HOTSPOT -
You have a Microsoft 365 subscription that contains three groups named All users, Sales team, and Office users, and two users shown in the following table.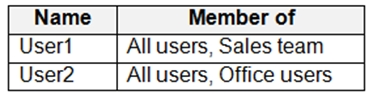
In Microsoft Endpoint Manager, you have the Policies for Office apps settings shown in the following exhibit.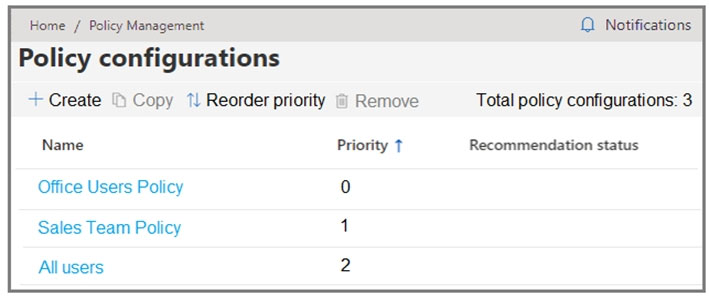
The policies use the settings shown in the following table.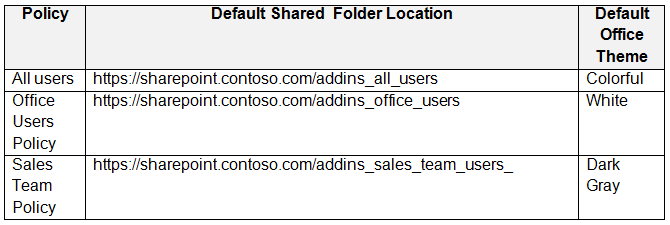
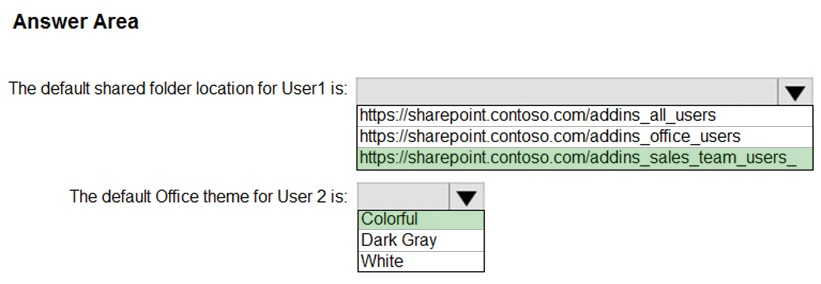
What is the default share folder location for User1 and the default Office theme for User2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: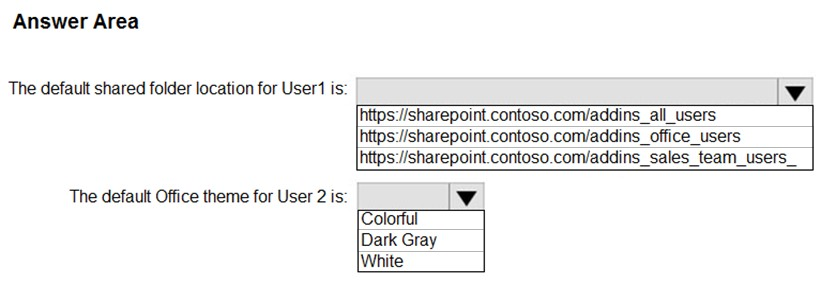
Answer:
Reference:
https://docs.microsoft.com/en-us/deployoffice/overview-office-cloud-policy-service
You have a Microsoft 365 tenant that contains a Windows 10 device. The device is onboarded to Microsoft Defender for Endpoint.
From Microsoft Defender Security Center, you perform a security investigation.
You need to run a PowerShell script on the device to collect forensic information.
Which action should you select on the device page?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/live-response?view=o365-worldwide
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft 365 compliance policies to meet the following requirements:
✑ Identify documents that are stored in Microsoft Teams and SharePoint Online that contain Personally Identifiable Information (PII).
✑ Report on shared documents that contain PII.
What should you create?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
HOTSPOT -
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.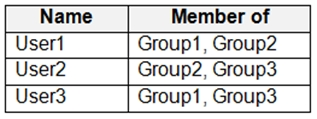
In Microsoft Endpoint Manager, you have the Policies for Office apps settings shown in the following table.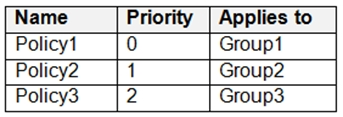
The policies use the settings shown in the following table.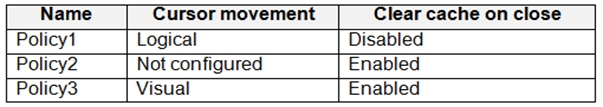
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: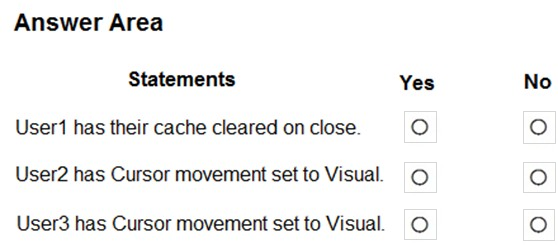
Answer:
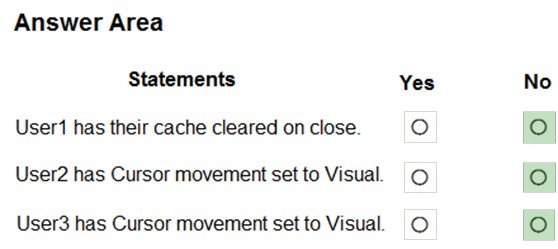
Reference:
https://docs.microsoft.com/en-us/deployoffice/overview-office-cloud-policy-service
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.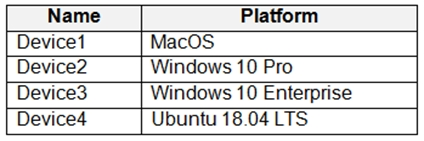
You plan to implement attack surface reduction (ASR) rules.
Which devices will support the ASR rules?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#requirements
You have a Microsoft 365 tenant.
You plan to enable BitLocker Disk Encryption (BitLocker) automatically for all Windows 10 devices that enroll in Microsoft Intune.
What should you use?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/encrypt-devices
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profiles?
Answer:
B
Intune device configuration profiles can be applied to Windows 10 devices and macOS devices
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. Windows 10
2. macOS
Other incorrect answer options you may see on the exam include the following:
1. Ubuntu Linux
2. iOS
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-configure
You have a Microsoft 365 tenant that contains 500 Windows 10 devices and a Microsoft Endpoint Manager device compliance policy.
You need to ensure that only devices marked as compliant can access Microsoft Office 365 apps.
Which policy type should you configure?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
You have a Microsoft 365 tenant that contains a Windows 10 device named Device1 and the Microsoft Endpoint Manager policies shown in the following table.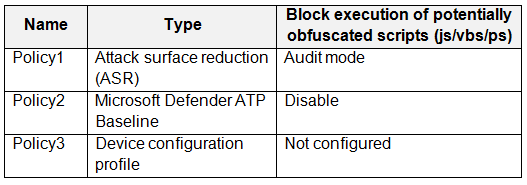
The policies are assigned to Device1.
Which policy settings will be applied to Device1?
Answer:
C
HOTSPOT -
You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices.
You plan to attack surface reduction (ASR) rules for the Windows 10 devices.
You configure the ASR rules in audit mode and collect audit data in a Log Analytics workspace.
You need to find the ASR rules that match the activities on the devices.
How should you complete the Kusto query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: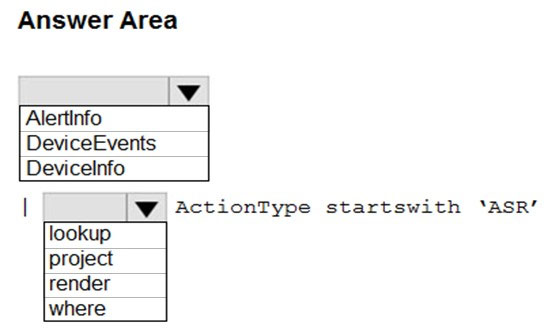
Answer:
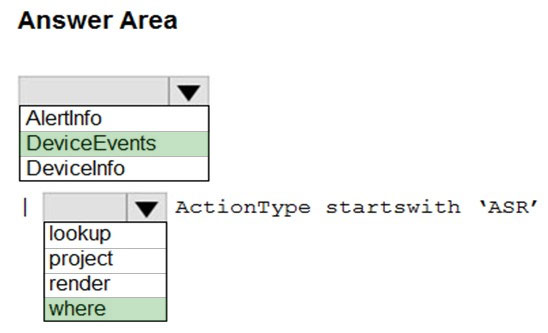
Reference:
https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/demystifying-attack-surface-reduction-rules-part-3/ba-p/1360968