Your on-premises network contains a database server and is accessible by using a VPN server.
You have a Microsoft 365 tenant.
You manage devices by using Microsoft Endpoint Manager.
You have an application named App1 that is deployed to every computer enrolled in Microsoft Intune. Each computer has a VPN profile assigned.
You need to ensure that App1 can access only the database server. App1 must be prevented from accessing other resources on the on-premises network.
What should you modify in the VPN profile?
Answer:
B
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
A network security group contains zero, or as many rules as desired, within Azure subscription limits.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
HOTSPOT -
You have the MDM Security Baseline profile shown in the MDM exhibit. (Click the MDM tab.)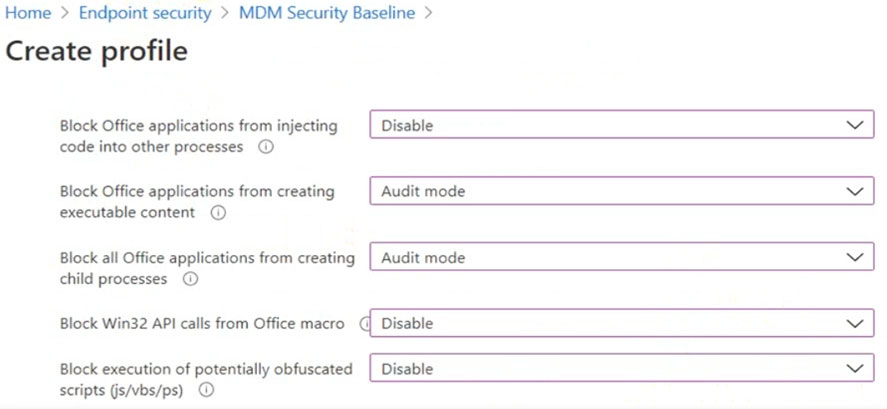
You have the ASR Endpoint Security profile shown in the ASR exhibit. (Click the ASR tab.)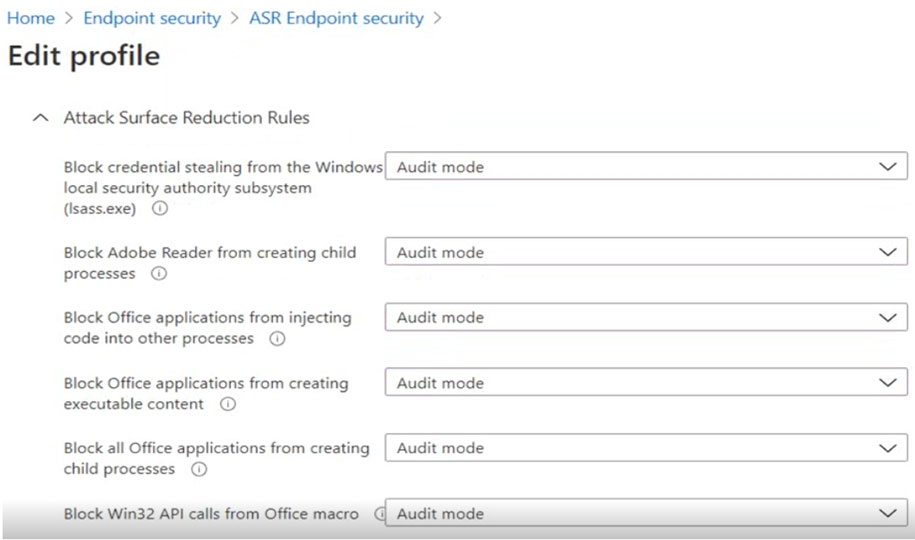
You plan to deploy both profiles to devices enrolled in Microsoft Intune.
You need to identify how the following settings will be configured on the devices:
✑ Block Office applications from creating executable content
✑ Block Win32 API calls from Office macro
Currently, the settings are disabled locally on each device.
What are the effective settings on the devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: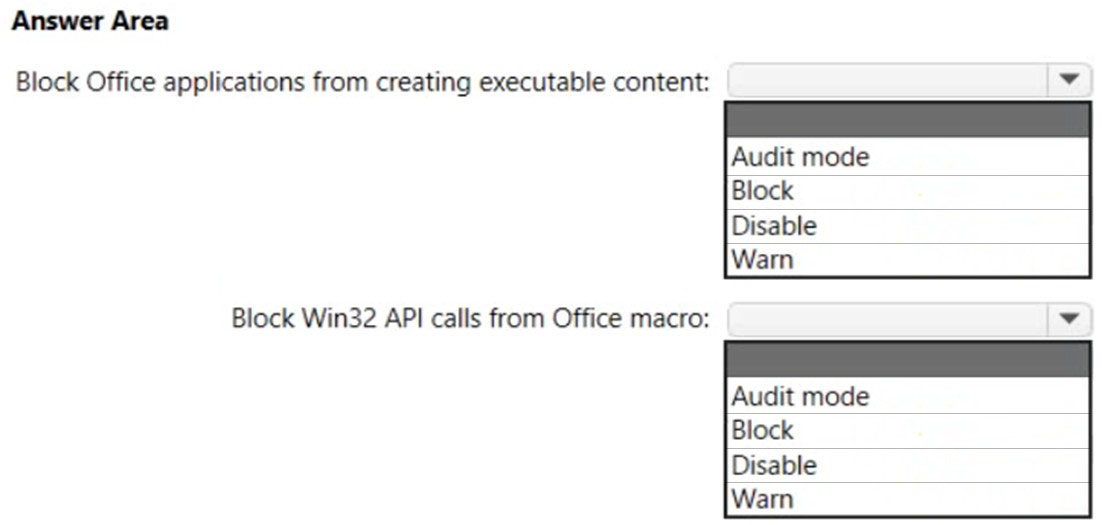
Answer:
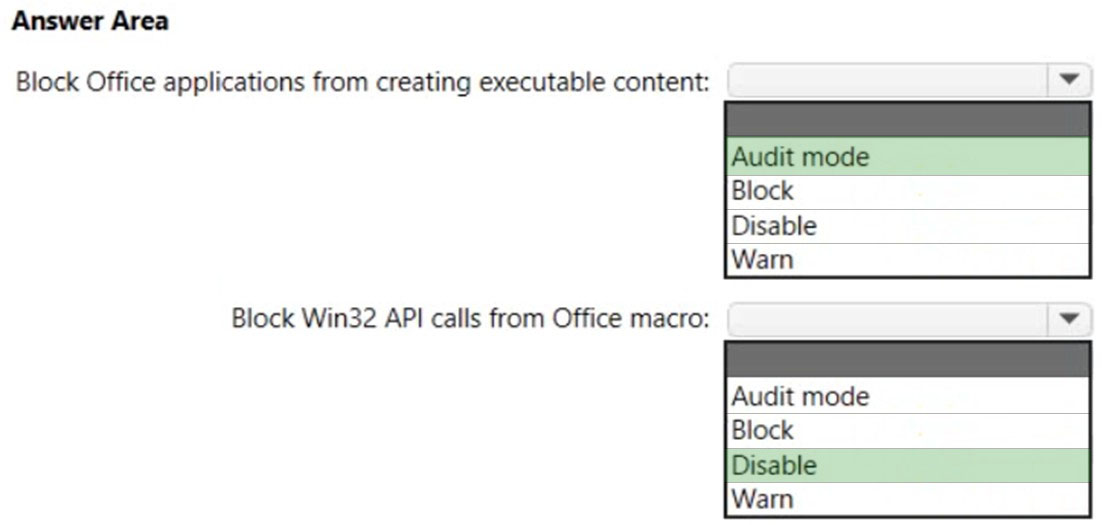
Box 1: Audit mode -
According to the ASR Endpoint Security profile and to the MDM Security Baseline profile
, Block Office applications from creating executable content is set to Audit mode.
Box 2: Disable -
Block Win32 API calls from Office macro: According to MDM Security Baseline profile it is set to disable. According to the ASR Endpoint Security profile it is set to
Audit mode.
The profiles are merged. The Baseline profile overrides the Endpoint Security profile.
Note:
When two or more policies have conflicting settings, the conflicting settings are not added to the combined policy, while settings that don't conflict are added to the superset policy that applies to a device.
Attack surface reduction rule merge behavior is as follows:
Endpoint security > Security baselines > Microsoft Defender for Endpoint Baseline > Attack Surface Reduction Rules.
MDM Security Baseline profile ASR Endpoint Security profile.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-security-asr-policy
HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.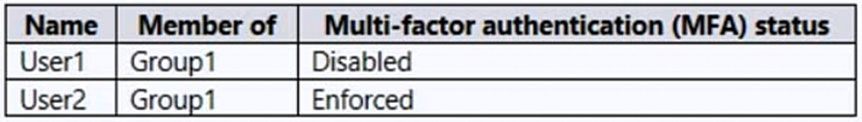
MFA has a trusted IP address range of 123.30.20.0/24.
You have the Azure AD named locations shown in the following table.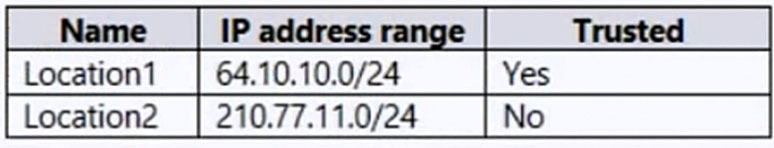
You create a Conditional Access policy that has the following settings:
✑ Name: CAPolicy1
✑ Assignments
- Users or workload identities
- Include: Group1
- Cloud apps or actions: App1
✑ Conditions
- Locations
- Include: All trusted locations
✑ Access controls
- Grant access
- Require multi-factor authentication
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: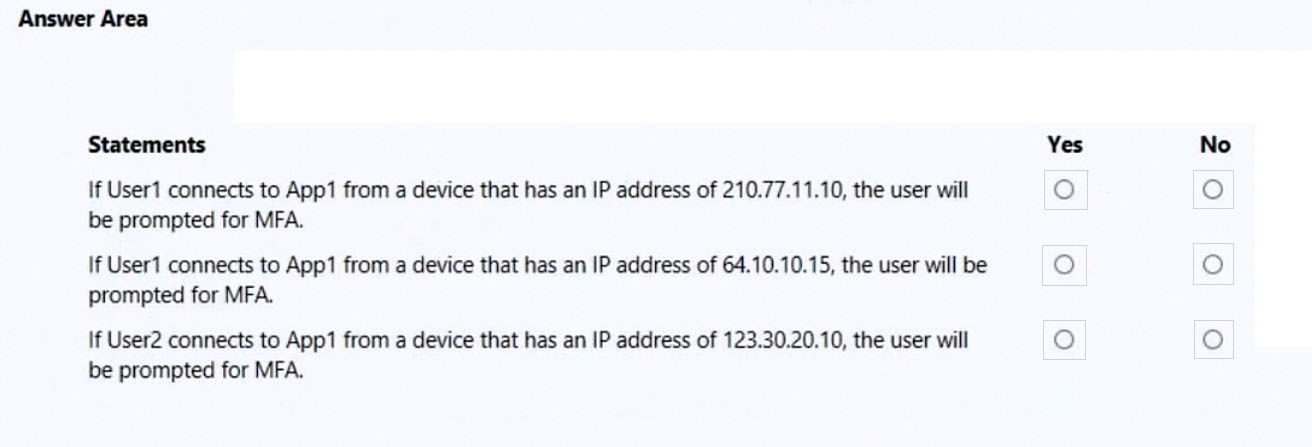
Answer:
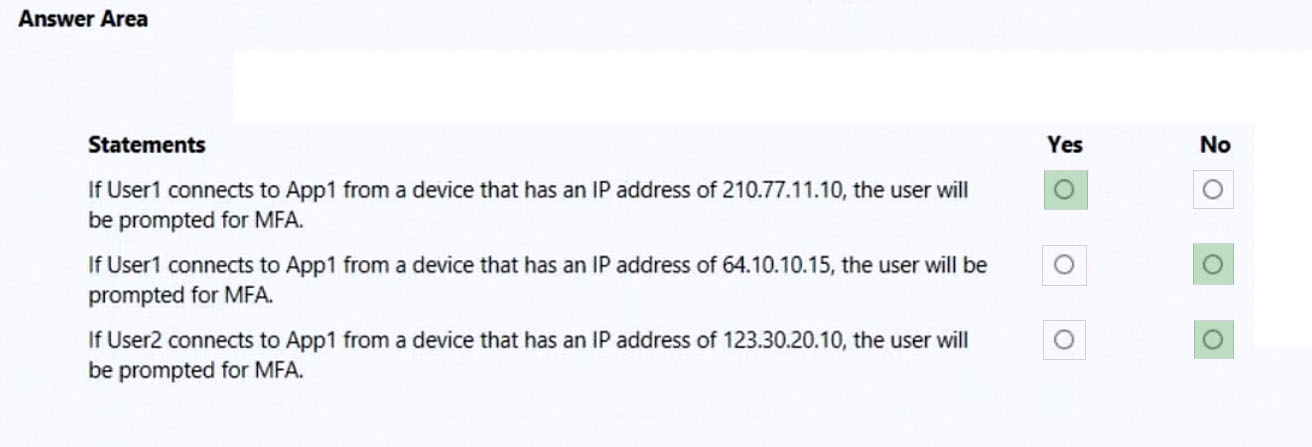
Box 1: Yes -
Location2 is not trusted.
Box 2: No -
Location1 is trusted.
Box 3:No -
MFA IP range is also trusted.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-all-users-mfa
DRAG DROP -
You have a Microsoft 365 subscription that contains two users named User1 and User2.
You need to ensure that the users can perform the following tasks:
User1 must be able to create groups and manage users.
✑ User2 must be able to reset passwords for nonadministrative users.
The solution must use the principle of least privilege.
Which role should you assign to each user? To answer, drag the appropriate roles to the correct users. Each role may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: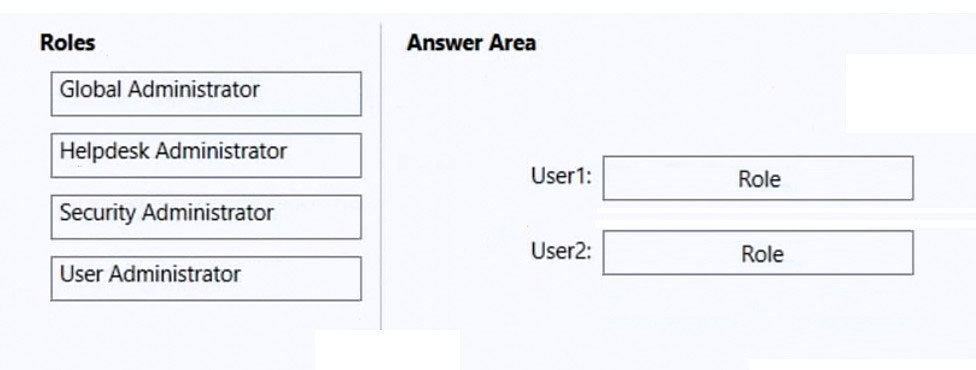
Answer:
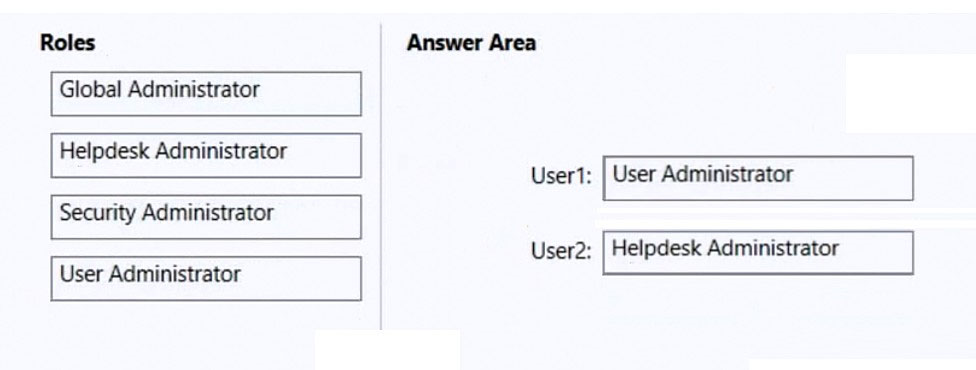
Box 1: User Administrator -
User admin -
Assign the user admin role to users who you want to access and manage user password resets and manage users and groups. They can also open and manage support requests to Microsoft support.
Box 2: Helpdesk Administrator -
Assign the Helpdesk admin role to users who want to reset passwords, force users to sign out for any security issues. They can also open and manage support requests to Microsoft support. The Helpdesk admin can only help non-admin users and users assigned these roles: Directory reader, Guest inviter, Helpdesk admin, Message center reader, and Reports reader.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/admin/add-users/admin-roles-page
HOTSPOT -
You have the device configuration profile shown in the following exhibit.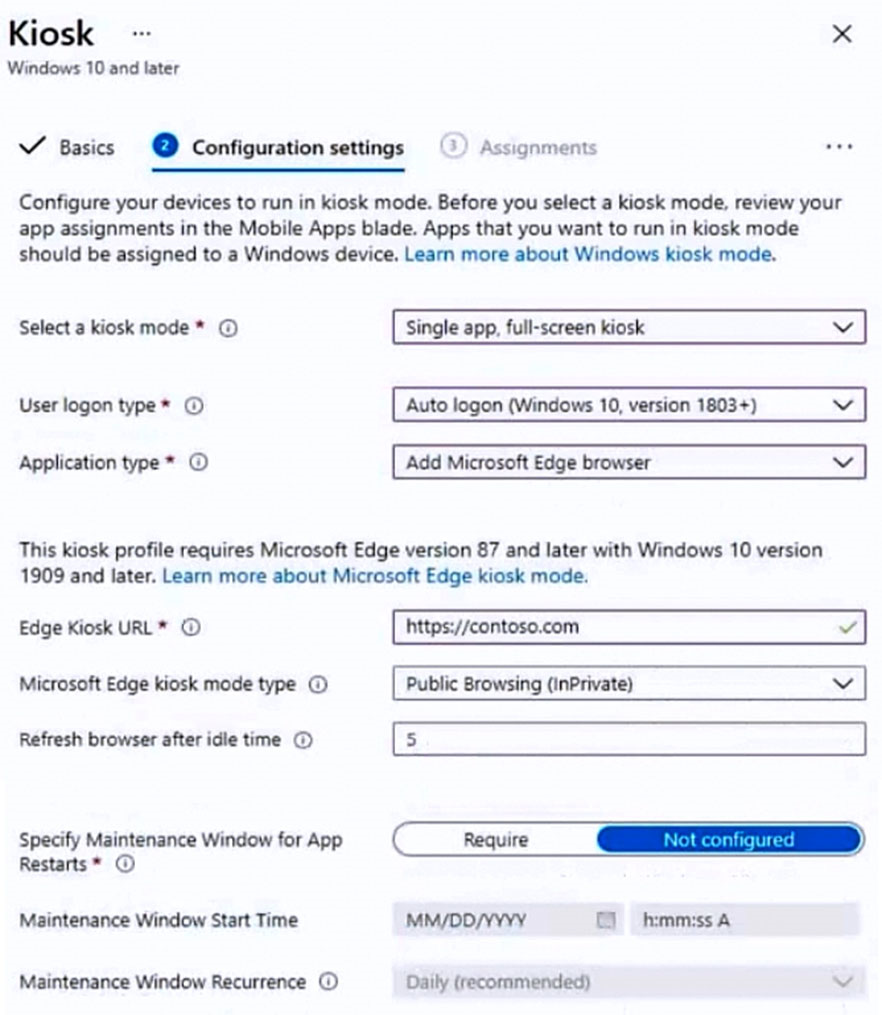
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: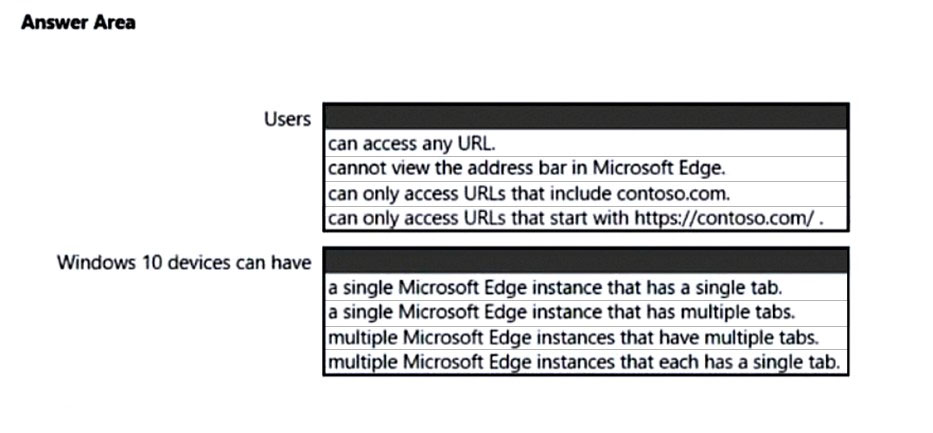
Answer:
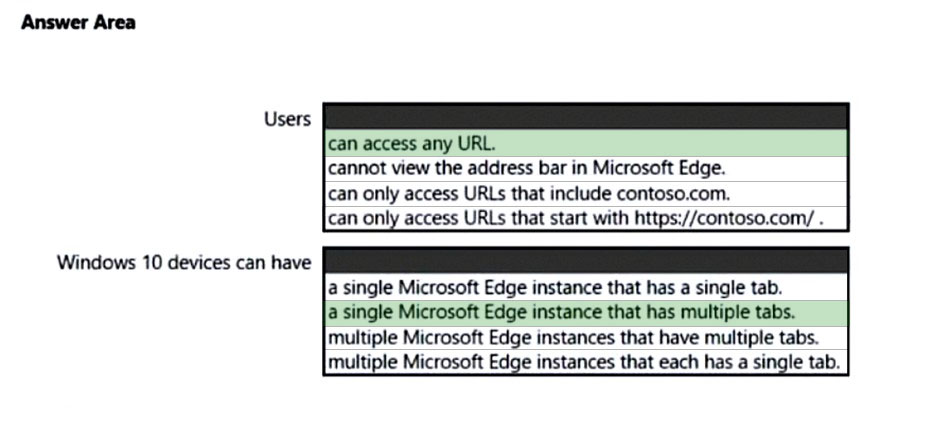
Box 1: can access any URL.
Public Browsing (InPrivate): Runs a limited multi-tab version of Microsoft Edge. Users can browse publicly, or end their browsing session.
Box 2: a single Microsoft Edge instance that has multiple tabs
Single app, full-screen kiosk runs only one app on the device, such as a web browser or Store app.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/kiosk-settings-windows
You have a Microsoft 365 subscription.
You plan to use Conditional Access policies.
You need to identify which scenarios the policies will support.
Which two scenarios should you identify? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
AD
A: Conditional Access allows administrators to control what Office 365 apps users can gain access to based on if they pass/fail certain conditions. These conditions are enforced by building a policy (or multiple policies) to control how users access your Office 365 resources.
Cloud Apps- What apps do you want to control? Conditional Access does not need to apply to all of Office 365, you can be more granular and just control access to specific apps ג€" E.g. Exchange Online.
Access can be allowed to Office 365 with the following conditions:
* Require multi-factor authentication ג€" User is allowed in but will need to complete additional security to log in.
* Etc.
D: The easiest way to block legacy authentication across your entire organization is by configuring a Conditional Access policy that applies specifically to legacy authentication clients and blocks access.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authenticationhttps://docs.microsoft.com/en-us/azure/active- directory/conditional-access/block-legacy-authentication
HOTSPOT -
You have devices enrolled in Microsoft Intune as shown in the following table.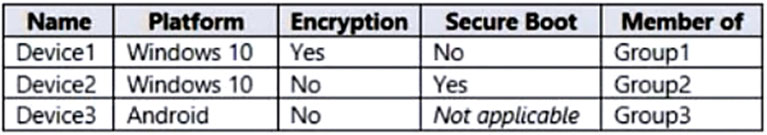
Intune includes the device compliance policies shown in the following table.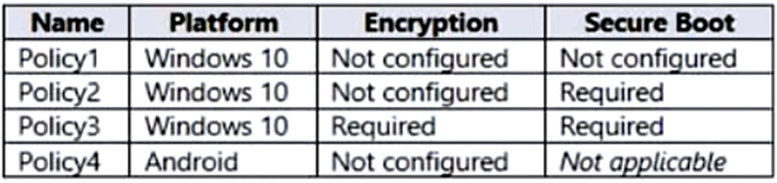
The device compliance policies have the assignments shown in the following table.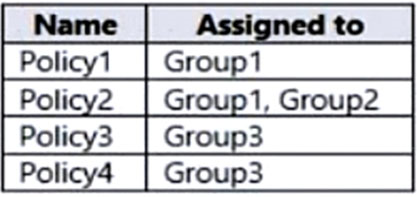
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
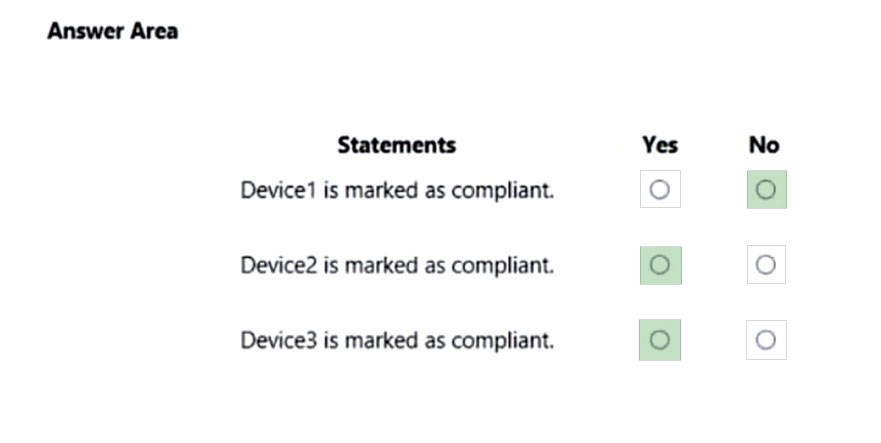
Box 1: No -
Device1 is in Group1. Policy1 is assigned to Group1. Policy2 is also assigned to Group1. Device1 is compliant to Policy1, but not compliant to Policy2 (fails on
Secure Boot).
By default, each device compliance policy includes the action to mark a device as noncompliant if it fails to meet a policy rule.
Box 2: Yes -
Device2 is in Group2. Policy2 is assigned to Group2. Device2 is compliant to Policy2 (Secure boot met).
Box 3: Yes -
Device3 is in Group 3. Policy3 and Policy4 are assigned to Group3. Policy3 is for Windows 10 so it is disregarded. Device3 is compliant to Policy4.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started
You have an Azure Active Directory (Azure AD) tenant that contains the named locations shown in the following table.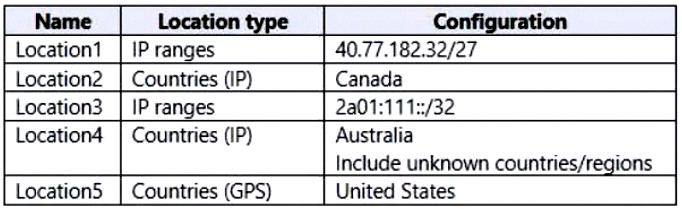
You need to create a Conditional Access policy that will have a condition to include only trusted locations.
Which two named locations can be marked as trusted? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
AC
Trusted locations -
Administrators can name locations defined by IP address ranges to be trusted named locations
A: An IPv4 named location can be marked as trusted.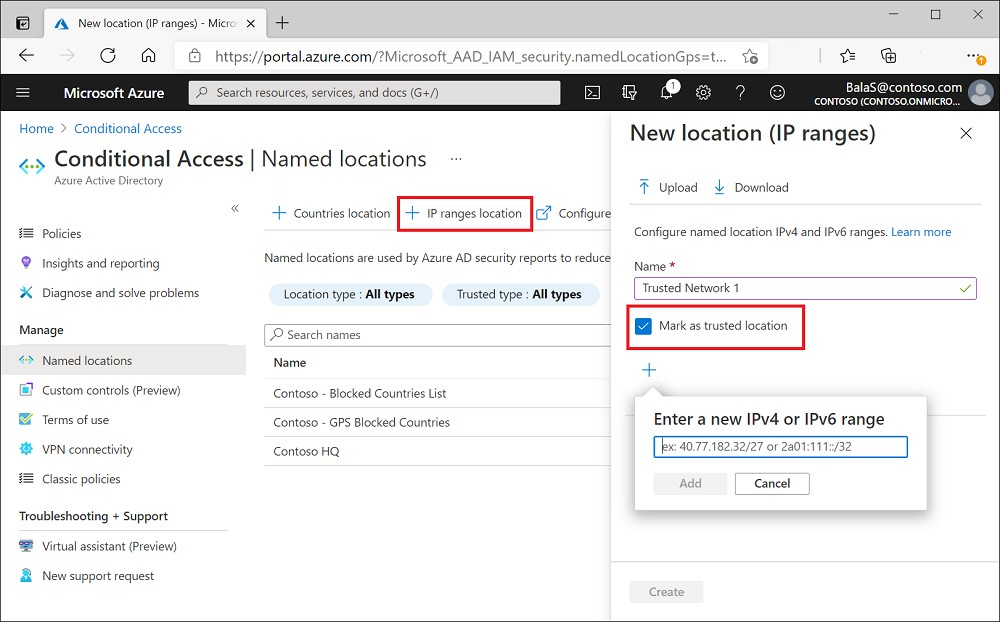
C: An IPv6 named location can be marked as trusted.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
You have a Microsoft 365 subscription,
You need provide a user the ability to disable Security defaults and create Conditional Access policies. The solution must use the principle of least privilege.
Which role should you assign to the user?
Answer:
B
To enable or disable security defaults in your directory, sign in to theג€‰Azure portalג€‰as a security administrator, Conditional Access administrator, or global administrator.
Note: Conditional Access Administrator
Users with this role have the ability to manage Azure Active Directory Conditional Access settings.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to create a Conditional Access policy to block users that have a high sign-in risk level.
You need to identify the required license, and what to use to identify the sign-in risk level. The solution must minimize costs.
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
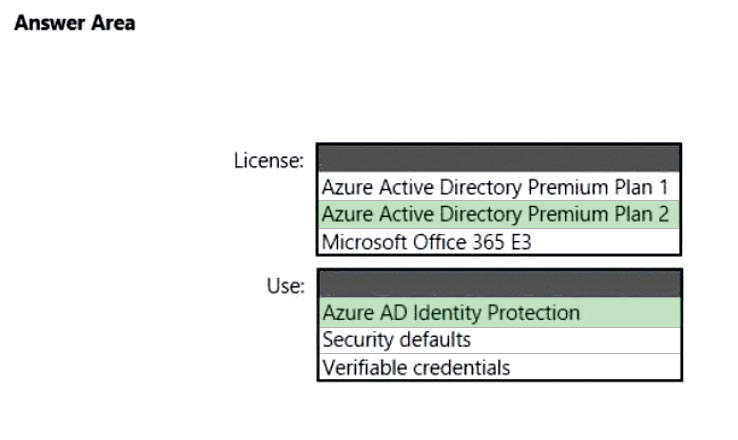
Box 1: Azure AD Premium Plan 2 -
You will need an Azure AD Premium P1 license to get access to the Microsoft Office 365 conditional access policy feature.
However, need Azure AD Premium Plan 2 to sign-in risk.
Box 2: Azure AD Identity Protection
A sign-in risk represents the probability that a given authentication request isn't authorized by the identity owner. Organizations with Azure AD Premium P2 licenses can create Conditional Access policies incorporating Azure AD Identity Protection sign-in risk detections.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-risk https://blog.mydock365.com/what-is-conditional-access-in-microsoft-365