A company uses an AWS Key Management Service (AWS KMS) CMK to encrypt application data before it is stored. The company's security policy was recently modified to require encryption key rotation annually. A security engineer must ensure that annual global key rotation is enabled for the key without making changes to the application.
What should the security engineer do to accomplish this requirement?
D
Reference:
https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html
A company is collecting AWS CloudTrail log data from multiple AWS accounts by managing individual trails in each account and forwarding log data to a centralized Amazon S3 bucket residing in a log archive account. After CloudTrail introduced support for AWS Organizations trails, the company decided to further centralize management and automate deployment of the CloudTrail logging capability across all of its AWS accounts.
The company's security engineer created an AWS Organizations trail in the master account, enabled server-side encryption with AWS KMS managed keys (SSE-
KMS) for the log files, and specified the same bucket as the storage location. However, the engineer noticed that logs recorded by the new trail were not delivered to the bucket.
Which factors could cause this issue? (Choose two.)
AD
A company's AWS CloudTrail logs are all centrally stored in an Amazon S3 bucket. The security team controls the company's AWS account. The security team must prevent unauthorized access and tampering of the CloudTrail logs.
Which combination of steps should the security team take? (Choose three.)
BCE
A company needs to migrate several applications to AWS. This will require storing more than 5,000 credentials. To meet compliance requirements, the company will use its existing password management system for key rotation, auditing, and integration with third-party secrets containers. The company has a limited budget and is seeking the most cost-effective solution that is still secure.
How should the company accomplish this at the LOWEST cost?
D
A company has a web-based application using Amazon CloudFront and running on Amazon Elastic Container Service (Amazon ECS) behind an Application Load
Balancer (ALB). The ALB is terminating TLS and balancing load across ECS service tasks. A security engineer needs to design a solution to ensure that application content is accessible only through CloudFront and that it is never accessible directly.
How should the security engineer build the MOST secure solution?
C
A large government organization is moving to the cloud and has specific encryption requirements. The first workload to move requires that a customer's data be immediately destroyed when the customer makes that request.
Management has asked the security team to provide a solution that will securely store the data, allow only authorized applications to perform encryption and decryption, and allow for immediate destruction of the data.
Which solution will meet these requirements?
A
A security engineer is defining the controls required to protect the AWS account root user credentials in an AWS Organizations hierarchy. The controls should also limit the impact in case these credentials have been compromised.
Which combination of controls should the security engineer propose? (Choose three.)
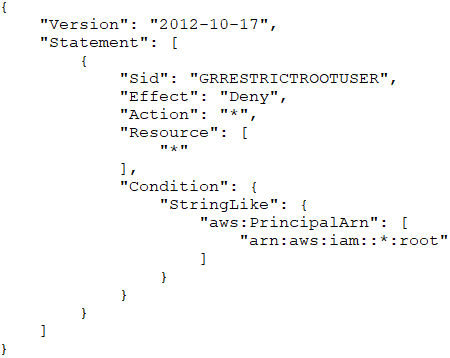
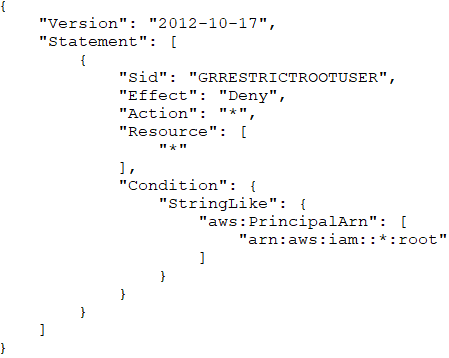
ADF
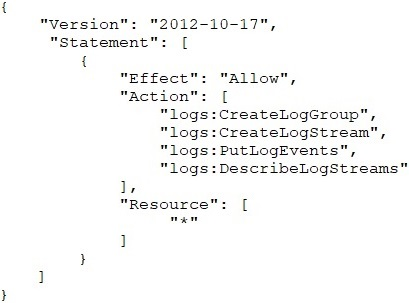
A VPC endpoint for Amazon CloudWatch Logs was recently added to a company's VPC. The company's system administrator has verified that private DNS is enabled and that the appropriate route tables and security groups have been updated. The role attached to the Amazon EC2 instance is: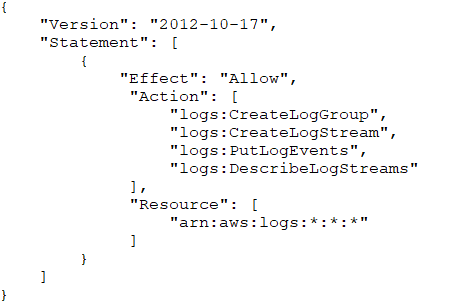
The CloudWatch Logs agent is running and attempting to write to a CloudWatch Logs stream in the same AWS account. However, no logs are being updated in
CloudWatch Logs.
What is the likely cause of this issue?
C
Amazon GuardDuty has detected communications to a known command and control endpoint from a company's Amazon EC2 instance. The instance was found to be running a vulnerable version of a common web framework. The company's security operations team wants to quickly identify other compute resources with the specific version of that framework installed.
Which approach should the team take to accomplish this task?
B
A security engineer has noticed an unusually high amount of traffic coming from a single IP address. This was discovered by analyzing the Application Load
Balancer's access logs.
How can the security engineer limit the number of requests from a specific IP address without blocking the IP address?
B