HOTSPOT -
Your company uses Microsoft Defender for Cloud Apps.
You plan to integrate Defender for Cloud Apps and security information and event management (SIEM).
You need to deploy a SIEM agent on a server that runs Windows Server 2016.
What should you do? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: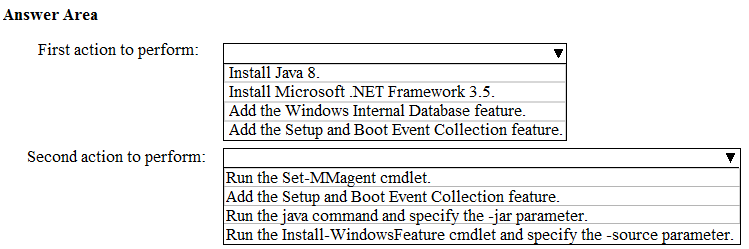
Answer:
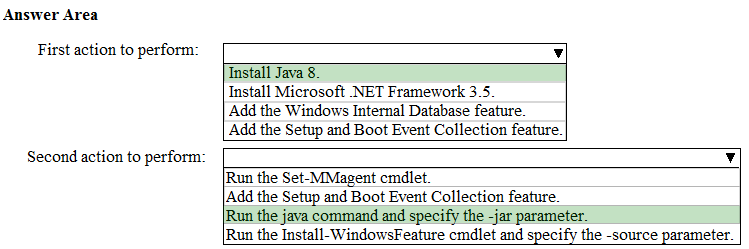
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/integrate-your-siem-server-with-office-365-cas
HOTSPOT -
From the Microsoft Azure Active Directory (Azure AD) Identity Protection dashboard, you view the risk events shown in the following exhibit.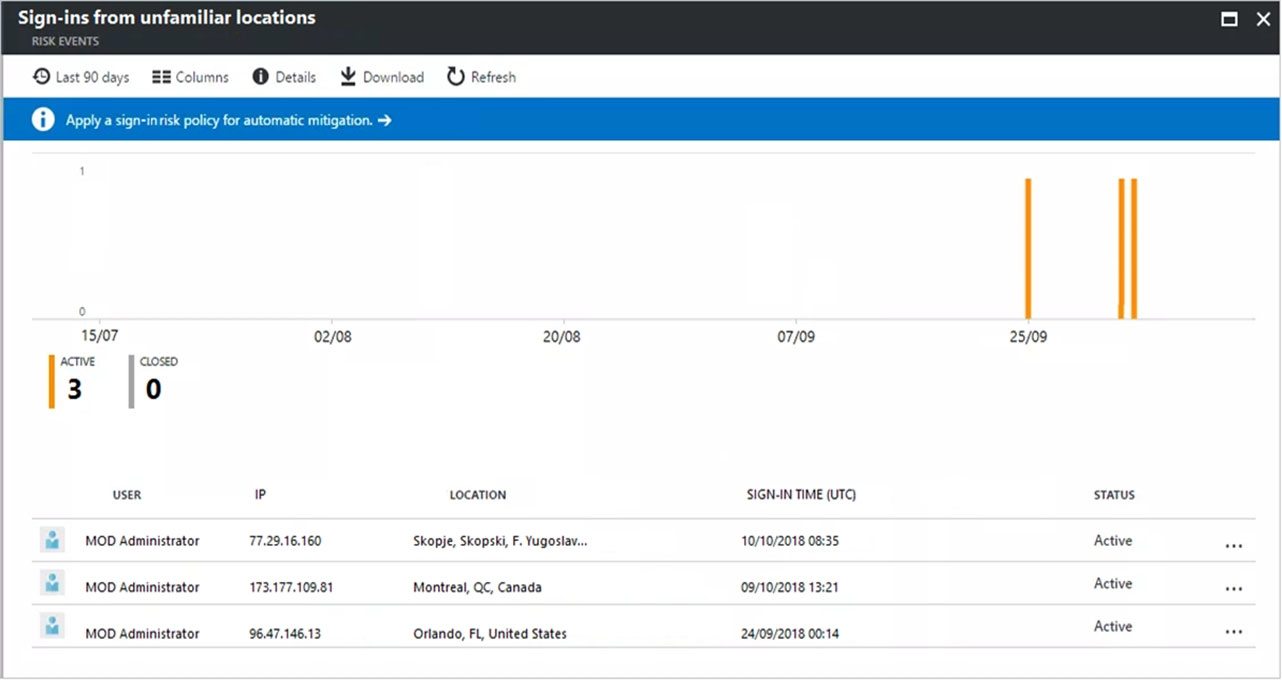
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-getstarted https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-sign-in-risk-policy https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/quickstart-configure-named-locations
Your company uses Microsoft Defender for Identity and Microsoft 365 Defender for Endpoint.
You need to integrate Microsoft Defender for Identity and Microsoft 365 Defender for Endpoint.
What should you do?
Answer:
B
Reference:
https://blog.ahasayen.com/azure-atp-and-windows-defender-atp-integration/
HOTSPOT -
You have a Microsoft Azure Activity Directory (Azure AD) tenant that contains the users shown in the following table.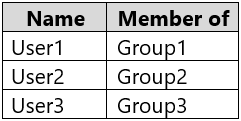
Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint contains the roles shown in the following table.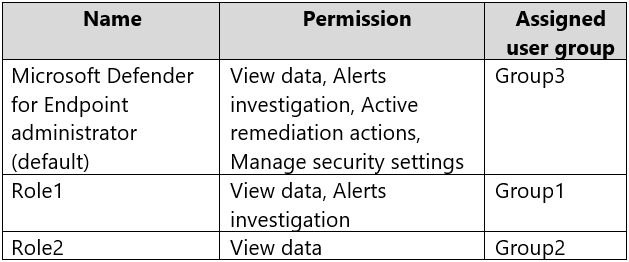
Microsoft Defender for Endpoint contains the device groups shown in the following table.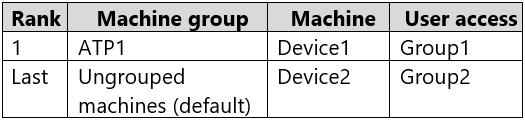
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
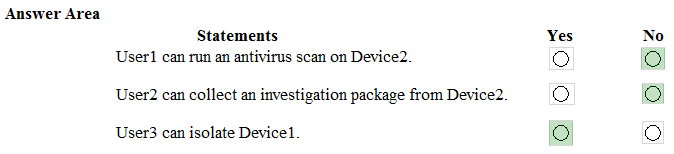
References:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-atp/user-roles-windows-defender-advanced-threat-protection
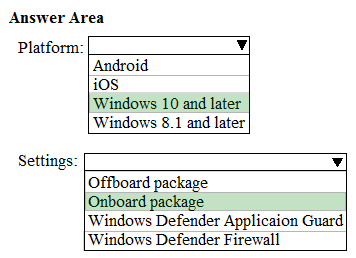
HOTSPOT -
You have a Microsoft 365 subscription. All client devices are managed by Microsoft Endpoint Manager.
You need to implement Microsoft Defender Advanced Threat Protection (ATP) for all the supported devices enrolled in mobile device management (MDM).
What should you include in the device configuration profile? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: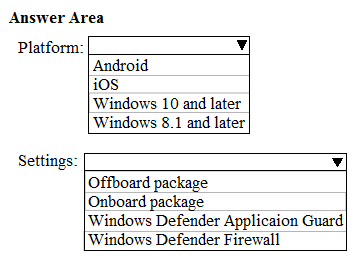
Answer:
Reference:
https://docs.microsoft.com/en-us/intune/advanced-threat-protection
You have a Microsoft 365 subscription.
Your company purchases a new financial application named App1.
From Cloud Discovery in Microsoft Defender for Cloud Apps, you view the Discovered apps page and discover that many applications have a low score because they are missing information about domain registration and consumer popularity.
You need to prevent the missing information from affecting the App1 score.
What should you configure from the Cloud Discover settings?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/getting-started-with-cloud-app-security
You have a Microsoft 365 E5 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/office365/servicedescriptions/exchange-online-service-description/anti-spam-and-anti-malware-protection
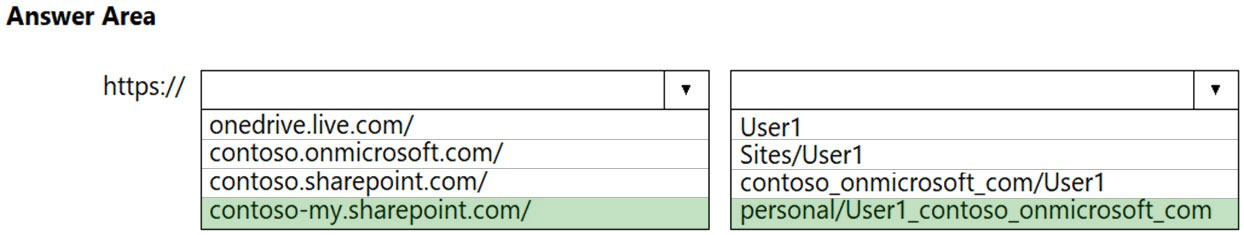
HOTSPOT -
You have a Microsoft 365 subscription that links to an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
A user named User1 stores documents in Microsoft OneDrive.
You need to place the contents of User1's OneDrive account on an eDiscovery hold.
Which URL should you use for the eDiscovery hold? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: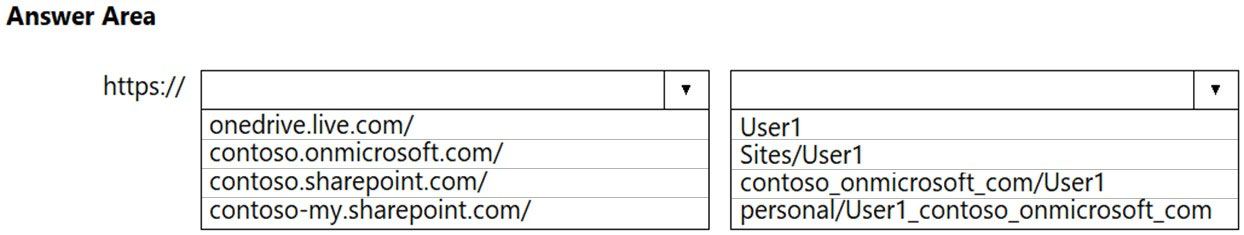
Answer:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/create-ediscovery-holds
HOTSPOT -
You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant. The tenant contains a group named Group1 and the users shown in the following table: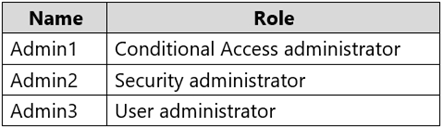
The tenant has a conditional access policy that has the following configurations:
✑ Name: Policy1
✑ Assignments:
- Users and groups: Group1
- Cloud aps or actions: All cloud apps
✑ Access controls:
✑ Grant, require multi-factor authentication
✑ Enable policy: Report-only
You set Enabled Security defaults to Yes for the tenant.
For each of the following settings select Yes, if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: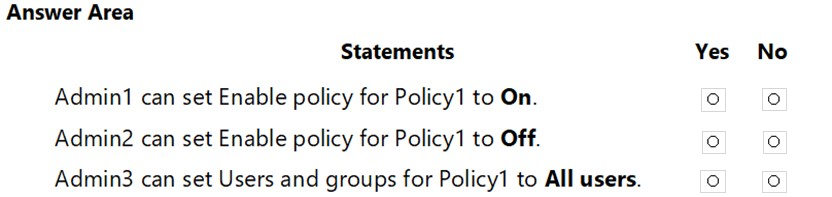
Answer:
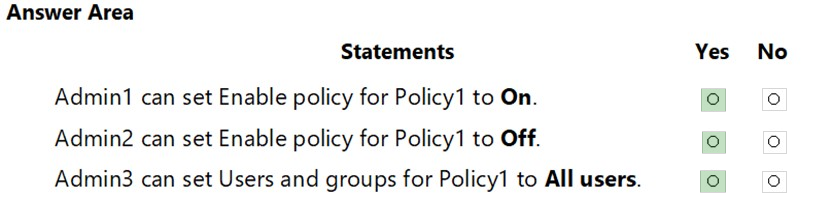
Report-only mode is a new Conditional Access policy state that allows administrators to evaluate the impact of Conditional Access policies before enabling them in their environment. With the release of report-only mode:
✑ Conditional Access policies can be enabled in report-only mode.
✑ During sign-in, policies in report-only mode are evaluated but not enforced.
✑ Results are logged in the Conditional Access and Report-only tabs of the Sign-in log details.
✑ Customers with an Azure Monitor subscription can monitor the impact of their Conditional Access policies using the Conditional Access insights workbook.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-report-only
Your network contains an on-premises Active Directory domain.
Your company has a security policy that prevents additional software from being installed on domain controllers.
You need to monitor a domain controller by using Microsoft Defender for Identity.
What should you do? More than one answer choice may achieve the goal. Choose the BEST answer.
Answer:
D
We cannot install additional software on the domain controllers. Azure ATP Standalone Sensor is a full agent installed on a dedicated server that can monitor traffic from multiple domain controllers. This is an alternative to those that do not wish to install an agent directly on a domain controller.
Incorrect Answers:
A, B: Azure ATP Sensor is a lightweight agent installed directly on a domain controller to monitor and report traffic. However, we cannot install additional software on the domain controllers
Reference:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/install-atp-step5 https://docs.microsoft.com/en-us/defender-for-identity/configure-port-mirroring https://blog.enablingtechcorp.com/secure-and-monitor-domain-controllers-with-azure-atp