A company has developed a new Amazon RDS database application. The company must secure the RDS database credentials for encryption in transit and encryption at rest. The company also must rotate the credentials automatically on a regular basis.
Which solution meets these requirements?
C
A company's development team is designing an application using AWS Lambda and Amazon Elastic Container Service (Amazon ECS). The development team needs to create IAM roles to support these systems. The company's security team wants to allow the developers to build IAM roles directly, but the security team wants to retain control over the permissions the developers can delegate to those roles. The development team needs access to more permissions than those required for application's AWS services. The solution must minimize management overhead.
How should the security team prevent privilege escalation for both teams?
C
A security engineer has enabled AWS Security Hub in their AWS account, and has enabled the Center for Internet Security (CIS) AWS Foundations compliance standard. No evaluation results on compliance are returned in the Security Hub console after several hours. The engineer wants to ensure that Security Hub can evaluate their resources for CIS AWS Foundations compliance.
Which steps should the security engineer take to meet these requirements?
B
Reference:
https://docs.aws.amazon.com/securityhub/latest/userguide/securityhub.pdf
A company has two AWS accounts: Account A and Account B. Account A has an IAM role that IAM users in Account B assume when they need to upload sensitive documents to Amazon S3 buckets in Account A.
A new requirement mandates that users can assume the role only if they are authenticated with multi-factor authentication (MFA). A security engineer must recommend a solution that meets this requirement with minimum risk and effort.
Which solution should the security engineer recommend?
D
A company is developing an ecommerce application. The application uses Amazon EC2 instances and an Amazon RDS MySQL database. For compliance reasons, data must be secured in transit and at rest. The company needs a solution that minimizes operational overhead and minimizes cost.
Which solution meets these requirements?
A
Reference:
https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.SSL.html
A company is undergoing a layer 3 and layer 4 DDoS attack on its web servers running on AWS.
Which combination of AWS services and features will provide protection in this scenario? (Choose three.)
ACD
Reference:
https://aws.amazon.com/shield/?whats-new-cards.sort-by=item.additionalFields.postDateTime&whats-new-cards.sort-order=desc
A user in account 111122223333 is receiving an access denied error message while calling the AWS Key Management Service (AWS KMS) GenerateDataKey
API operation. The key policy contains the following statement: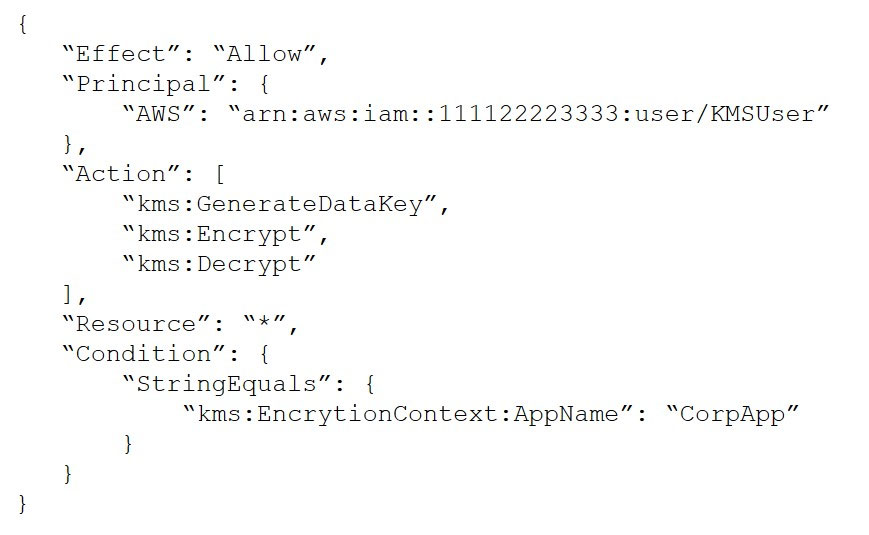
Account 111122223333 is not using AWS Organizations SCPs.
Which combination of steps should a security engineer take to ensure that KMSUser can perform the action on the key? (Choose two.)
AC
A company is building an application on AWS that will store sensitive information. The company has a support team with access to the IT infrastructure, including databases. The company's security engineer must introduce measures to protect the sensitive data against any data breach while minimizing management overhead. The credentials must be regularly rotated.
What should the security engineer recommend?
D
A company is developing a mobile shopping web app. The company needs an environment that is configured to encrypt all resources in transit and at rest.
A security engineer must develop a solution that will encrypt traffic in transit to the company's Application Load Balancer and Amazon API Gateway resources.
The solution also must encrypt traffic at rest for Amazon S3 storage.
What should the security engineer do to meet these requirements?
A
A security team is implementing a centralized logging solution to meet requirements for auditing. The solution must be able to aggregate logs from Amazon
CloudWatch and AWS CloudTrail to an account that is controlled by the security team. This approach must be usable across the entire organization in AWS
Organizations.
Which solution meets these requirements in the MOST operationally efficient manner?
A