HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area: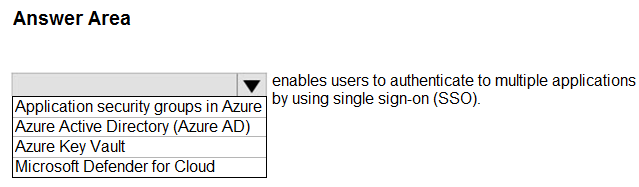
Answer:
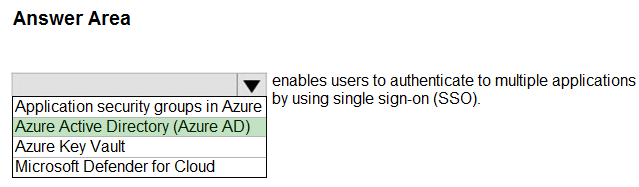
Box: Azure Active Directory (Azure AD)
You can enable single sign-on for an enterprise application through Azure Active Directory (Azure AD.
Incorrect:
Application security groups enable you to configure network security as a natural extension of an application's structure, allowing you to group virtual machines and define network security policies based on those groups.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/add-application-portal-setup-sso
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Box 1: No -
Azure creates the default rules in each network security group that you create. These rules allow some traffic.
Box 2: Yes -
A network security group contains zero, or as many rules as desired. These rules can refer to application security groups.
Box 3: Yes -
Azure creates the Inbound and OutBound default rules in each network security group that you create.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
DRAG DROP -
Match the term to the appropriate description.
To answer, drag the appropriate term from the column on the left to its description on the right. Each term may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: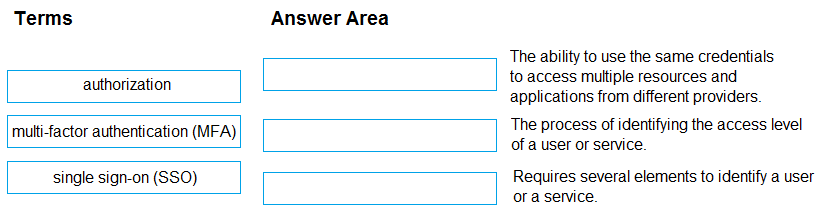
Answer:
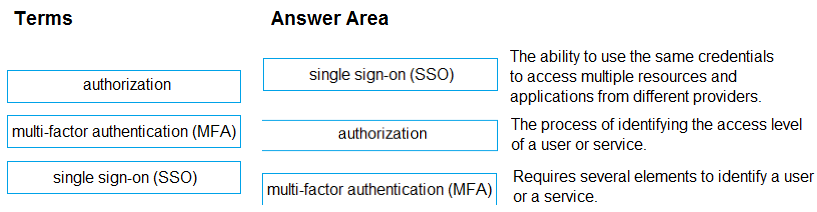
Your company plans to automate the deployment of servers to Azure.
Your manager is concerned that you may expose administrative credentials during the deployment.
You need to recommend an Azure solution that encrypts the administrative credentials during the deployment.
What should you include in the recommendation?
Answer:
A
Azure Key Vault protects cryptographic keys, certificates (and the private keys associated with the certificates), and secrets (such as connection strings and passwords) in the cloud.
Reference:
https://docs.microsoft.com/en-us/azure/key-vault/general/security-features
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area: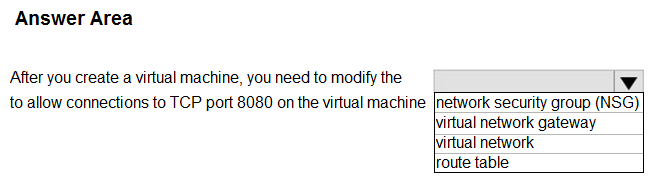
Answer:
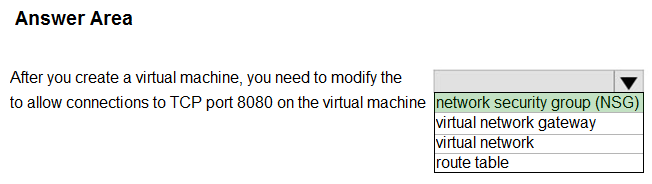
Box: network Security group (NSG)
You can use an Azure network security group to filter network traffic to and from Azure resources in an Azure virtual network. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources. For each rule, you can specify source and destination, port, and protocol.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area: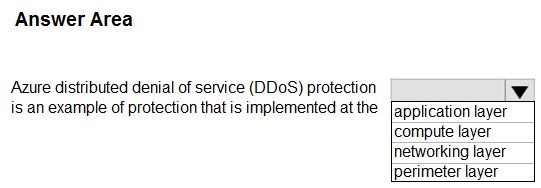
Answer:
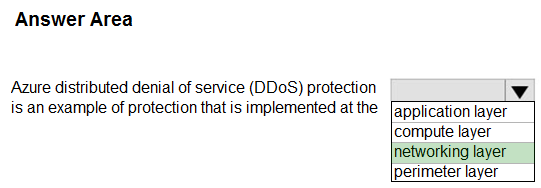
Box: networking layer -
DDoS Protection defends against a comprehensive set of network layer (layer 3/4) attacks.
Reference:
https://azure.microsoft.com/en-us/services/ddos-protection
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Answer:
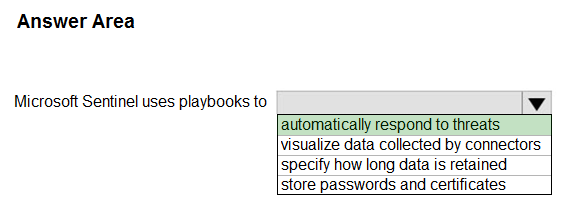
Box: automatically respond to threats
Playbooks are collections of procedures that can be run from Microsoft Sentinel in response to an alert or incident. A playbook can help automate and orchestrate your response, and can be set to run automatically when specific alerts or incidents are generated, by being attached to an analytics rule or an automation rule, respectively.
Note: Automation rules help you triage incidents in Microsoft Sentinel. You can use them to automatically assign incidents to the right personnel, close noisy incidents or known false positives, change their severity, and add tags. They are also the mechanism by which you can run playbooks in response to incidents.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook
You need to configure an Azure solution that meets the following requirements:
✑ Secures websites from attacks
✑ Generates reports that contain details of attempted attacks
What should you include in the solution?
Answer:
D
DDoS is a type of attack that tries to exhaust application resources. The goal is to affect the application's availability and its ability to handle legitimate requests.
DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet.
Azure has two DDoS service offerings that provide protection from network attacks: DDoS Protection Basic and DDoS Protection Standard.
DDoS Basic protection is integrated into the Azure platform by default and at no extra cost.
You have the option of paying for DDoS Standard. It has several advantages over the basic service, including logging, alerting, and telemetry. DDoS Standard can generate reports that contain details of attempted attacks as required in this question.
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/ddos-best-practices
HOTSPOT -
You plan to implement several security services for an Azure environment. You need to identify which Azure services must be used to meet the following security requirements:
✑ Monitor threats by using sensors
✑ Enforce Azure Multi-Factor Authentication (MFA) based on a condition
Which Azure service should you identify for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
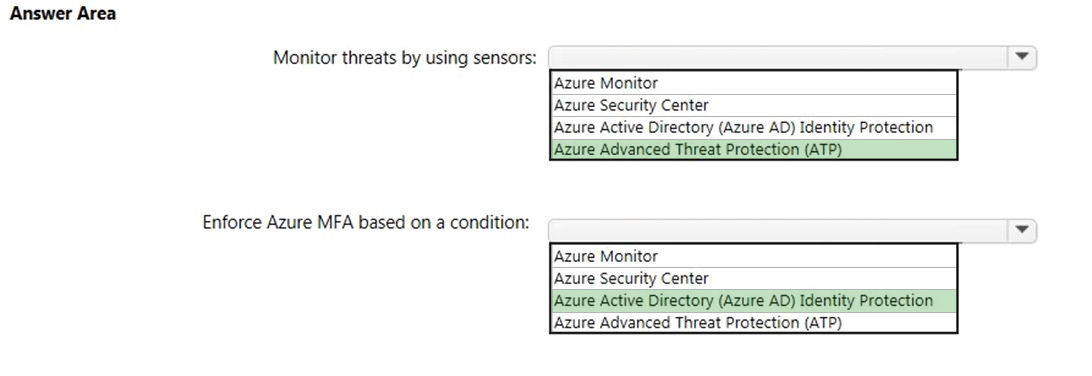
Box 1:
To monitor threats by using sensors, you would use Azure Advanced Threat Protection (ATP).
Azure Advanced Threat Protection (ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Sensors are software packages you install on your servers to upload information to Azure ATP.
Box 2:
To enforce MFA based on a condition, you would use Azure Active Directory Identity Protection.
Azure AD Identity Protection helps you manage the roll-out of Azure Multi-Factor Authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you are signing in to.
References:
https://docs.microsoft.com/en-us/azure-advanced-threat-protection/what-is-atp https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-configure-mfa-policy
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
What are two possible solutions? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
B
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network.
You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 80 (HTTP).
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview