A company stores images for a website in an Amazon S3 bucket. The company is using Amazon CloudFront to serve the images to the end users. The company recently discovered that the images are being accessed form countries where the company does not have a distribution license.
Which actions should the company take to secure the images to limit their distribution? (Choose two.)
AE
An audit determined that a company's Amazon EC2 instance security group violated company policy by allowing unrestricted incoming SSH traffic. A security engineer must implement a near-real-time monitoring and alerting solution that will notify administrators of such violations.
Which solution meets these requirements with the MOST operational efficiency?
A
Reference:
https://docs.aws.amazon.com/inspector/latest/userguide/inspector_assessments.html
A large company has hundreds of AWS accounts. The company needs to provide its employees with access to these accounts. The solution must maximize scalability and operational efficiency.
Which solution meets these requirements?
B
A company's security team suspects that an insider threat is present. The security team is basing its suspicion on activity that occurred in one of the company's
AWS accounts. The activity was performed with the AWS account root user credentials. The root user has no access keys. The company uses AWS
Organizations, and the account where the activity occurred is in an OU.
A security engineer needs to take away the root user's ability to make any updates to the account. The root user password cannot be changed to accomplish this goal.
Which solution will meet these requirements?
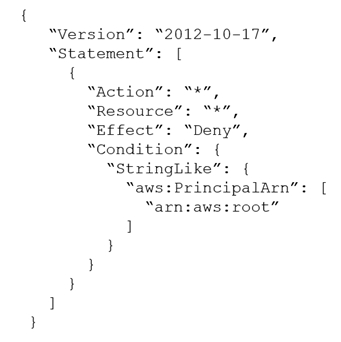
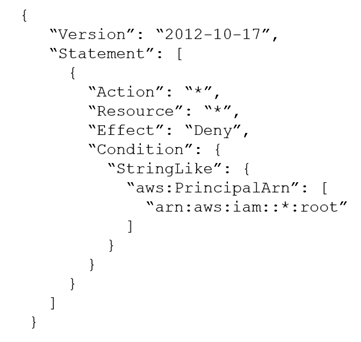
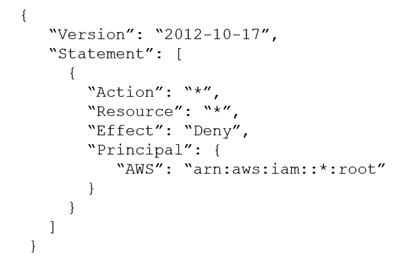
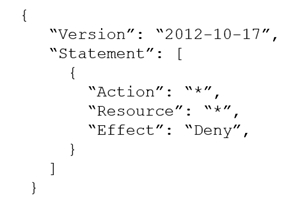
C
A user is implementing a third-party web application on an Amazon EC2 instance. All client communications must be over HTTPS, and traffic must be terminated before it reaches the instance. Communication to the instance must be over port 80. Company policy requires that workloads reside in private subnets.
Which solution meets these requirements?
D
A company uses AWS CodePipeline for its software builds. Company policy mandates that code must be deployed to the staging environment before it is deployed to the production environment. The company needs to implement monitoring and alerting to detect when a CodePipeline pipeline is used to deploy code to production without the code first being deployed to staging.
What should a security engineer do to meet these requirements?
A
An application is running on an Amazon EC2 instance that has an IAM role attached. The IAM role provides access to an AWS Key Management Service (AWS
KMS) customer managed key and an Amazon S3 bucket.
A security engineer discovers a potential vulnerability on the EC2 instance that could result in the compromise of the sensitive data. Due to other critical operations, the security engineer cannot immediately shut down the EC2 instance for vulnerability patching.
What is the FASTEST way to prevent the sensitive data from being exposed?
C
A company stores sensitive documents in Amazon S3 by using server-side encryption with an AWS Key Management Service (AWS KMS) CMK. A new requirement mandates that the CMK that is used for these documents can be used only for S3 actions.
Which statement should the company add to the key policy to meet this requirement?
A.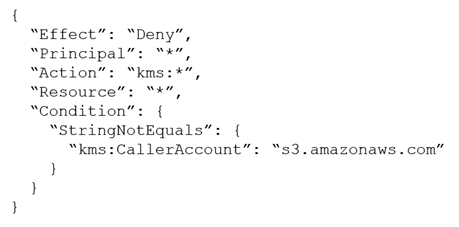
B.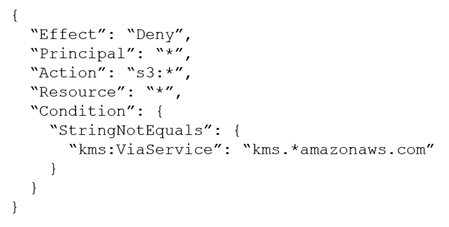
C.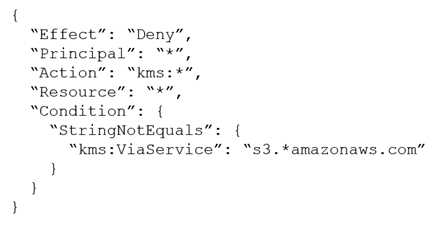
D.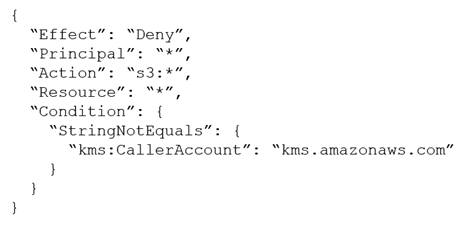
B
A company needs to use HTTPS when connecting to its web applications to meet compliance requirements. These web applications run in Amazon VPC on
Amazon EC2 instances behind an Application Load Balancer (ALB). A security engineer wants to ensure that the load balancer will only accept connections over port 443, even if the ALB is mistakenly configured with an HTTP listener.
Which configuration steps should the security engineer take to accomplish this task?
D
A company maintains an open-source application that is hosted on a public GitHub repository. While creating a new commit to the repository, an engineer uploaded their AWS access key and secret access keys. The engineer reported the mistake to a manager, and the manager immediately disabled the access key.
The company needs to assess the impact of the exposed access key. A security engineer must recommend a solution that requires the least possible managerial overhead.
Which solution meets these requirements?
D
Reference:
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_getting-report.html