You have a Microsoft 365 tenant that contains the objects shown in the following table.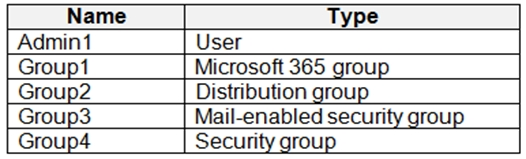
You are creating a compliance policy named Compliance1.
Which objects can you specify in Compliance1 as additional recipients of noncompliance notifications?
Answer:
D
Need email address to specify additional recipients of noncompliance notification.
Security groups have no email address.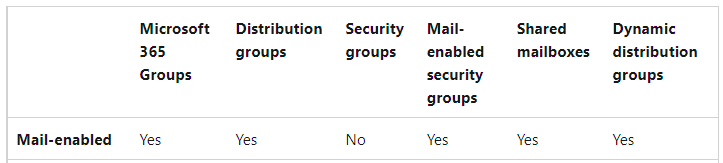
Reference:
https://docs.microsoft.com/en-us/microsoft-365/admin/create-groups/compare-groups?view=o365-worldwide
HOTSPOT -
You have a workgroup computer named Computer1 that runs Windows 10 and has the users shown in the following table.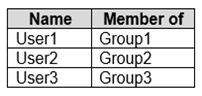
Group1 is a member of Group3.
You are creating a file named Kiosk.xml that specifies a lockdown profile for a multi-app kiosk.
Kiosk.xml contains the following section.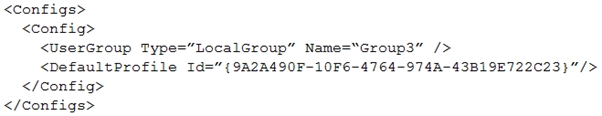
You apply Kiosk.xml to Computer1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: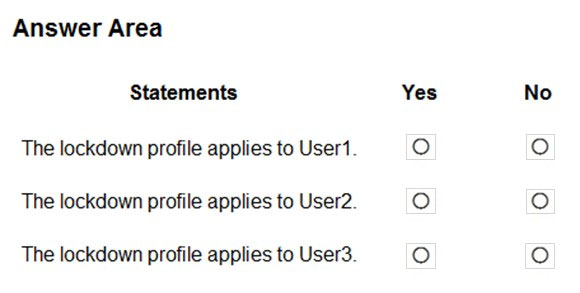
Answer:
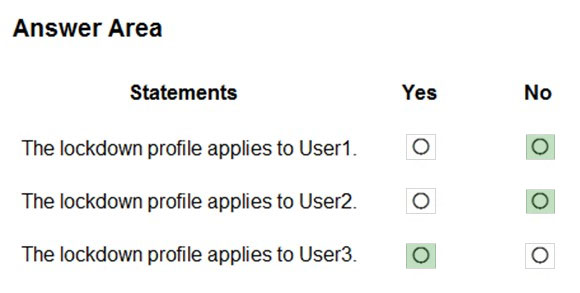
Box 1: No -
The lockdown profile only applies to the specified group, not to the nested group.
Box 2: No -
Box 3: Yes -
Reference:
https://docs.microsoft.com/en-us/windows/configuration/lock-down-windows-10-to-specific-apps#config-for-group-accounts
HOTSPOT -
Your network contains an Active Directory domain named contoso.com that syncs to Azure Active Directory (Azure AD). The domain contains the users shown in the following table.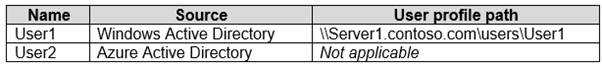
Enterprise State Roaming is enabled for User2.
You have the computers shown in the following table.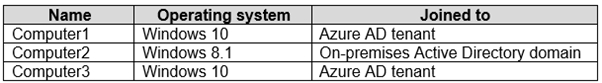
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: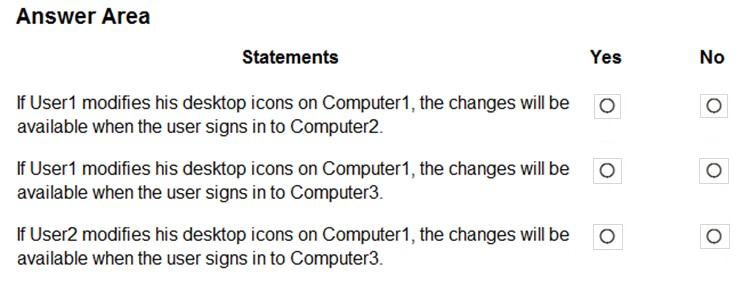
Answer:
The requirements of Enterprise State Roaming are:
✑ Windows 10, with the latest updates, and a minimum Version 1511 (OS Build 10586 or later) is installed on the device.
✑ The device is Azure AD joined or hybrid Azure AD joined.
✑ Ensure that Enterprise State Roaming is enabled for the tenant in Azure AD.
✑ The user is assigned an Azure Active Directory Premium license.
✑ The device must be restarted and the user must sign in again to access Enterprise State Roaming features.
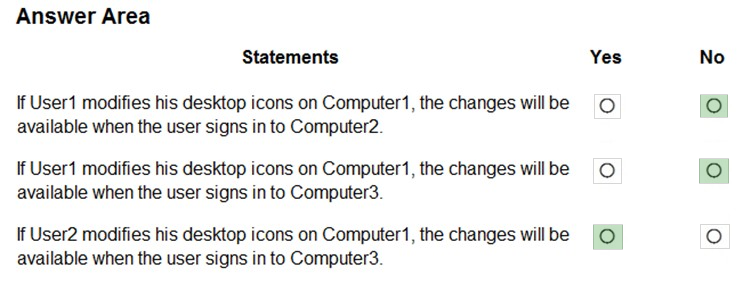
Box 1: No -
Computer2 runs Windows 8.1.
Enterprise State Roaming requires Windows 10, with the latest updates, and a minimum Version 1511 (OS Build 10586).
Also, Enterprise State Roaming is enabled for User2, not for User1.
Box 2: No -
The device must be Azure AD joined or hybrid Azure AD joined.
Your network contains an Active Directory domain named contoso.com that syncs to Azure Active Directory (Azure AD), in other words, a hybrid Azure AD.
Also, Enterprise State Roaming is enabled for User2, not for User1.
Box 3: Yes -
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/devices/enterprise-state-roaming-troubleshooting
HOTSPOT -
Your company has computers that run Windows 8.1, Windows 10, or macOS.
The company uses Microsoft Intune to manage the computers.
You need to create a device configuration profile to configure Windows Hello for Business on the computers that support it.
Which platform type and profile type should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: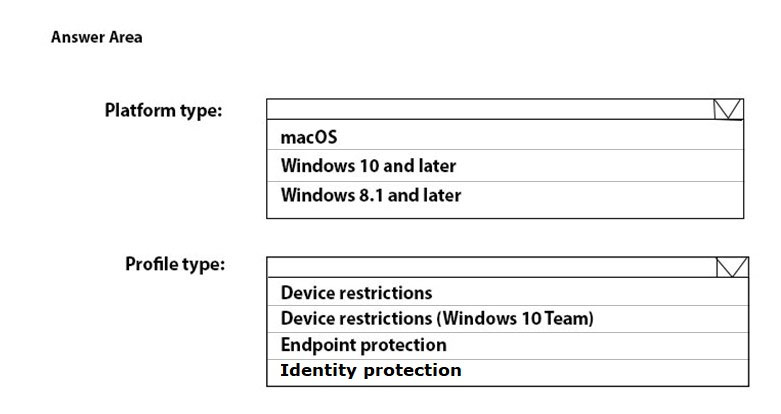
Answer:
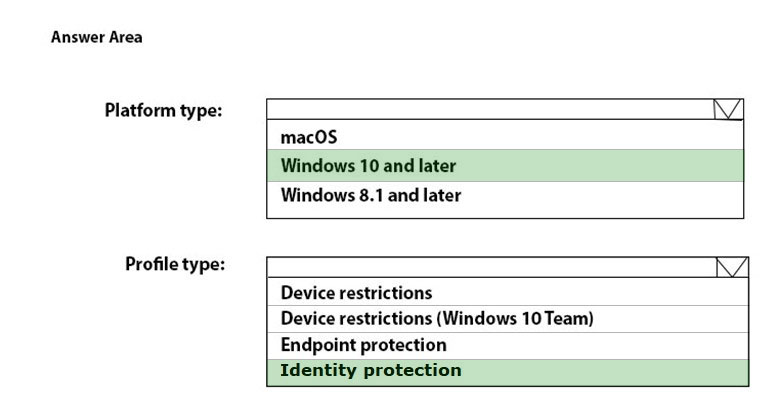
Box 1: Windows 10 and later -
Windows Hello for Business is a method for signing in to Windows devices by replacing passwords, smart cards, and virtual smart cards. Intune includes built-in settings so Administrators can configure and use Windows Hello for Business. For example, you can use these settings to:
✑ Enable Windows Hello for Business for devices and users
✑ Set device PIN requirements, including a minimum or maximum PIN length
✑ Allow gestures, such as a fingerprint, that users can (or can't use) to sign in to devices
Box 2: Identity protection -
Create the device profile -
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Select Devices > Configuration profiles > Create profile.
3. Enter the following properties:
4. Platform: Select Windows 10 and later.
5. Profile: Select Templates > Identity protection.
6. Etc
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/identity-protection-configure
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create an Azure Active Directory group that contains only the Windows 10 Enterprise devices. You assign Profile1 to the new group.
Does this meet the goal?
Answer:
B
Instead: You configure an applicability rule for Profile1. You assign Profile1 to Group1.
Note: Applicability rules allow administrators to target devices in a group that meet specific criteria. For example, you create a device restrictions profile that applies to the All Windows 10/11 devices group. And, you only want the profile assigned to devices running Windows Enterprise.
To do this task, create an applicability rule.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-create
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You create a scope tag, and then you add the scope tag to the Windows 10 Enterprise devices. You edit the settings of Profile1.
Does this meet the goal?
Answer:
B
Instead: You configure an applicability rule for Profile1. You assign Profile1 to Group1.
Note: Applicability rules allow administrators to target devices in a group that meet specific criteria. For example, you create a device restrictions profile that applies to the All Windows 10/11 devices group. And, you only want the profile assigned to devices running Windows Enterprise.
To do this task, create an applicability rule.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-create
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Directory group named Group1 that contains Windows 10 Enterprise devices and Windows 10 Pro devices.
From Microsoft Intune, you create a device configuration profile named Profile1.
You need to ensure that Profile1 applies to only the Windows 10 Enterprise devices in Group1.
Solution: You configure an applicability rule for Profile1. You assign Profile1 to Group1.
Does this meet the goal?
Answer:
A
Applicability rules allow administrators to target devices in a group that meet specific criteria. For example, you create a device restrictions profile that applies to the All Windows 10/11 devices group. And, you only want the profile assigned to devices running Windows Enterprise.
To do this task, create an applicability rule.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-create
HOTSPOT -
You have two Windows 10 devices enrolled in Microsoft Intune as shown in the following table.
The Compliance policy settings are configured as shown in the following exhibit.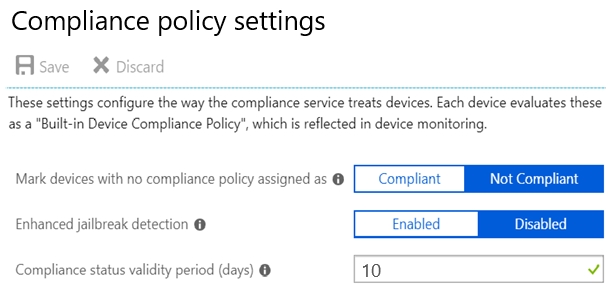
On August 1, you create a compliance policy as shown in the following exhibit.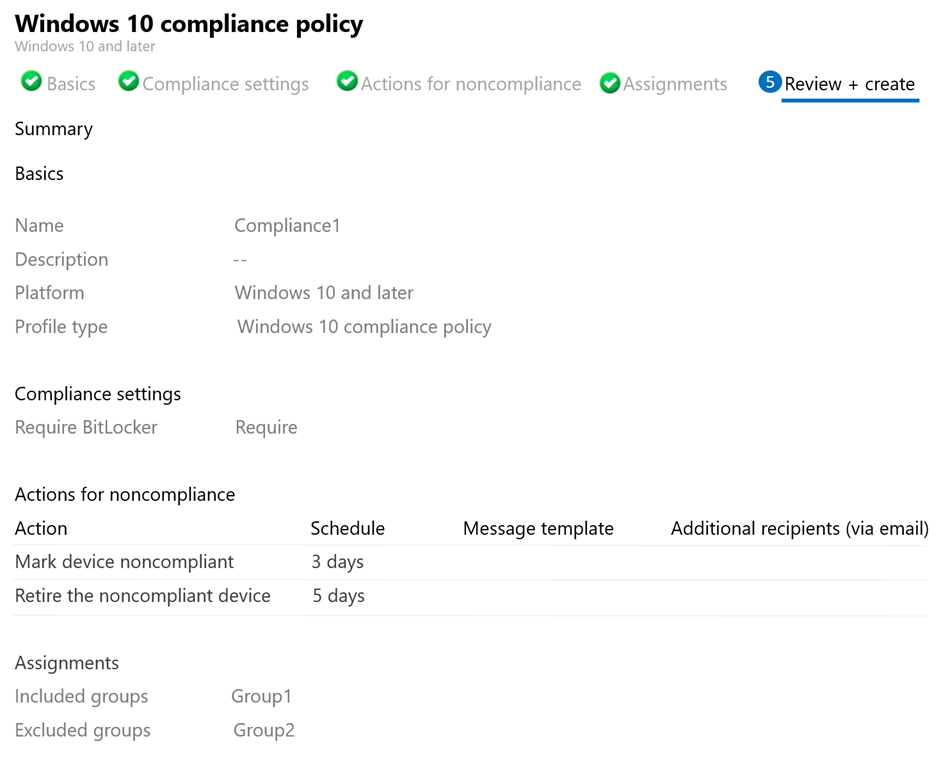
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Box 1: No -
Device1 belongs to Group2. Group2 has not been assigned a compliance policy. Devices with no compliance policy assigned as Not Compliant. Device1 gets a 3 day grace period, but at August 4 is it marked as Non-compliant.
Box 2: Yes -
Device1 belongs to Group2. Group2 has not been assigned a compliance policy. Devices with no compliance policy assigned as Not Compliant. Device1 gets a 3 day grace period, so at August 2 it is compliant.
Box 3: No -
Device2 has BitLocker Disabled. The Windows 10 compliance policy applies to Group1 which includes Device1. At August 4 Device is marked noncompliant. 5 days later, at August 9th it is retired.
Note:
* Retire the noncompliant device: This action removes all company data off the device and removes the device from Intune management.
* By default, each compliance policy includes the action for noncompliance of Mark device noncompliant with a schedule of zero days (0). The result of this default is when Intune detects a device isn't compliant, Intune immediately marks the device as noncompliant.
By configuring Actions for noncompliance you gain flexibility to decide what to do about noncompliant devices, and when to do it. For example, you might choose to not block the device immediately, and give the user a grace period to become compliant.
Compliance status validity period (days):
Specify a period in which devices must successfully report on all their received compliance policies. If a device fails to report its compliance status for a policy before the validity period expires, the device is treated as noncompliant.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/device-compliance-get-started https://docs.microsoft.com/en-us/mem/intune/protect/actions-for-noncompliance
HOTSPOT -
Your network contains an Active Directory forest named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You use Microsoft Endpoint Configuration Manager for device management.
You have the Windows 10 devices shown in the following table.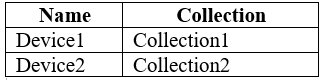
You configure Endpoint Configuration Manager co-management as follows:
✑ Automatic enrollment in Intune: Pilot
✑ Pilot collection for all workloads: Collection2
You configure co-management workloads as shown in the following exhibit.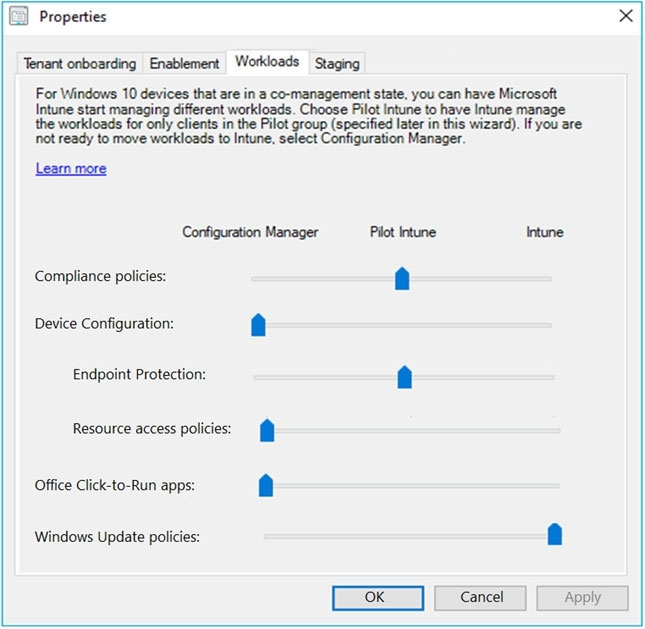
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: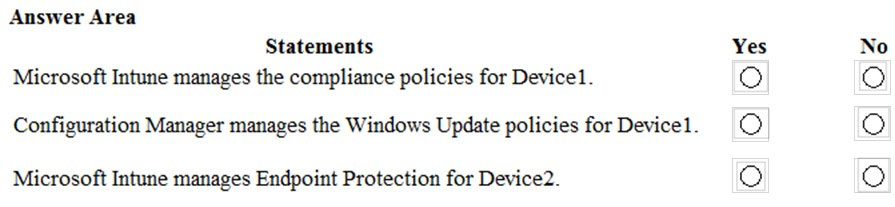
Answer:
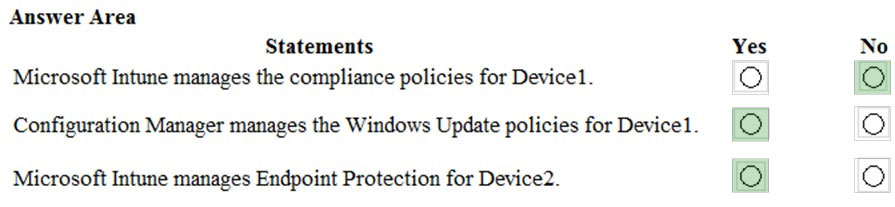
Box 1: No -
The Pilot Group does not include Device1.
Box 2: Yes -
Box 3: Yes -
The Pilot Group includes Device3.
Reference:
https://docs.microsoft.com/en-us/mem/configmgr/comanage/how-to-enable
HOTSPOT -
You have a Microsoft 365 E5 tenant that connects to Microsoft Defender for Endpoint.
You have devices enrolled in Microsoft Intune as shown in the following table.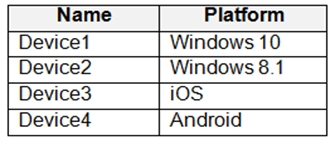
You plan to use risk levels in Microsoft Defender for Endpoint to identify whether a device is compliant. Noncompliant devices must be blocked from accessing corporate resources.
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint, and which Endpoint security policies must be configured.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: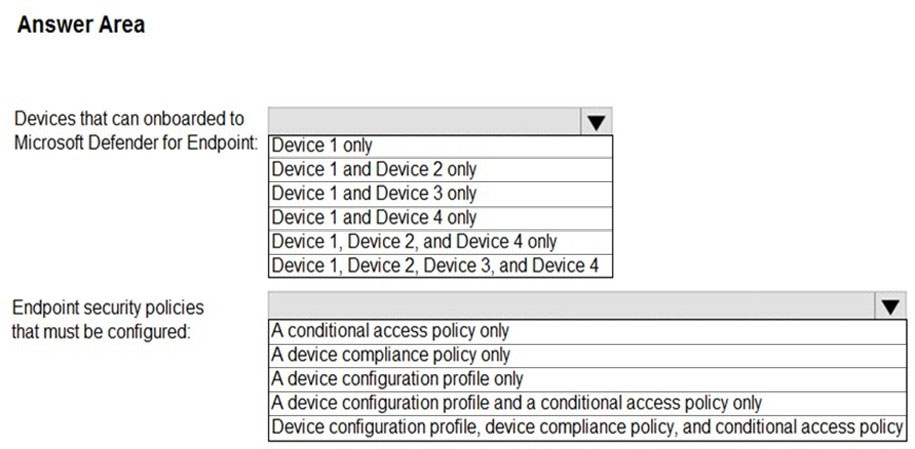
Answer:
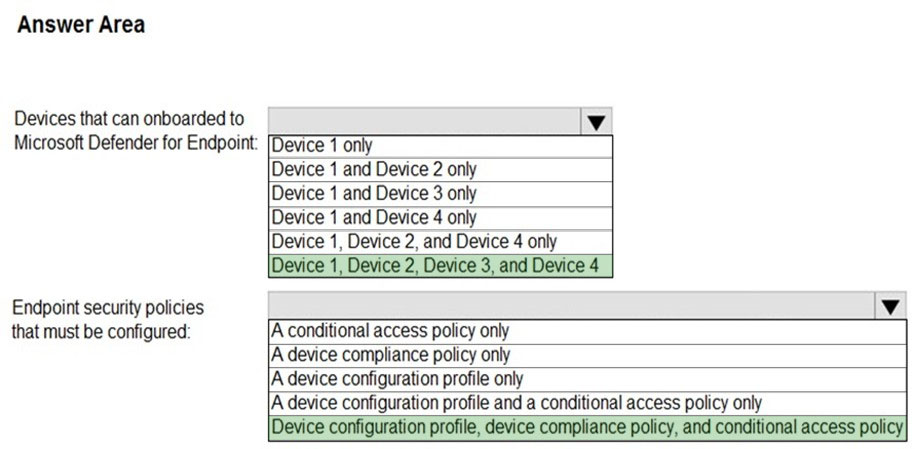
Box 1: Device 1, Device2, Device 3, and Device 4
Supported Windows versions include Windows 8.1 and Windows 10
Other supported operating systems
Android -
iOS
Linux -
macOS
Box 2: Device configuration profile, device compliance policy, and conditional access policy
We need all three policies.
Establish a service-to-service connection between Intune and Microsoft Defender for Endpoint. This connection lets Microsoft Defender for Endpoint collect data about machine risk from supported devices you manage with Intune.
Use a device configuration profile to onboard devices with Microsoft Defender for Endpoint. You onboard devices to configure them to communicate with Microsoft
Defender for Endpoint and to provide data that helps assess their risk level.
Use a device compliance policy to set the level of risk you want to allow. Risk levels are reported by Microsoft Defender for Endpoint. Devices that exceed the allowed risk level are identified as noncompliant.
Use a conditional access policy to block users from accessing corporate resources from devices that are noncompliant.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/minimum-requirements https://docs.microsoft.com/en-us/mem/intune/protect/advanced-threat-protection#onboard-devices-by-using-a-configuration-profile