Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Controlled folder access.
Does this meet the goal?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-controlled-folders?view=o365-worldwide
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection
Does this meet the goal?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-controlled-folders?view=o365-worldwide
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From App & browser control, you configure the Exploit protection settings.
Does this meet the goal?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-controlled-folders?view=o365-worldwide
DRAG DROP -
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant.
The AD DS domain contains a domain controller named DC1. DC1 does NOT have internet access.
You need to configure password security for on-premises users. The solution must meet the following requirements:
✑ Prevent the users from using known weak passwords.
✑ Prevent the users from using the company name in passwords.
What should you do? To answer, drag the appropriate configurations to the correct targets. Each configuration may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: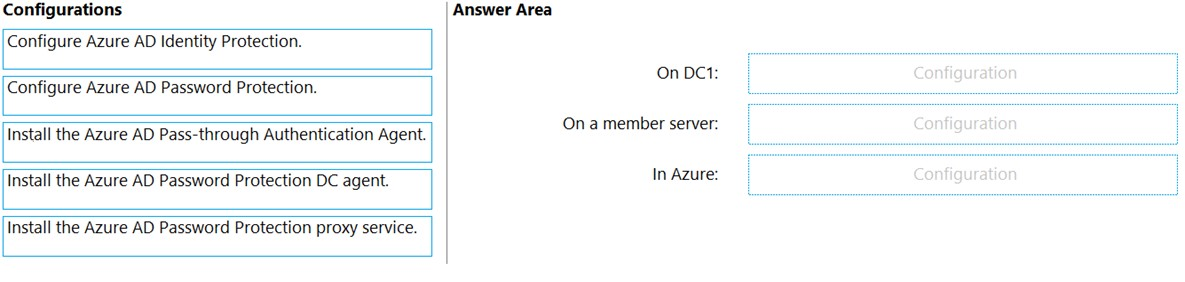
Answer:
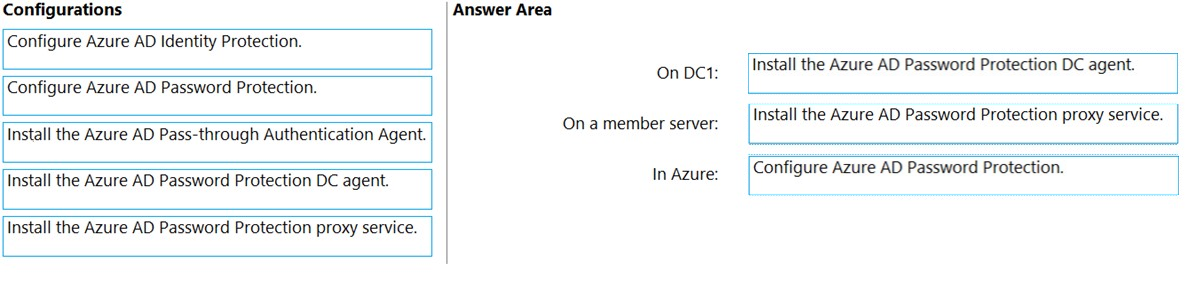
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-ban-bad-on-premises-deploy
You have a three-node failover cluster.
You need to run pre-scripts and post-scripts when Cluster-Aware Updating (CAU) runs. The solution must minimize administrative effort.
What should you use?
Answer:
B
Cluster-Aware Updating advanced options and updating run profiles.
You can set the PreUpdateScript or PostUpdateScript the option.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating-options
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)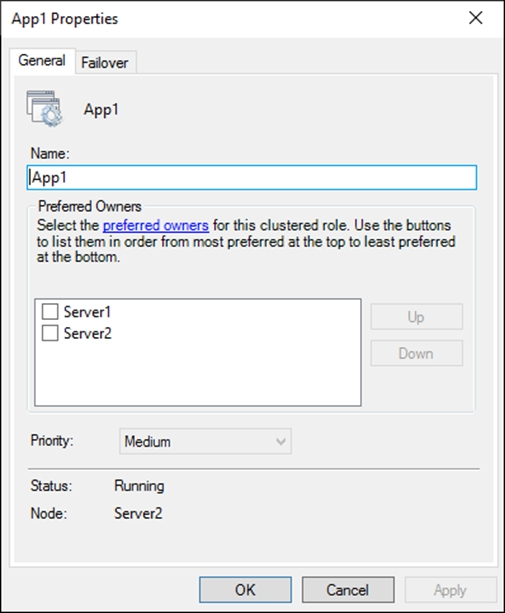
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)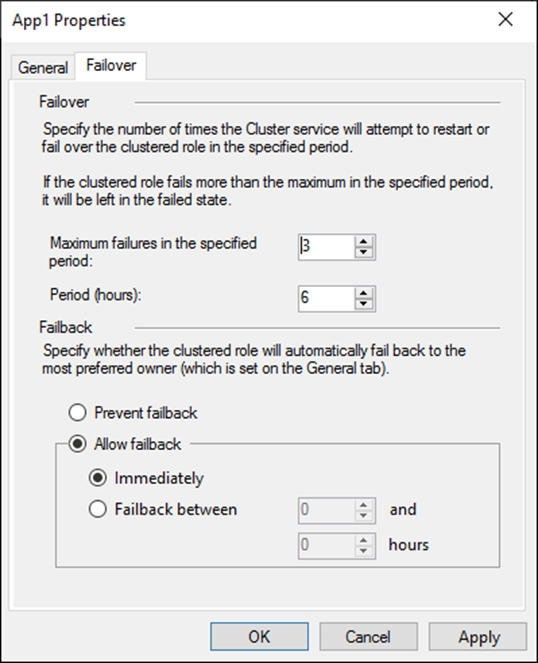
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: You pause the Server1 node in Cluster1 and then start Server1.
Does this meet the goal?
Answer:
B
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource's cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting "prevent failback." When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)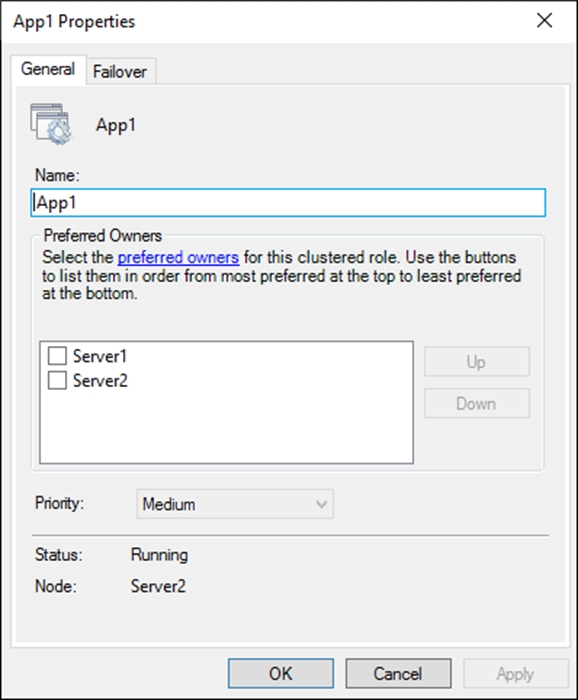
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)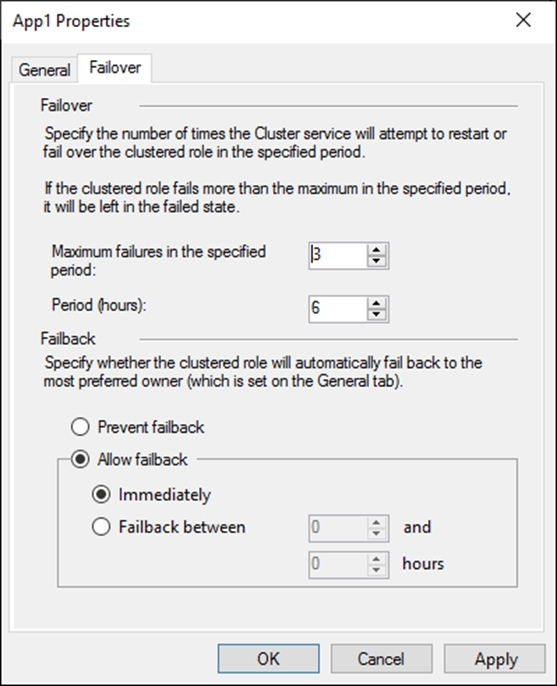
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you increase the priority of Server2 in the Preferred Owners list.
Does this meet the goal?
Answer:
B
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource's cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting "prevent failback." When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
Answer:
D
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
Answer:
D
HOTSPOT -
You have a Hyper-V failover cluster named Cluster1 at a main datacenter. Cluster1 contains two nodes that have the Hyper-V server role installed. Cluster1 hosts
10 highly available virtual machines.
You have a cluster named Cluster2 in a disaster recovery site. Cluster2 contains two nodes that have the Hyper-V server role installed.
You plan to use Hyper-V Replica to replicate the virtual machines from Cluster1 to Cluster2.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: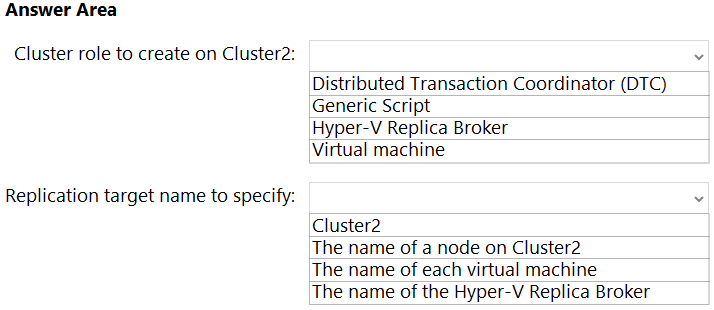
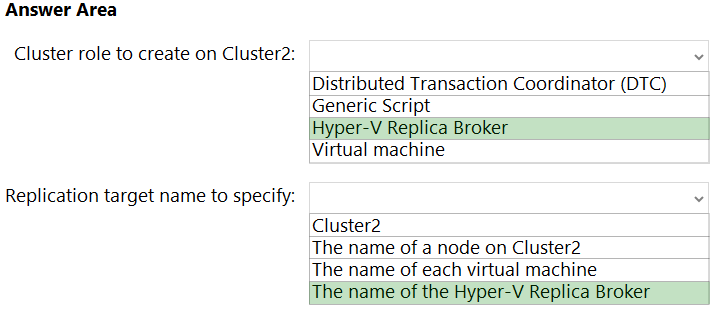
Answer:
Reference:
https://docs.microsoft.com/en-us/virtualization/community/team-blog/2012/20120327-why-is-the-hyper-v-replica-broker-required