Unapproved changes were previously made to a company's Amazon S3 bucket. A security engineer configured AWS Config to record configuration changes made to the company's S3 buckets. The engineer discovers there are S3 configuration changes being made, but no Amazon SNS notifications are being sent. The engineer has already checked the configuration of the SNS topic and has confirmed the configuration is valid.
Which combination of steps should the security engineer take to resolve the issue? (Choose two.)
AD
Reference:
https://aws.amazon.com/blogs/security/how-to-use-aws-config-to-monitor-for-and-respond-to-amazon-s3-buckets-allowing-public-access/
A security engineer must develop an encryption tool for a company. The company requires a cryptographic solution that supports the ability to perform cryptographic erasure on all resources protected by the key material in 15 minutes or less.
Which Aws Key Management Service (AWS KMS) key solution will allow the security engineer to meet these requirements?
A
A company deployed an Amazon EC2 instance to a VPC on AWS. A recent alert indicates that the EC2 instance is receiving a suspicious number of requests over an open TCP port from an external source. The TCP port remains open for long periods of time.
The company's security team needs to stop all activity to this port from the external source to ensure that the EC2 instance is not being compromised. The application must remain available to other users.
Which solution will meet these requirements?
D
After a recent security audit involving Amazon S3, a company has asked for assistance reviewing its S3 buckets to determine whether the data is properly secured. The first S3 bucket on the list has the following bucket policy: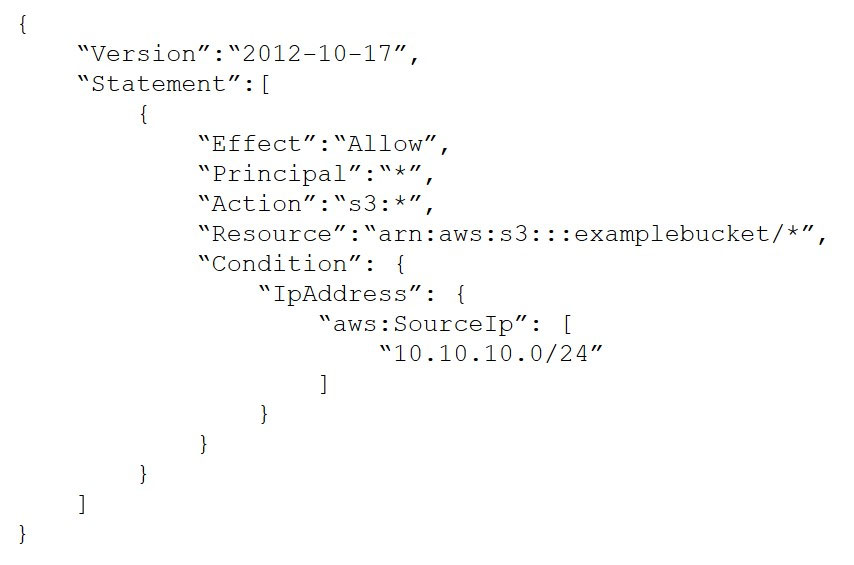
In this bucket policy sufficient to ensure that the data is not publicly accessible?
A
A security engineer needs to build a solution to turn AWS CloudTrail back on in multiple AWS Regions in case it is ever turned off.
What is the MOST efficient way to implement this solution?
C
A company needs to encrypt all of its data stored in Amazon S3. The company wants to use AWS Key Management Service (AWS KMS) to create and manage its encryption keys. The company's security policies require the ability to import the company's own key material for the keys, set an expiration date on the keys, and delete keys immediately, if needed.
How should a security engineer set up AWS KMS to meet these requirements?
A
Reference:
https://docs.aws.amazon.com/kms/latest/developerguide/overview.html
A company has an application that uses an Amazon RDS PostgreSQL database. The company is developing an application feature that will store sensitive information for an individual in the database.
During a security review of the environment, the company discovers that the RDS DB instance is not encrypting data at rest. The company needs a solution that will provide encryption at rest for all the existing data and for any new data that is entered for an individual.
Which combination of options can the company use to meet these requirements? (Choose two.)
AD
Reference:
https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/USER_CopySnapshot.html
A security engineer needs to create an Amazon S3 bucket policy to grant least privilege read access to IAM user accounts that are named User1, User2 and
User3. These IAM user accounts are members of the AuthorizedPeople IAM group. The security engineer drafts the following S3 bucket policy: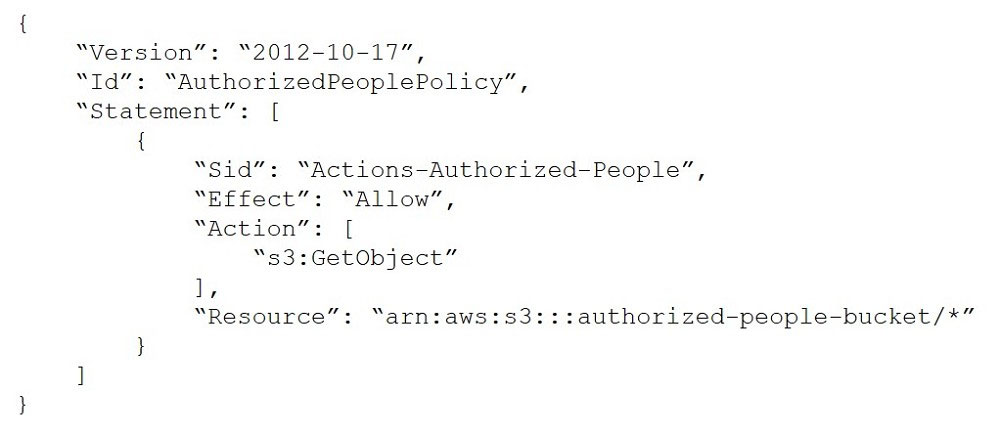
When the security engineer tries to add the policy to the S3 bucket, the following message appears: `Missing required field Principal.`
The security engineer is adding a Principal element to the policy. The addition must provide read access to only User1, User2 and User3.
Which solution meets these requirements?
A.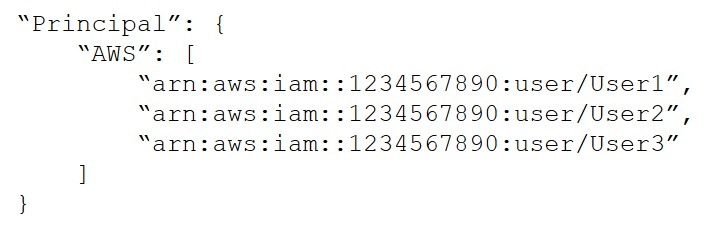
B.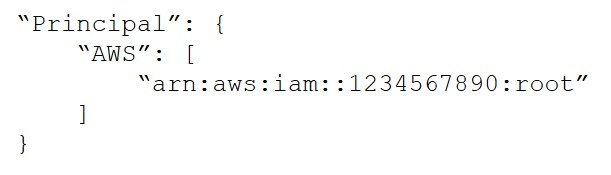
C.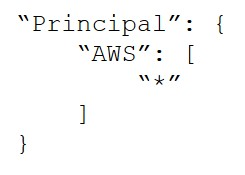
D.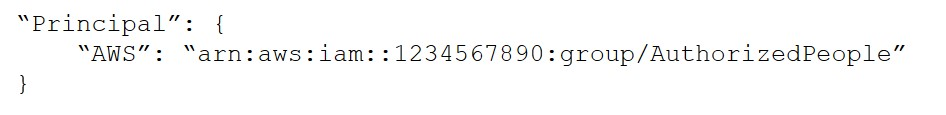
B
Reference:
https://docs.amazonaws.cn/en_us/AmazonS3/latest/userguide/example-bucket-policies.html
A company is hosting a web application on Amazon EC2 instances behind an Application Load Balancer (ALB). The application has become the target of a DoS attack. Application logging shows that requests are coming from small number of client IP addresses, but the addresses change regularly.
The company needs to block the malicious traffic with a solution that requires the least amount of ongoing effort.
Which solution meets these requirements?
A
Reference:
https://docs.aws.amazon.com/whitepapers/latest/aws-best-practices-ddos-resiliency/aws-best-practices-ddos-resiliency.pdf
A public subnet contains two Amazon EC2 instances. The subnet has a custom network ACL. A security engineer is designing a solution to improve the subnet security.
The solution must allow outbound traffic to an internet service that uses TLS through port 443. The solution also must deny inbound traffic that is destined for
MySQL port 3306.
Which network ACL rule set meets these requirements?
A