HOTSPOT -
Your company has a Microsoft 365 subscription.
You need to configure Microsoft 365 to meet the following requirements:
✑ Malware found in email attachments must be quarantined for 20 days.
✑ The email address of senders to your company must be verified.
Which two options should you configure in the Security & Compliance admin center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: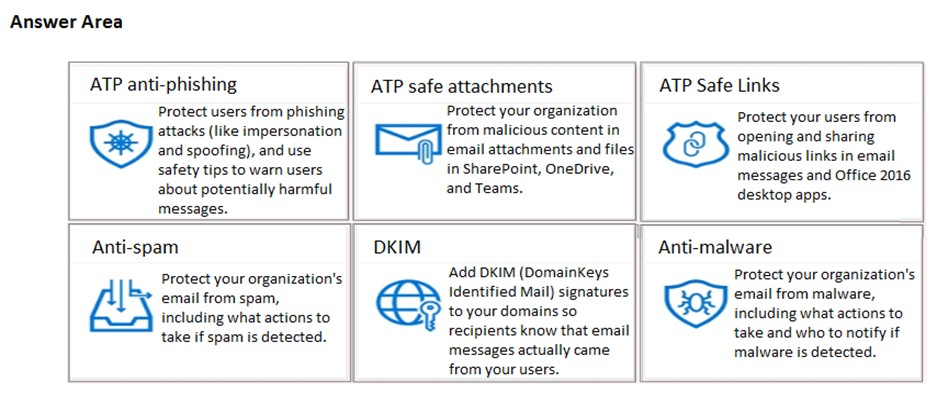
Answer:
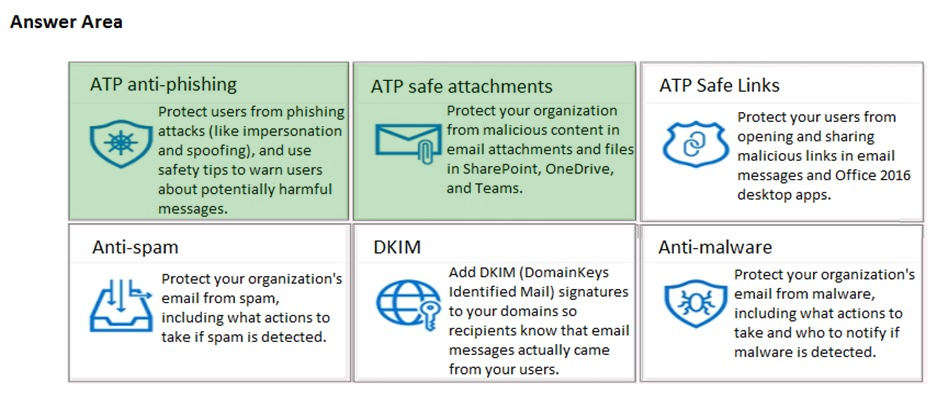
You have a Microsoft 365 subscription that uses Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
All the devices in your organization are onboarded to Microsoft Defender ATP.
You need to ensure that an alert is generated if malicious activity was detected on a device during the last 24 hours.
What should you do?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/custom-detection-rules
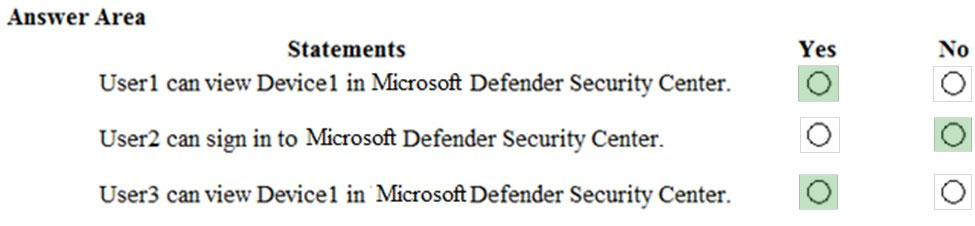
You have an Azure Active Directory (Azure AD) tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.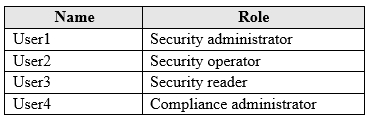
You plan to implement Microsoft Defender for Endpoint.
You verify that role-based access control (RBAC) is turned on in Microsoft Defender for Endpoint.
You need to identify which user can view security incidents from the Microsoft Defender Security Center.
Which user should you identify?
Answer:
A
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices.
You perform a proof of concept (PoC) deployment of Microsoft Defender for Endpoint for 10 test devices. During the onboarding process, you configure Microsoft
Defender for Endpoint-related data to be stored in the United States.
You plan to onboard all the devices to Microsoft Defender for Endpoint.
You need to store the Microsoft Defender for Endpoint data in Europe.
What should you do first?
Answer:
D
You have a Microsoft 365 subscription.
You need to be notified if users receive email containing a file that has a virus.
What should you do?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/office365/servicedescriptions/exchange-online-service-description/anti-spam-and-anti-malware-protection
You have a Microsoft 365 subscription that contains 500 users.
You have several hundred computers that run the 64-bit version of Windows 10 Enterprise and have the following configurations:
✑ Two volumes that contain data
✑ A CPU that has two cores
✑ TPM disabled
✑ 4 GB of RAM
All the computers are managed by using Microsoft Endpoint Manager.
You need to ensure that you can turn on Windows Defender Application Guard on the computers.
What should you do first?
Answer:
D
The computers need 4 CPU cores and 8GB of RAM.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-guard/reqs-wd-app-guard
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
From Microsoft Defender for Endpoint, you turn on the Allow or block file advanced feature.
You need to block users from downloading a file named File1.exe.
What should you use?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-atp/respond-file-alerts#allow-or-block-file
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
When users attempt to access the portal of a partner company, they receive the message shown in the following exhibit.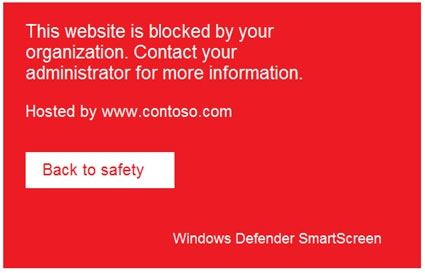
You need to enable user access to the partner company's portal.
Which Microsoft Defender for Endpoint setting should you modify?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/manage-indicators?view=o365-worldwide
HOTSPOT -
You have a Microsoft 365 subscription.
You create a Microsoft Defender for Cloud Apps policy named Risk1 based on the Logon from a risky IP address template as shown in the following exhibit.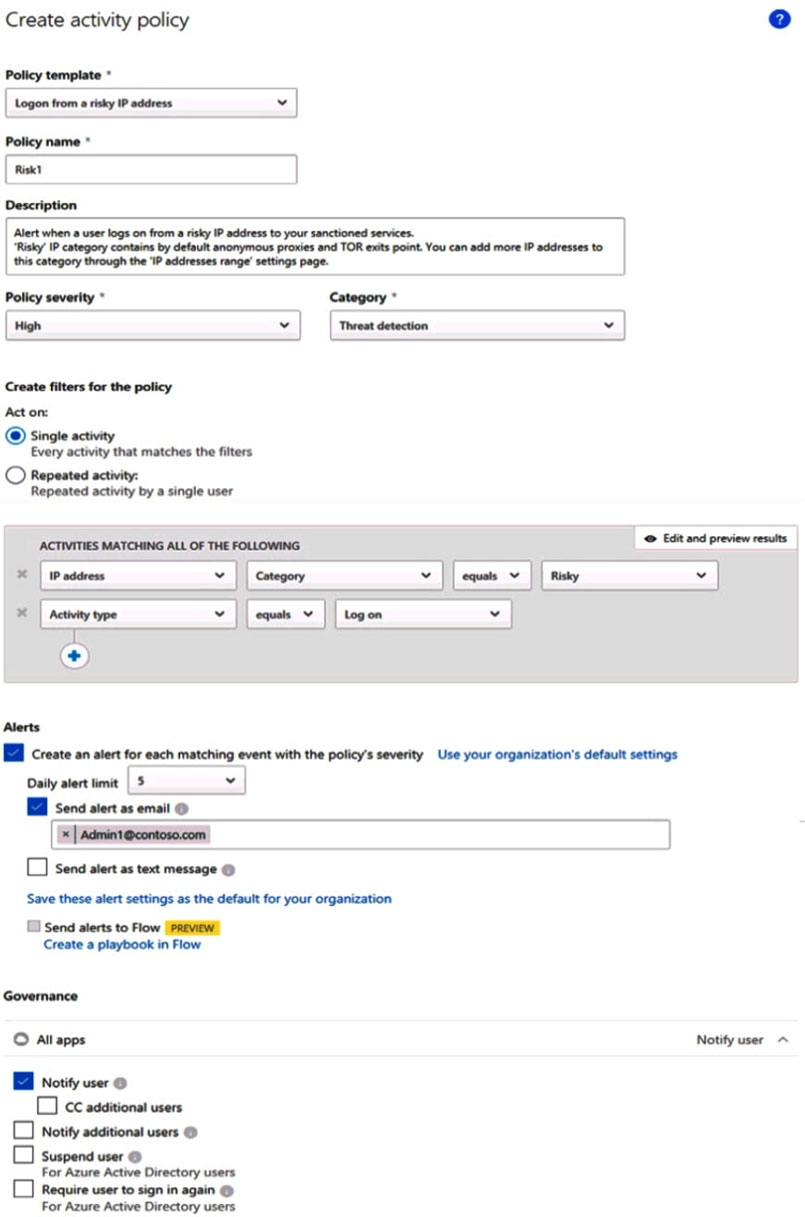
You have two users named User1 and User2. Each user signs in to Microsoft SharePoint Online from a risky IP address 10 times within 24 hours.
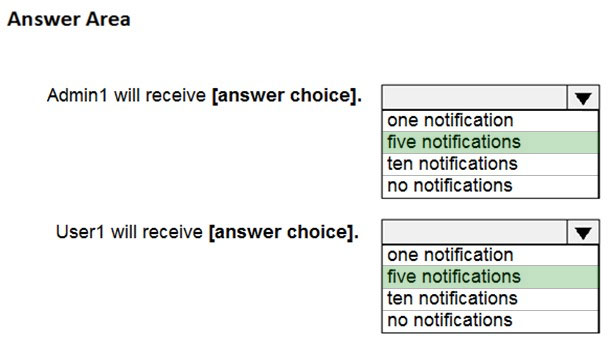
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
HOTSPOT -
You have a Microsoft Azure Activity Directory (Azure AD) tenant contains the users shown in the following table.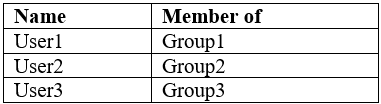
Group3 is a member of Group1.
Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the roles shown in the following table.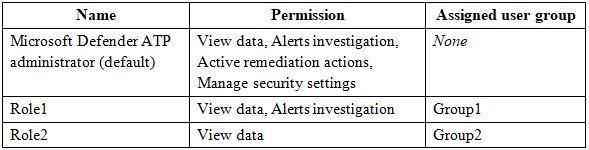
Microsoft Defender ATP contains the device groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer: