HOTSPOT -
You have the Azure virtual networks shown in the following table.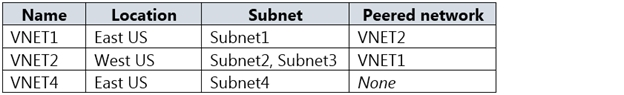
You have the Azure virtual machines shown in the following table.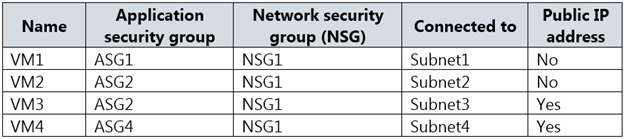
The firewalls on all the virtual machines allow ping traffic.
NSG1 is configured as shown in the following exhibit.
Inbound security rules -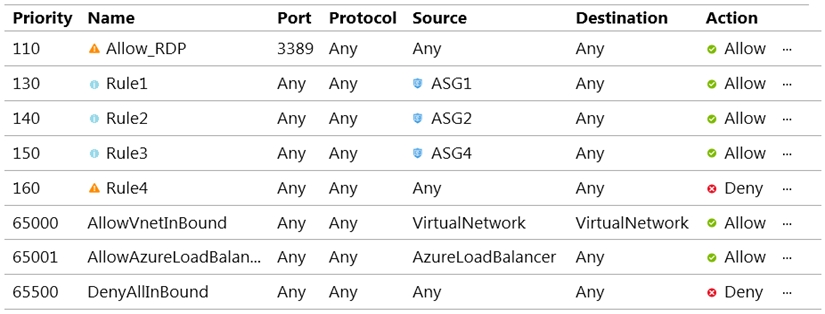
Outbound security rules -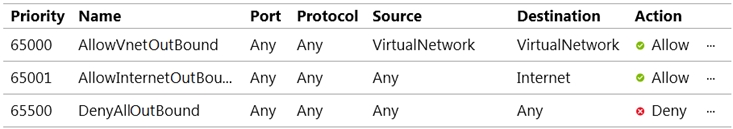
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: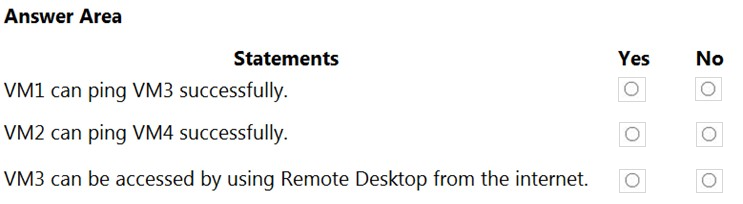
Answer:
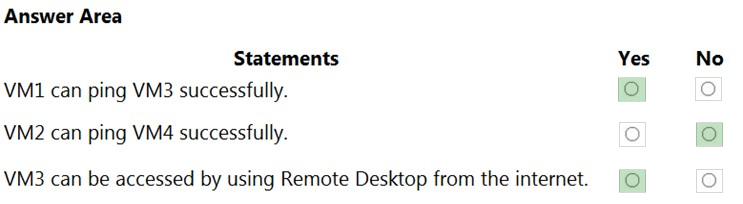
Box 1: Yes -
VM1 and VM3 are on peered VNets. The firewall rules with a source of ASG1 and ASG2 allow 'any' traffic on 'any' protocol so pings are allowed between VM1 and VM3.
Box 2: No -
VM2 and VM4 are on separate VNets and the VNets are not peered. Therefore, the pings would have to go over the Internet. VM4 does have a public IP and the firewall allows pings. However, for VM2 to be able to ping VM4, VM2 would also need a public IP address. In Azure, pings don't go out through the default gateway as they would in a physical network. For an Azure VM to ping external IPs, the VM must have a public IP address assigned to it.
Box 3: Yes -
VM3 has a public IP address and the firewall allows traffic on port 3389.
You have multiple development teams that will create apps in Azure.
You plan to create a standard development environment that will be deployed for each team.
You need to recommend a solution that will enforce resource locks across the development environments and ensure that the locks are applied in a consistent manner.
What should you include in the recommendation?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/azure/governance/blueprints/concepts/resource-locking
You have an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the automatically generated service principal for the AKS cluster to authenticate to the Azure Container Registry.
What should you create?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/aks/kubernetes-service-principal
You have an Azure subscription that contains two virtual machines named VM1 and VM2 that run Windows Server 2019.
You are implementing Update Management in Azure Automation.
You plan to create a new update deployment named Update1.
You need to ensure that Update1 meets the following requirements:
✑ Automatically applies updates to VM1 and VM2.
✑ Automatically adds any new Windows Server 2019 virtual machines to Update1.
What should you include in Update1?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/automation/update-management/configure-groups
You have the Azure virtual machines shown in the following table.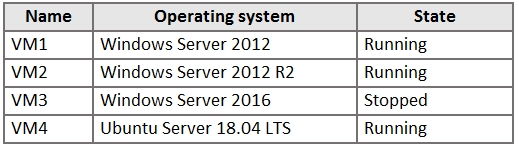
For which virtual machines can you enable Update Management?
Answer:
C
References:
https://docs.microsoft.com/en-us/azure/automation/automation-update-management?toc=%2Fazure%2Fautomation%2Ftoc.json
DRAG DROP -
You have an Azure subscription named Sub1.
You have an Azure Active Directory (Azure AD) group named Group1 that contains all the members of your IT team.
You need to ensure that the members of Group1 can stop, start, and restart the Azure virtual machines in Sub1. The solution must use the principle of least privilege.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: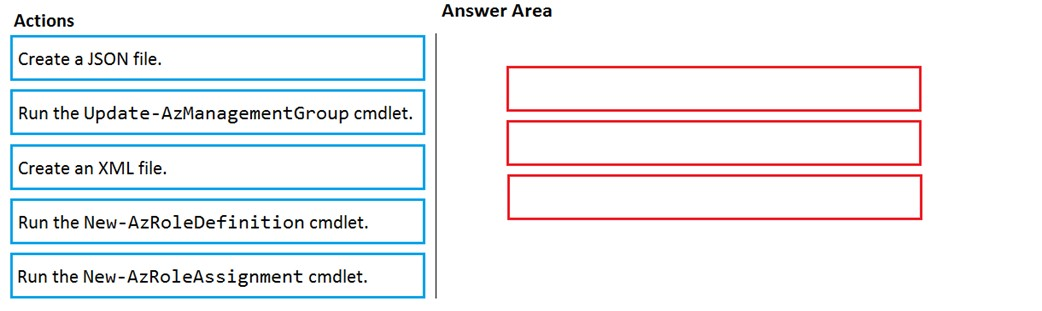
Answer:
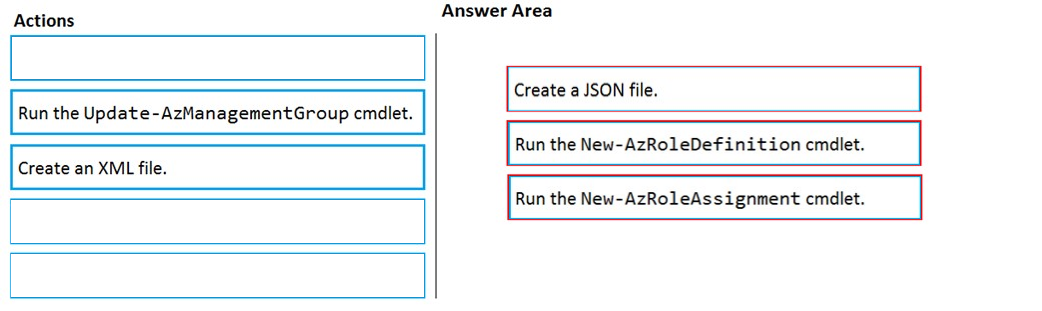
References:
https://www.petri.com/cloud-security-create-custom-rbac-role-microsoft-azure
DRAG DROP -
You have an Azure subscription that contains the following resources:
A virtual network named VNET1 that contains two subnets named Subnet1 and Subnet2.
✑ A virtual machine named VM1 that has only a private IP address and connects to Subnet1.
You need to ensure that Remote Desktop connections can be established to VM1 from the internet.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange then in the correct order.
Select and Place: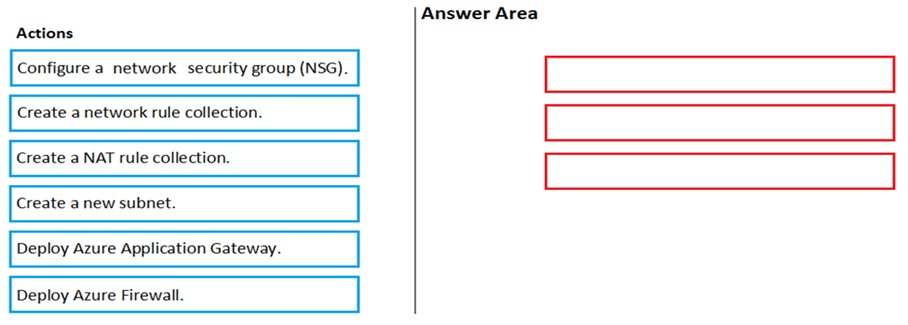
Answer:
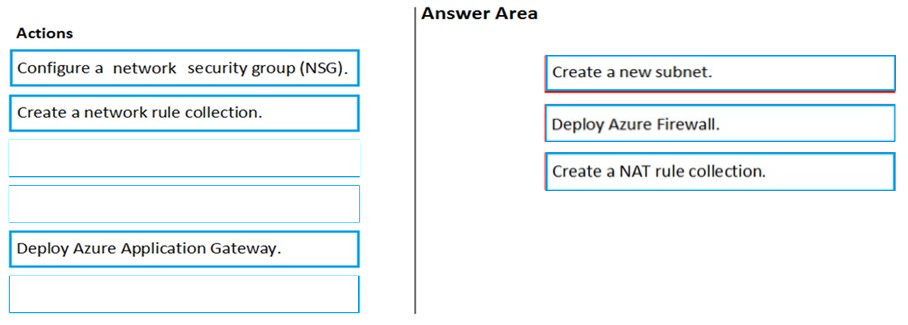
HOTSPOT -
You have an Azure subscription that is linked to an Azure Active Directory (Azure AD). The tenant contains the users shown in the following table.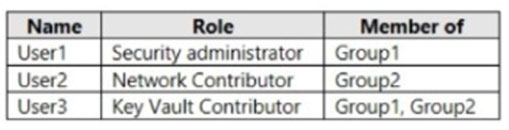
You have an Azure key vault named Vault1 that has Purge protection set to Disable. Vault1 contains the access policies shown in the following table.
You create role assignments for Vault1 as shown in the following table.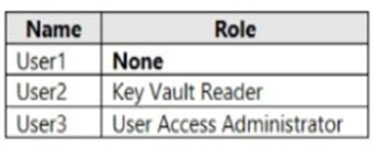
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: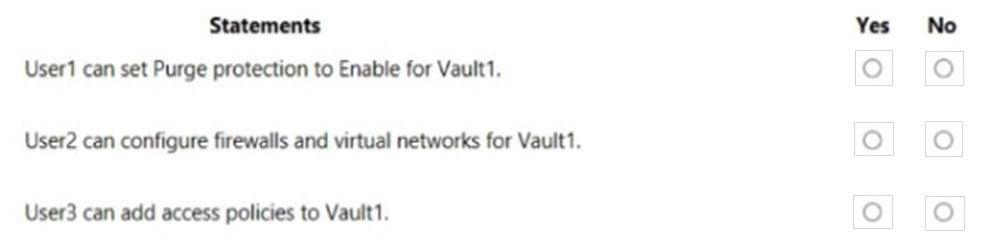
Answer:
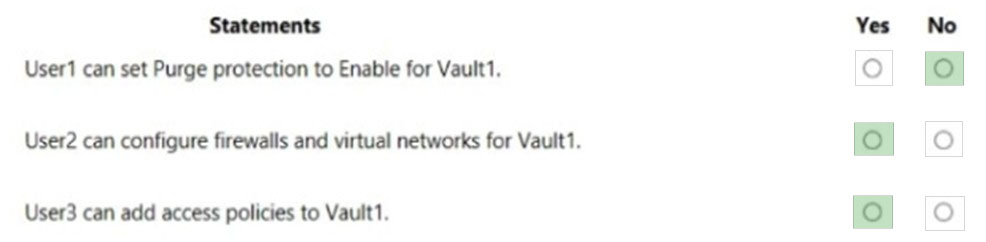
Box 1: No -
Resource Policy Contributor or Security Administrator is required.
User1 is Security Administrator only with the no specific permission granted to Vault1.
The Security Admin can view and update permissions for Security Center. Same permissions as the Security Reader role and can also update the security policy and dismiss alerts and recommendations.
However:
Box 2: Yes -
User2 is a Network Contributor, with Select All Key, Secret & Certificate permissions, and Key Vault Reader.
The Network Contributor role lets you manage networks, but not access to them.
Box 3: Yes -
User3 is a Key Vault Contributor and a User Access Administrator for Vault.
The Key Vault Contributor role allows you to manage key vaults, but does not allow you to assign roles in Azure RBAC, and does not allow you to access secrets, keys, or certificates.
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles#network-contributor https://charbelnemnom.com/enable-purge-protection-key-vault-azure-policy/
HOTSPOT
-
You have an Azure subscription that contains the virtual machines shown in the following table.
VNET1, VNET2, and VNET3 are peered with each other.
You perform the following actions:
• Create two application security groups named ASG1 and ASG2 in the West US region.
• Add the network interface of VM1 to ASG1.
The network interfaces of which virtual machines can you add to ASG1 and ASG2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:

You have an Azure subscription that contains an Azure key vault.
You need to configure the maximum number of days for which new keys are valid. The solution must minimize administrative effort.
What should you use?
Answer:
D