute operation: Encrypted snapshots with EBS default key cannot be shared`
Which combination of steps should the security engineer take in the incident account to complete the sharing operation? (Choose three.)
CDE
A company is hosting multiple applications within a single VPC in its AWS account. The applications are running behind an Application Load Balancer that is associated with an AWS WAF web ACL. The company's security team has identified that multiple port scans are originating from a specific range of IP addresses on the internet.
A security engineer needs to deny access from the offending IP addresses.
Which solution will meet these requirements?
D
Reference:
https://docs.aws.amazon.com/waf/latest/developerguide/classic-web-acl-regex-conditions.html
A company plans to create individual child accounts within an existing organization in AWS Organizations for each of its DevOps teams. AWS CloudTrail has been enabled and configured on all accounts to write audit logs to an Amazon S3 bucket in a centralized AWS account. A security engineer needs to ensure that
DevOps team members are unable to modify or disable this configuration.
How can the security engineers meet these requirements?
D
A company has an IAM group. All of the IAM users in the group have been assigned a multi-factor authentication (MFA) device and have full access to Amazon
S3.
The company needs to ensure that users in the group can perform S3 actions only after the users authenticate with MFA. A security engineer must design a solution that accomplishes this goal with the least maintenance overhead.
Which combination of actions will meet these requirements? (Choose two.)
CE
Reference:
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_mfa_configure-api-require.html
A company uses Amazon RDS for MySQL as a database engine for its applications. A recent security audit revealed an RDS instance that is not compliant with company policy for encrypting data at rest. A security engineer at the company needs to ensure that all existing RDS databases are encrypted using server-side encryption and that any future deviations from the policy are detected.
Which combination of steps should the security engineer take to accomplish this? (Choose two.)
DE
A security engineer has been tasked with implementing a solution that allows the company's development team to have interactive command line access to
Amazon EC2 Linux instances using the AWS Management Console.
Which steps should the security engineer take to satisfy this requirement maintaining least privilege?
D
A company's on-premises networks are connected to VPCs using an AWS Direct Connect gateway. The company's on-premises application needs to stream data using an existing Amazon Kinesis Data Firehose delivery stream. The company's security policy requires that data be encrypted in transit using a private network.
How should the company meet these requirements?
B
A company has implemented AWS WAF and Amazon CloudFront for an application. The application runs on Amazon EC2 instances that are part of an Auto
Scaling group. The Auto Scaling group is behind an Application Load Balancer (ALB).
The AWS WAF web ACL uses an AWS Managed Rules rule group and is associated with the CloudFront distribution. CloudFront receives the request from AWS
WAF and the uses the ALB as the distribution's origin.
During a security review, a security engineer discovers that the infrastructure is susceptible to a large, layer 7 DDoS attack.
How can the security engineer improve the security at the edge of the solution to defend against this type of attack?
A
A development team is using an AWS Key Management Service (AWS KMS) CMK to try to encrypt and decrypt a secure string parameter from AWS Systems
Manager Parameter Store. However, the development team receives an error message on each attempt.
Which issues that are related to the CMK could be reasons for the error? (Choose two.)
BE
A company uses AWS Config and AWS Organizations. One of the company's account administrators recently turned off AWS Config recording, and a critical security incident was not logged properly.
The company's security engineer must create an SCP that will deny all users the ability to stop AWS Config. The SCP also must allow the ApprovedAdministrator role to edit AWS Config settings.
Which SCP meets these requirements?
A.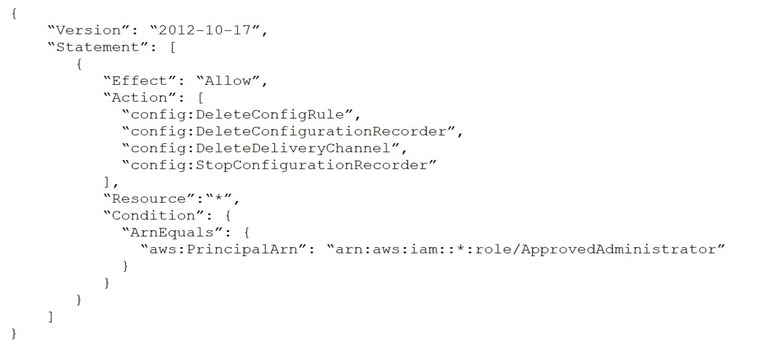
B.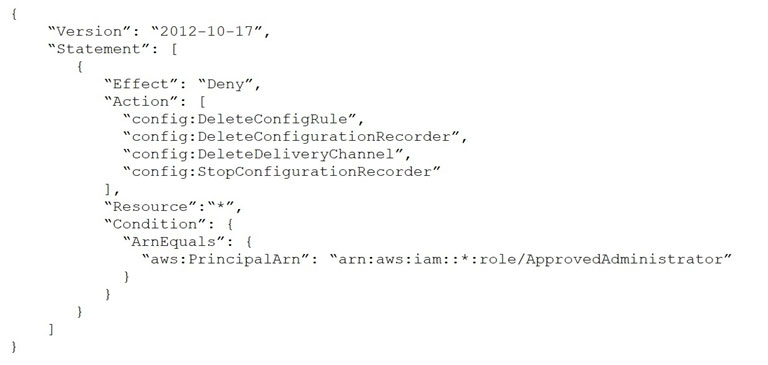
C.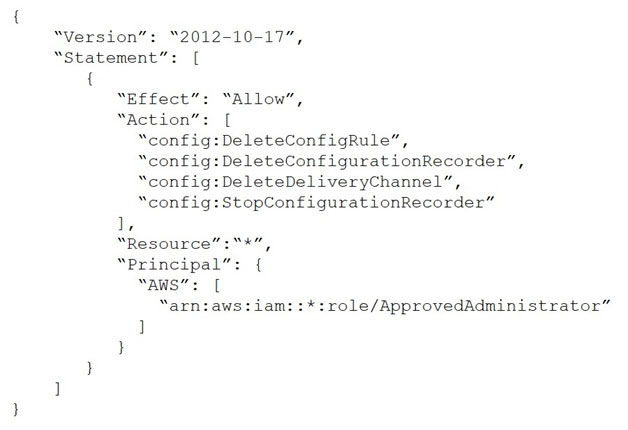
D.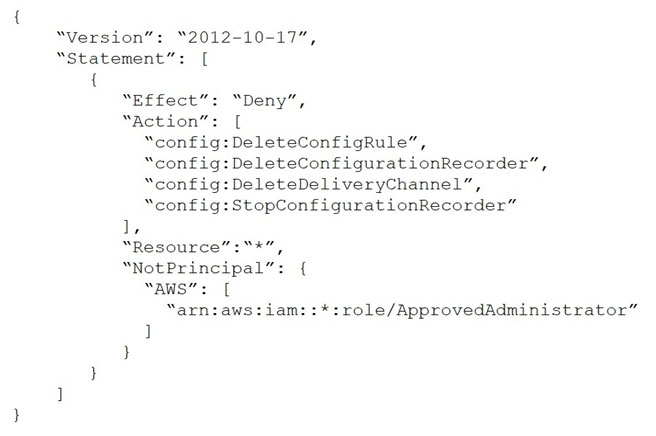
A