Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains the following resources:
✑ A virtual network named Vnet1
A subnet named Subnet1 in Vnet1 -
✑ A virtual machine named VM1 that connects to Subnet1
✑ Three storage accounts named storage1, storage2, and storage3
You need to ensure that VM1 can access storage1. VM1 must be prevented from accessing any other storage accounts.
Solution: You create a network security group (NSG). You configure a service tag for Microsoft.Storage and link the tag to Subnet1.
Does this meet the goal?
Answer:
B
You need to use Traffic Analytics to monitor the usage of applications deployed to Azure virtual machines.
Which Azure Network Watcher feature should you implement first?
Answer:
A
Network Watcher: A regional service that enables you to monitor and diagnose conditions at a network scenario level in Azure. You can turn NSG flow logs on and off with Network Watcher.
Network security group (NSG) flow logs is a feature of Azure Network Watcher that allows you to log information about IP traffic flowing through an NSG.
Why use NSG Flow Logs?
It is vital to monitor, manage, and know your own network for uncompromised security, compliance, and performance.
Common use cases include Network Monitoring: Identify unknown or undesired traffic. Monitor traffic levels and bandwidth consumption. Filter flow logs by IP and port to understand application behavior.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-overview
HOTSPOT -
You have an Azure subscription that contains the virtual machines shown in the following table.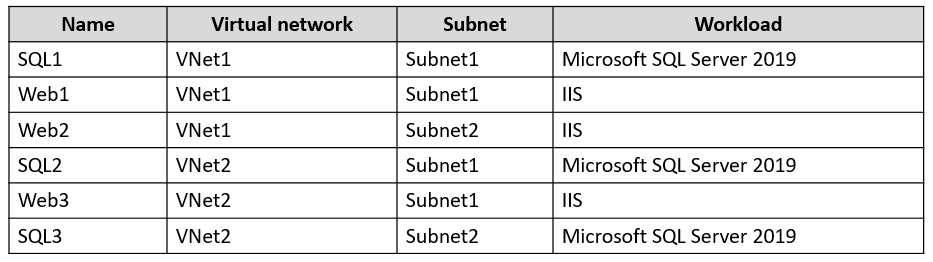
VNet1 and VNet2 are NOT connected to each other.
You need to block traffic from SQL Server 2019 to IIS by using application security groups. The solution must minimize administrative effort.
How should you configure the application security groups? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: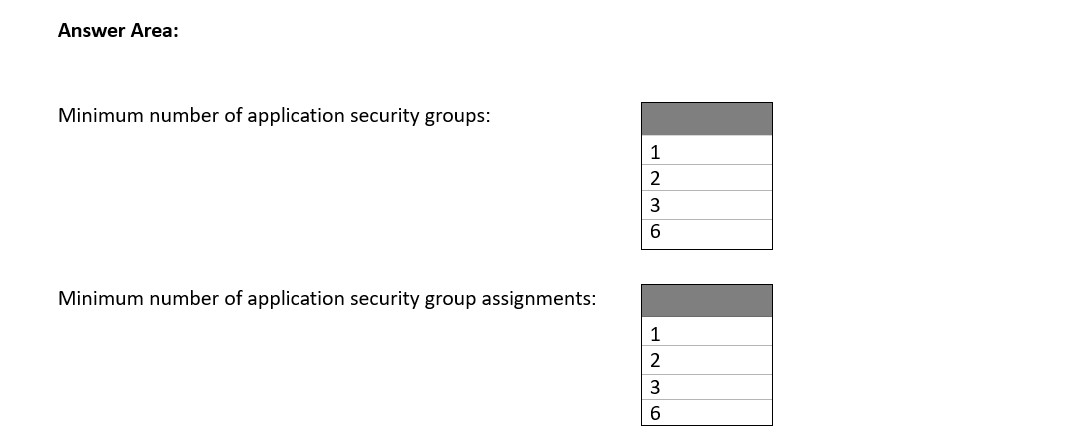
Answer:
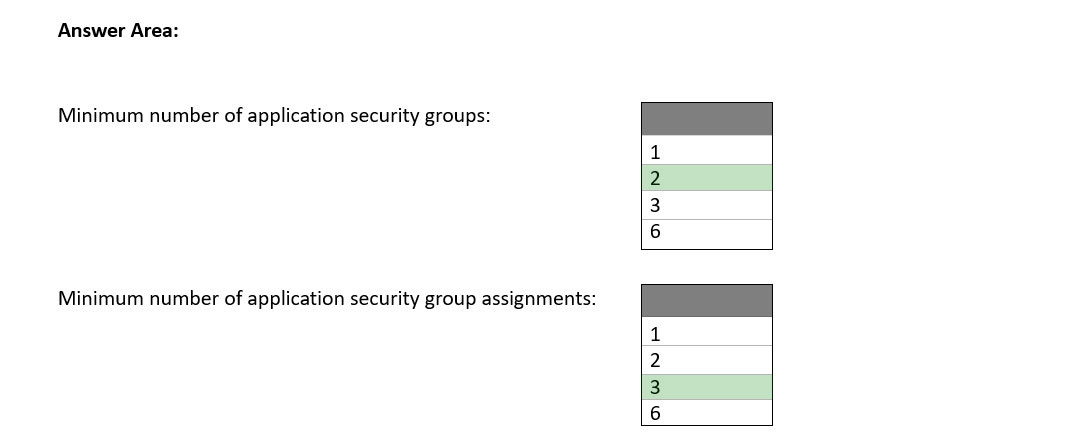
Box 1: 2 -
All network interfaces assigned to an application security group have to exist in the same virtual network that the first network interface assigned to the application security group is in.
We need one application security group for each of the two virtual networks.
Box 2: 3 -
One network assignment in VNet1. Two network assignments in VNET2.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/application-security-groups
HOTSPOT -
You have an Azure virtual network that contains the subnets shown in the following table.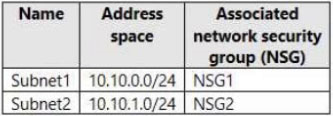
In.NSG1, you create inbound rules as shown in the following table.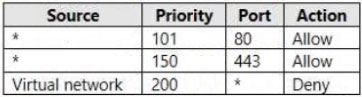
NSG2 has only the default rules configured.
You have the Azure virtual machines shown in the following table.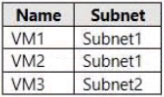
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: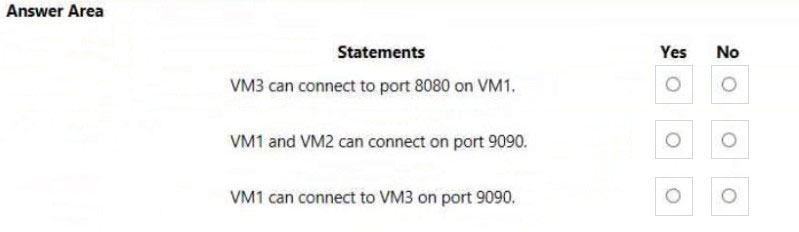
Answer:
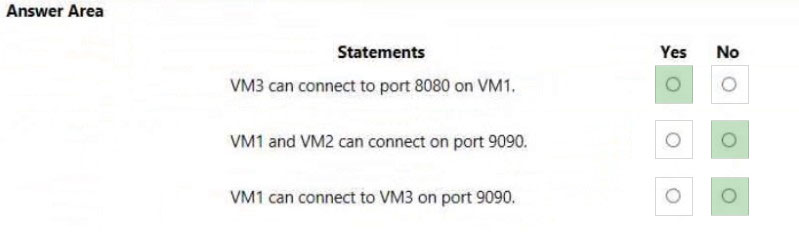
Box 1: Yes -
VM3 is Subnet2. NSG2 applies. The default rule will allow communication.
Box 2: No -
VM1 & VM2 is in Subnet1. NSG1 applies. Only traffic on ports 80 and 443 will be allowed. Connection on port 9090 will be denied.
Note: Priority: A number between 100 and 4096. Rules are processed in priority order, with lower numbers processed before higher numbers, because lower numbers have higher priority. Once traffic matches a rule, processing stops. As a result, any rules that exist with lower priorities (higher numbers) that have the same attributes as rules with higher priorities are not processed.
Box 3: No -
VM1 is in Subnet1. NSG1 applies. Only traffic on ports 80 and 443 will be allowed. Connection on port 9090 will be denied.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
You have the Azure virtual networks shown in the following table.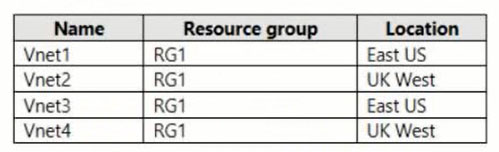
You have the Azure resources shown in the following table.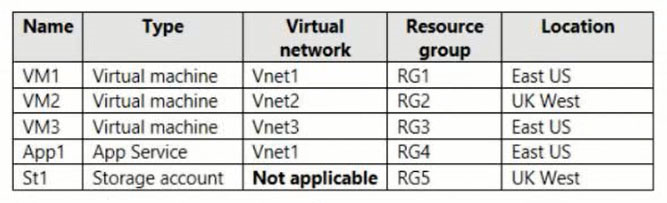
You need to check latency between the resources by using connection monitors in Azure Network Watcher.
What is the minimum number of connection monitors that you must create?
Answer:
C
In the Region UK West region we have one single virtual machine VM2.
There is not anything to monitor here.
In the Region East US region we have two virtual machines VM1 & VM3, and App1.
We can monitor the connections: VM1-VM3, VM1-App1, VM3-App1.
Note: Connection Monitor includes the following entities:
Connection monitor resource: A region-specific Azure resource. All the following entities are properties of a connection monitor resource.
Endpoint: A source or destination that participates in connectivity checks. Examples of endpoints include Azure VMs, on-premises agents, URLs, and IP addresses.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/connection-monitor-overview
You have the Azure resources shown in the following table.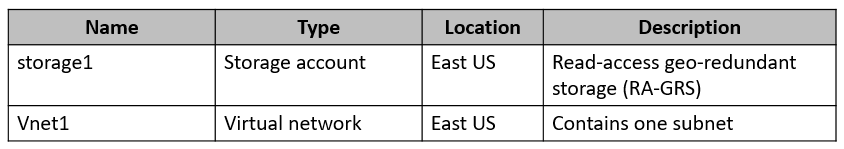
You configure storage1 to provide access to the subnet in Vnet1 by using a service endpoint.
You need to ensure that you can use the service endpoint to connect to the read-only endpoint of storage1 in the paired Azure region.
What should you do first?
Answer:
B
The Azure storage firewall provides access control for the public endpoint of your storage account. You can also use the firewall to block all access through the public endpoint when using private endpoints.
Note: By default, service endpoints work between virtual networks and service instances in the same Azure region. When using service endpoints with Azure
Storage, service endpoints also work between virtual networks and service instances in a paired region.
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security
You have an Azure subscription that contains multiple virtual machines in the West US Azure region.
You need to use Traffic Analytics.
Which two resources should you create? Each correct answer presents part of the solution. (Choose two.)
NOTE: Each correct answer selection is worth one point.
Answer:
BC
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/traffic-analytics
HOTSPOT -
You have an Azure subscription that contains the virtual machines shown in the following table.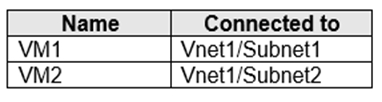
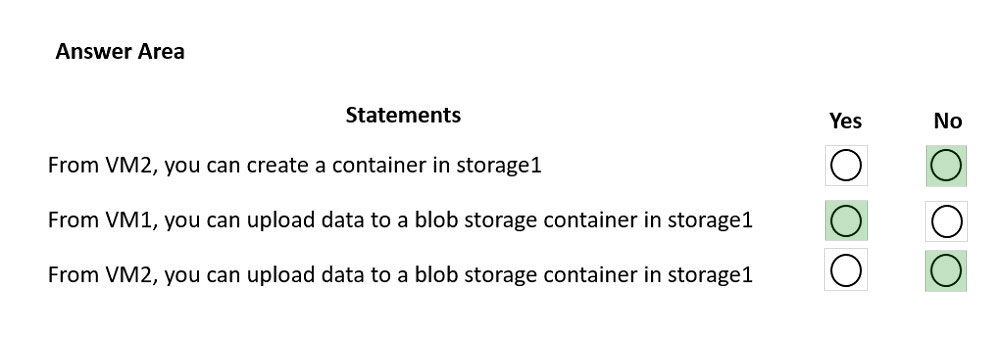
Subnet1 and Subnet2 are associated to a network security group (NSG) named NSG1 that has the following outbound rule:
✑ Priority: 100
✑ Port: Any
✑ Protocol: Any
✑ Source: Any
✑ Destination: Storage
✑ Action: Deny
You create a private endpoint that has the following settings:
✑ Name: Private1
✑ Resource type: Microsoft.Storage/storageAccounts
✑ Resource: storage1
✑ Target sub-resource: blob
✑ Virtual network: Vnet1
✑ Subnet: Subnet1
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: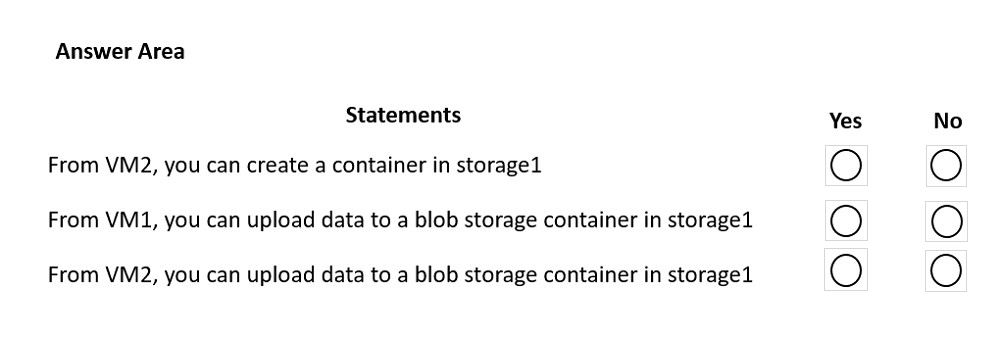
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/private-link/disable-private-endpoint-network-policy
HOTSPOT -
You have an Azure firewall shown in the following exhibit.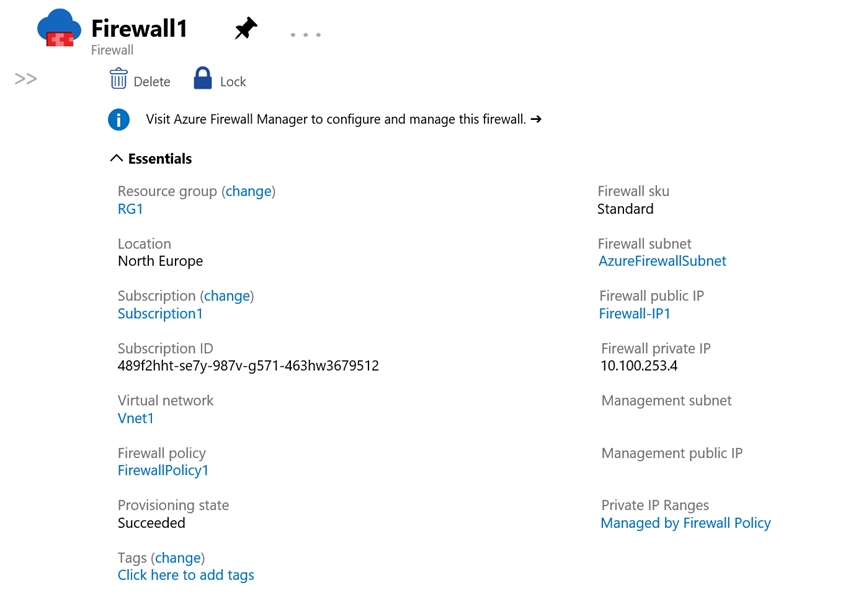
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: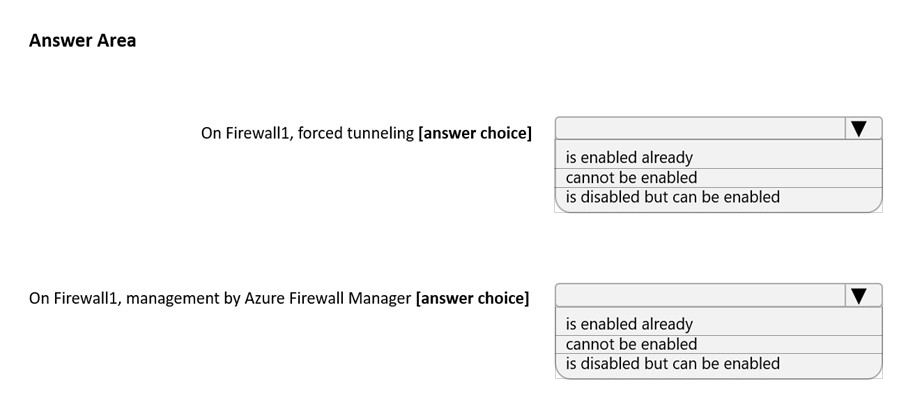
Answer:
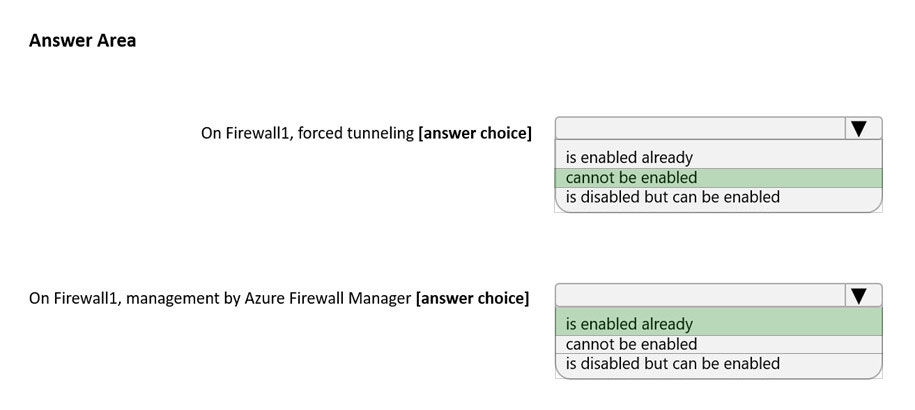
Box 1:
If forced tunneling was enabled, the Firewall Subnet would be named AzureFirewallManagementSubnet. Forced tunneling can only be enabled during the creation of the firewall. It cannot be enabled after the firewall has been deployed.
Box 2:
The ג€Visit Azure Firewall Manager to configure and manage this firewallג€ link in the exhibit shows that the firewall is managed by Azure Firewall Manager.
You have a hybrid environment that uses ExpressRoute to connect an on-premises network and Azure.
You need to log the uptime and the latency of the connection periodically by using an Azure virtual machine and an on-premises virtual machine.
What should you use?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/connection-monitor