You have a Microsoft 365 tenant.
You discover that administrative tasks are unavailable in the Microsoft 365 audit logs of the tenant.
You run the Get-AdminAuditLogConfig cmdlet and receive the following output: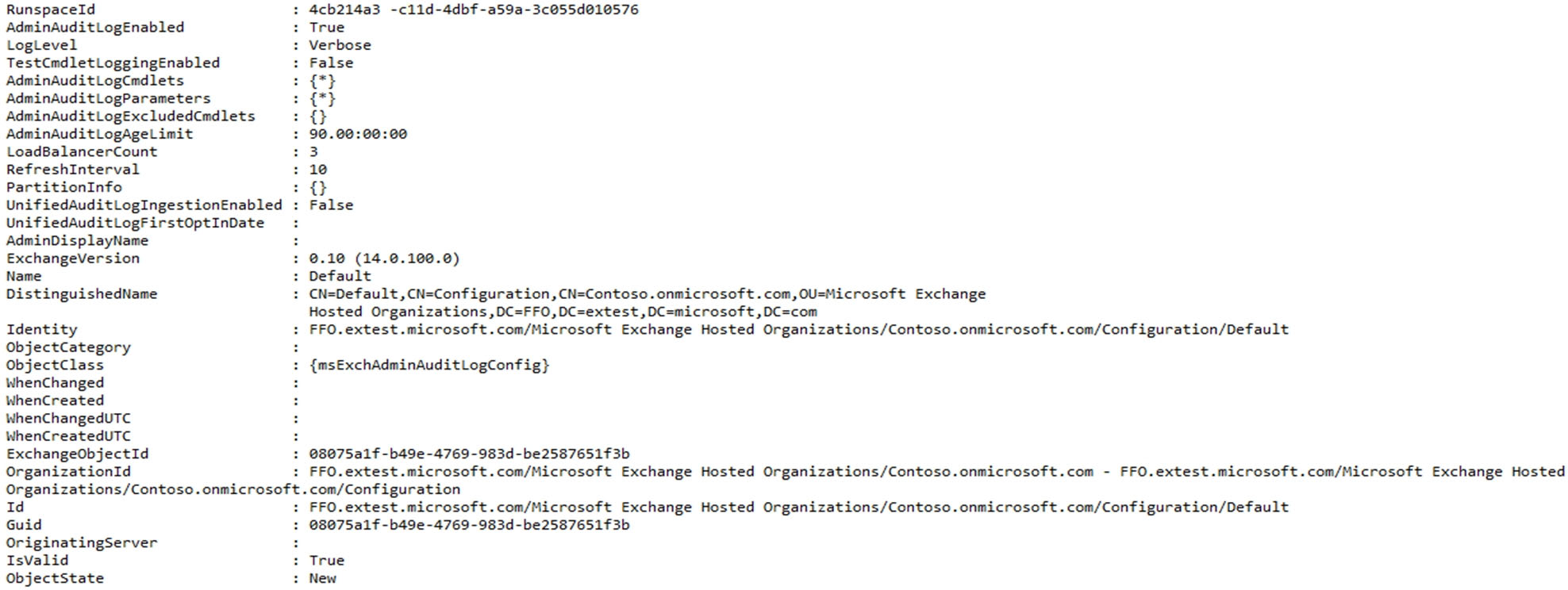
You need to ensure that administrative tasks are logged in the Microsoft 365 audit logs.
Which attribute should you modify?
Answer:
B
References:
https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/set-adminauditlogconfig?view=exchange-ps
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a new Microsoft 365 subscription.
You need to prevent users from sending email messages that contain Personally Identifiable Information (PII).
Solution: From the Microsoft 365 compliance center, you create a data loss prevention (DLP) policy.
Does this meet the goal?
Answer:
A
In Microsoft 365, you can create a data loss prevention (DLP) policy in two different admin centers:
✑ In the Security & Compliance admin center (now known as the Microsoft 365 Compliance Center), you can create a single DLP policy to help protect content in
SharePoint, OneDrive, Exchange, Teams, and now Endpoint Devices.
✑ In the Exchange admin center, you can create a DLP policy to help protect content only in Exchange.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/how-dlp-works-between-admin-centers?view=o365-worldwide
Your company has a Microsoft 365 tenant.
The company sells products online and processes credit card information.
You need to be notified if a file stored in Microsoft SharePoint Online contains credit card information. The file must be removed automatically from its current location until an administrator can review its contents.
What should you use?
Answer:
A
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/data-loss-prevention-policies
HOTSPOT -
You configure an anti-phishing policy as shown in the following exhibit.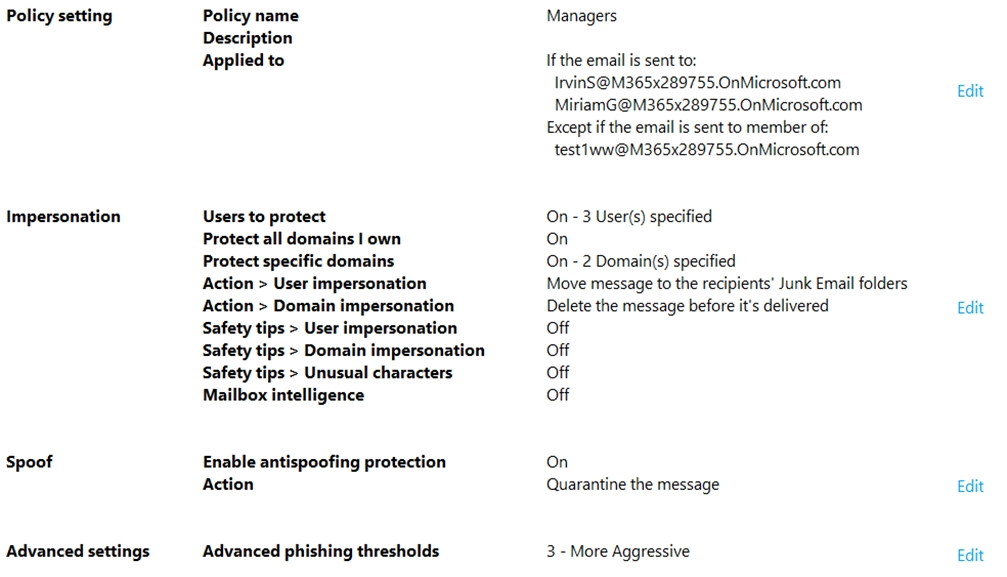
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: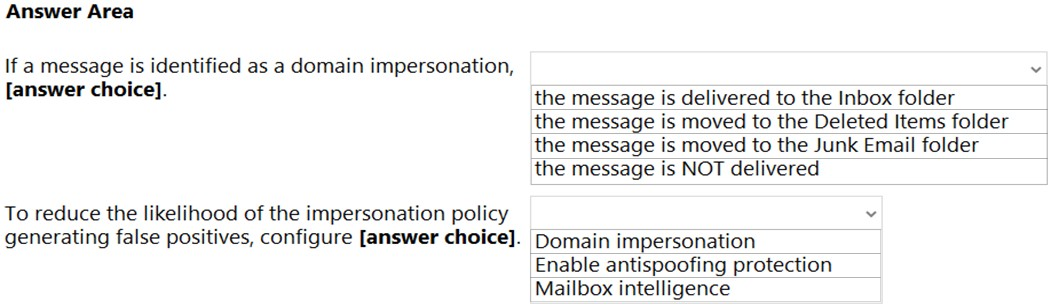
Answer:
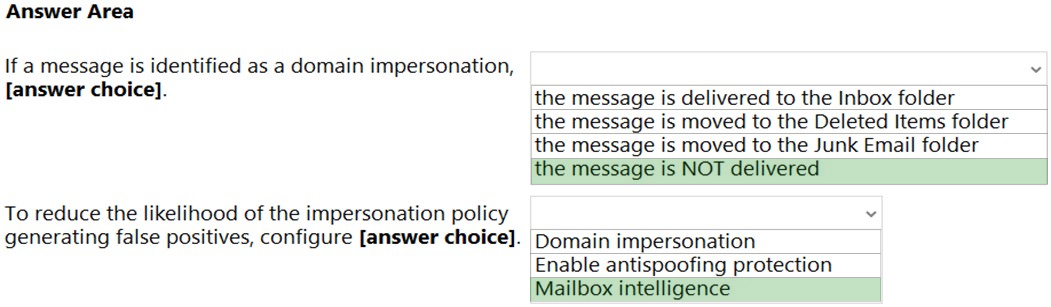
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/set-up-anti-phishing-policies#learn-about-atp-anti-phishing-policy-options
You need to notify the manager of the human resources department when a user in the department shares a file or folder from the department's Microsoft
SharePoint Online site.
What should you do?
Answer:
A
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/create-activity-alerts
HOTSPOT -
You have a Microsoft 365 subscription.
You are configuring permissions for Security & Compliance.
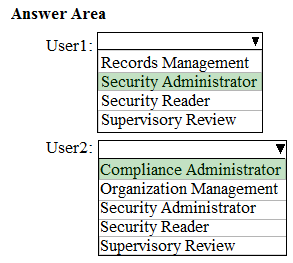
You need to ensure that the users can perform the tasks shown in the following table.
The solution must use the principle of least privilege.
To which role should you assign each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: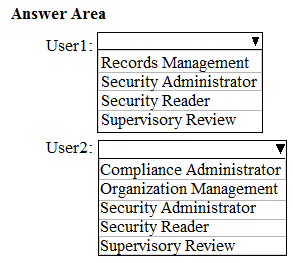
Answer:
References:
https://docs.microsoft.com/en-us/office365/securitycompliance/permissions-in-the-security-and-compliance-center#mapping-of-role-groups-to-assigned-roles
HOTSPOT -
You have a Microsoft Azure Active Directory (Azure AD) tenant.
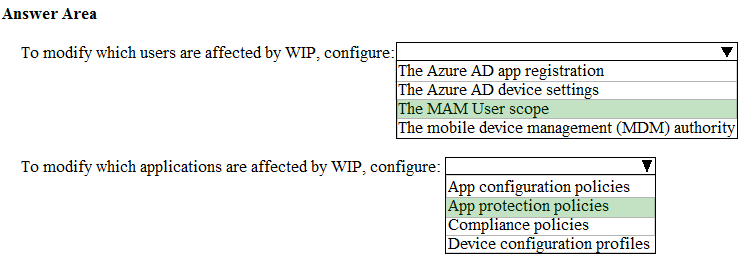
Your company implements Windows Information Protection (WIP).
You need to modify which users and applications are affected by WIP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: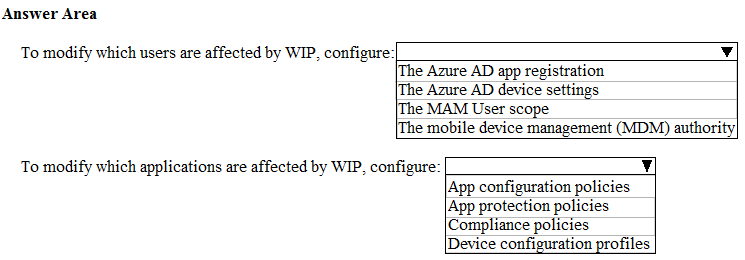
Answer:
References:
https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/create-wip-policy-using-intune-azure
HOTSPOT -
You have a Microsoft 365 subscription.
All users are assigned Microsoft Azure Active Directory Premium licenses.
From the Device Management admin center, you set Microsoft Intune as the MDM authority.
You need to ensure that when the members of a group named Marketing join a device to Azure Active Directory (Azure AD), the device is enrolled automatically in
Intune. The Marketing group members must be limited to five devices enrolled in Intune.
Which two options should you use to perform the configurations? To answer, select the appropriate blades in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: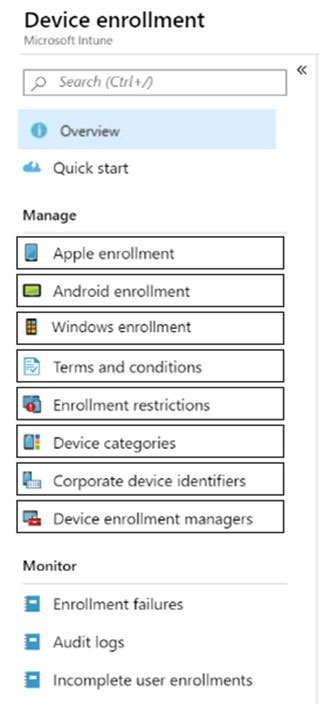
Answer:
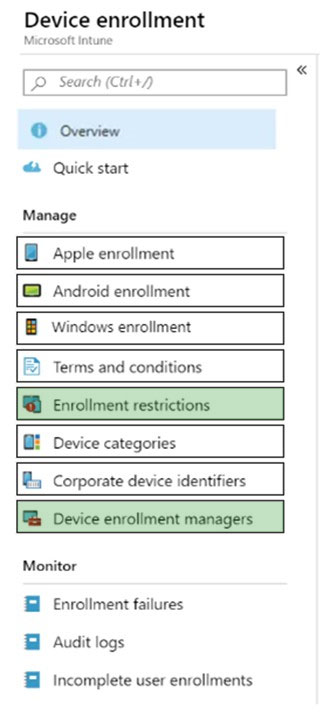
Device enrollment manager (DEM) is an Intune permission that can be applied to an Azure AD user account and lets the user enroll up to 1,000 devices
You can create and manage enrollment restrictions that define what devices can enroll into management with Intune, including the:
✑ Number of devices.
✑ Operating systems and versions.
The Marketing group members must be limited to five devices enrolled in Intune
References:
https://docs.microsoft.com/en-us/intune/enrollment/device-enrollment-manager-enroll https://docs.microsoft.com/en-us/intune/enrollment/enrollment-restrictions-set
You have a Microsoft 365 subscription.
You plan to enable Microsoft Azure Information Protection.
You need to ensure that only the members of a group named PilotUsers can protect content.
What should you do?
Answer:
C
Reference:
https://blogs.technet.microsoft.com/kemckinn/2018/05/17/creating-labels-for-azure-information-protection/
Your company has a Microsoft 365 subscription.
You need to identify which users performed the following privileged administration tasks:
✑ Deleted a folder from the second-stage Recycle Bin of Microsoft SharePoint
✑ Opened a mailbox of which the user was not the owner
✑ Reset a user password
What should you use?
Answer:
A
You can view the required information in the audit logs. The Azure AD audit logs provide records of system activities for compliance. To access the audit report, select Audit logs in the Activity section of Azure Active Directory.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/reports-monitoring/concept-audit-logs https://docs.microsoft.com/en-us/azure/azure-monitor/platform/activity-logs-overview