HOTSPOT -
You have an Azure Web app that uses Cosmos DB as a data store. You create a CosmosDB container by running the following PowerShell script:
$resourceGroupName = "testResourceGroup"
$accountName = "testCosmosAccount"
$databaseName = "testDatabase"
$containerName = "testContainer"
$partitionKeyPath = "/EmployeeId"
$autoscaleMaxThroughput = 5000
New-AzCosmosDBSqlContainer -
-ResourceGroupName $resourceGroupName
-AccountName $accountName
-DatabaseName $databaseName
-Name $containerName
-PartitionKeyKind Hash
-PartitionKeyPath $partitionKeyPath
-AutoscaleMaxThroughput $autoscaleMaxThroughput
You create the following queries that target the container:
SELECT * FROM c WHERE c.EmployeeId > '12345'
SELECT * FROM c WHERE c.UserID = '12345'
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:

Box 1: No -
You set the highest, or maximum RU/s Tmax you don't want the system to exceed. The system automatically scales the throughput T such that 0.1* Tmax <= T <=
Tmax.
In this example we have autoscaleMaxThroughput = 5000, so the minimum throughput for the container is 500 R/Us.
Box 2: No -
First query: SELECT * FROM c WHERE c.EmployeeId > '12345'
Here's a query that has a range filter on the partition key and won't be scoped to a single physical partition. In order to be an in-partition query, the query must have an equality filter that includes the partition key:
SELECT * FROM c WHERE c.DeviceId > 'XMS-0001'
Box 3: Yes -
Example of In-partition query:
Consider the below query with an equality filter on DeviceId. If we run this query on a container partitioned on DeviceId, this query will filter to a single physical partition.
SELECT * FROM c WHERE c.DeviceId = 'XMS-0001'
Reference:
https://docs.microsoft.com/en-us/azure/cosmos-db/how-to-choose-offer https://docs.microsoft.com/en-us/azure/cosmos-db/how-to-query-container
HOTSPOT -
You are developing a web application that makes calls to the Microsoft Graph API. You register the application in the Azure portal and upload a valid X509 certificate.
You create an appsettings.json file containing the certificate name, client identifier for the application, and the tenant identifier of the Azure Active Directory (Azure
AD). You create a method named ReadCertificate to return the X509 certificate by name.
You need to implement code that acquires a token by using the certificate.
How should you complete the code segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: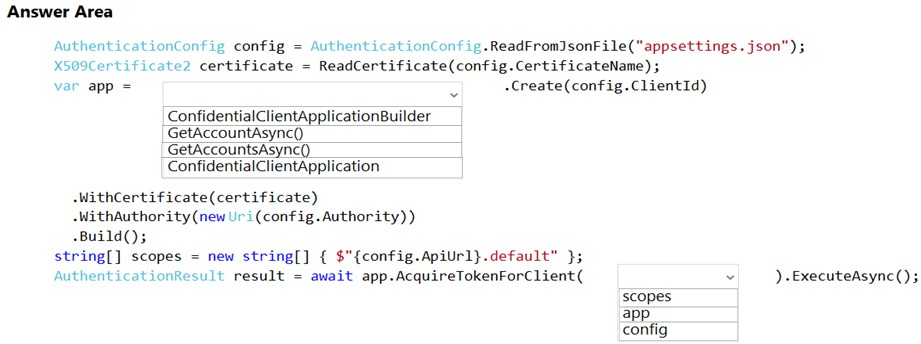
Answer:
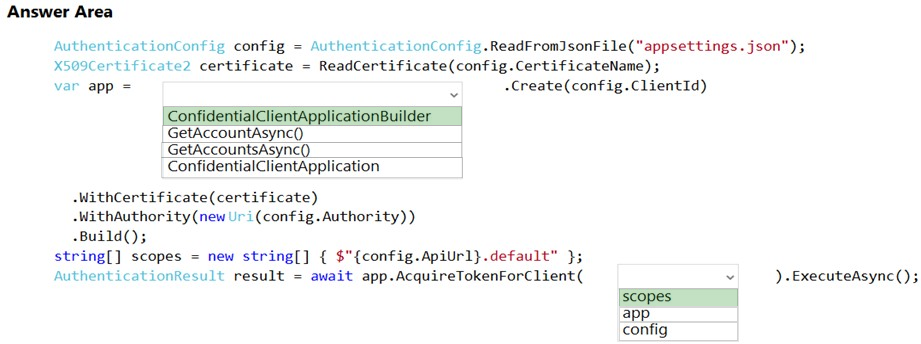
Box 1: ConfidentialClientApplicationBuilder
Here's the code to instantiate the confidential client application with a client secret: app = ConfidentialClientApplicationBuilder.Create(config.ClientId)
.WithClientSecret(config.ClientSecret)
.WithAuthority(new Uri(config.Authority))
.Build();
Box 2: scopes -
After you've constructed a confidential client application, you can acquire a token for the app by calling AcquireTokenForClient, passing the scope, and optionally forcing a refresh of the token.
Sample code: result = await app.AcquireTokenForClient(scopes)
.ExecuteAsync();
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/scenario-daemon-app-configuration https://docs.microsoft.com/en-us/azure/active-directory/develop/scenario-daemon-acquire-token
HOTSPOT -
You develop a containerized application. You plan to deploy the application to a new Azure Container instance by using a third-party continuous integration and continuous delivery (CI/CD) utility.
The deployment must be unattended and include all application assets. The third-party utility must only be able to push and pull images from the registry. The authentication must be managed by Azure Active Directory (Azure AD). The solution must use the principle of least privilege.
You need to ensure that the third-party utility can access the registry.
Which authentication options should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: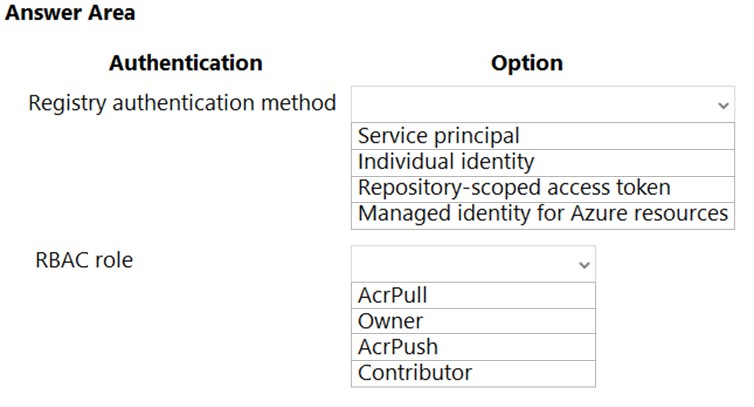
Answer:
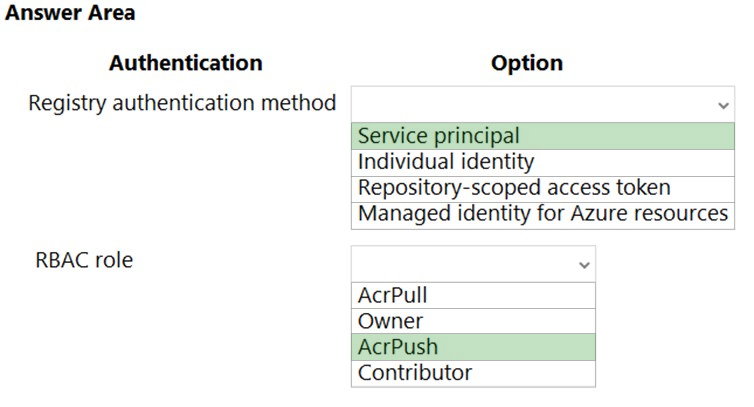
Box 1: Service principal -
Applications and container orchestrators can perform unattended, or "headless," authentication by using an Azure Active Directory (Azure AD) service principal.
Incorrect Answers:
✑ Individual AD identity does not support unattended push/pull
✑ Repository-scoped access token is not integrated with AD identity
✑ Managed identity for Azure resources is used to authenticate to an Azure container registry from another Azure resource.
Box 2: AcrPush -
AcrPush provides pull/push permissions only and meets the principle of least privilege.
Incorrect Answers:
AcrPull only allows pull permissions it does not allow push permissions.
✑ Owner and Contributor allow pull/push permissions but does not meet the principle of least privilege.
Reference:
https://docs.microsoft.com/en-us/azure/container-registry/container-registry-authentication?tabs=azure-cli https://docs.microsoft.com/en-us/azure/container-registry/container-registry-roles?tabs=azure-cli
You deploy an Azure App Service web app. You create an app registration for the app in Azure Active Directory (Azure AD) and Twitter.
The app must authenticate users and must use SSL for all communications. The app must use Twitter as the identity provider.
You need to validate the Azure AD request in the app code.
What should you validate?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-auth-aad-app?tabs=dotnet
A development team is creating a new REST API. The API will store data in Azure Blob storage. You plan to deploy the API to Azure App Service.
Developers must access the Azure Blob storage account to develop the API for the next two months. The Azure Blob storage account must not be accessible by the developers after the two-month time period.
You need to grant developers access to the Azure Blob storage account.
What should you do?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
DRAG DROP -
You develop a web application.
You need to register the application with an active Azure Active Directory (Azure AD) tenant.
Which three actions should you perform in sequence? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: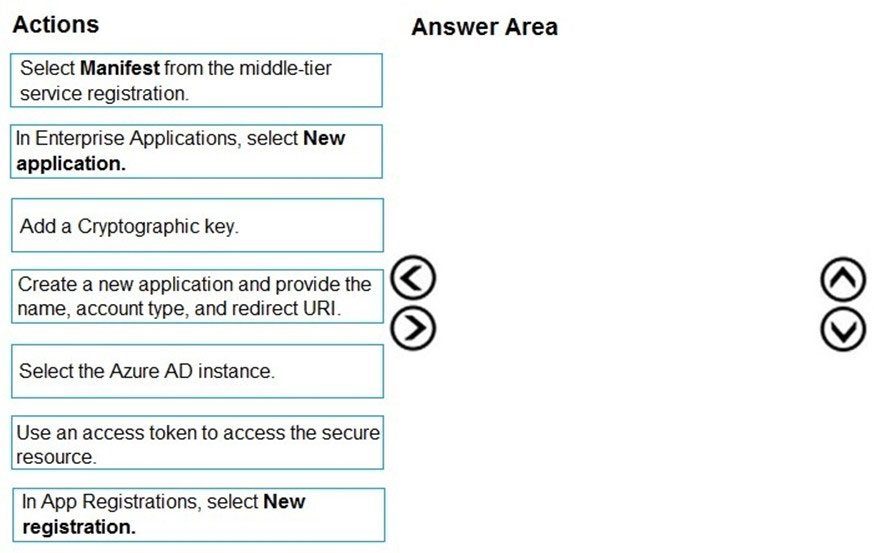
Answer:
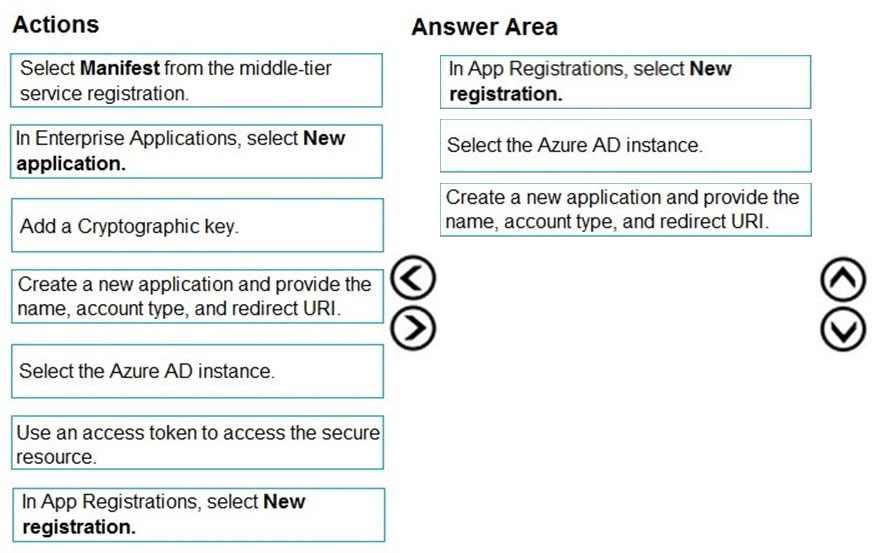
Register a new application using the Azure portal
1. Sign in to the Azure portal using either a work or school account or a personal Microsoft account.
2. If your account gives you access to more than one tenant, select your account in the upper right corner. Set your portal session to the Azure AD tenant that you want.
3. Search for and select Azure Active Directory. Under Manage, select App registrations.
4. Select New registration. (Step 1)
5. In Register an application, enter a meaningful application name to display to users.
6. Specify who can use the application. Select the Azure AD instance. (Step 2)
7. Under Redirect URI (optional), select the type of app you're building: Web or Public client (mobile & desktop). Then enter the redirect URI, or reply URL, for your application. (Step 3)
8. When finished, select Register.
You have a new Azure subscription. You are developing an internal website for employees to view sensitive data. The website uses Azure Active Directory (Azure
AD) for authentication.
You need to implement multifactor authentication for the website.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
BC
B: MFA Enabled by conditional access policy. It is the most flexible means to enable two-step verification for your users. Enabling using conditional access policy only works for Azure MFA in the cloud and is a premium feature of Azure AD.
C: Multi-Factor Authentication comes as part of the following offerings:
✑ Azure Active Directory Premium licenses - Full featured use of Azure Multi-Factor Authentication Service (Cloud) or Azure Multi-Factor Authentication Server
(On-premises).
✑ Multi-Factor Authentication for Office 365
✑ Azure Active Directory Global Administrators
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-getstarted
DRAG DROP -
An organization plans to deploy Azure storage services.
You need to configure shared access signature (SAS) for granting access to Azure Storage.
Which SAS types should you use? To answer, drag the appropriate SAS types to the correct requirements. Each SAS type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: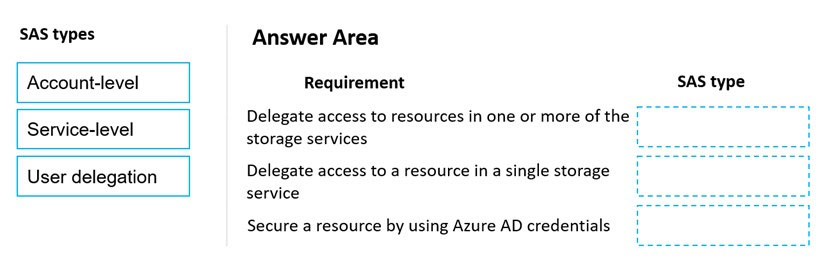
Answer:
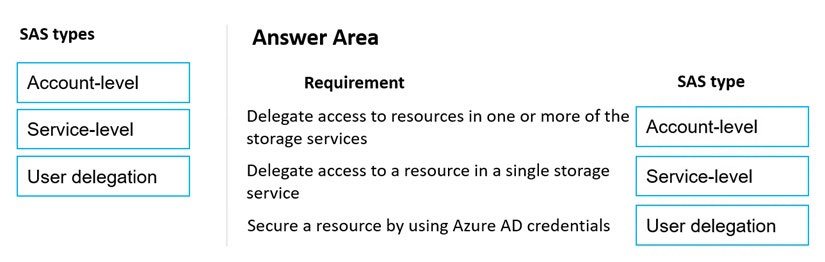
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
HOTSPOT -
You are developing an ASP.NET Core app that includes feature flags which are managed by Azure App Configuration. You create an Azure App Configuration store named AppFeatureflagStore as shown in the exhibit: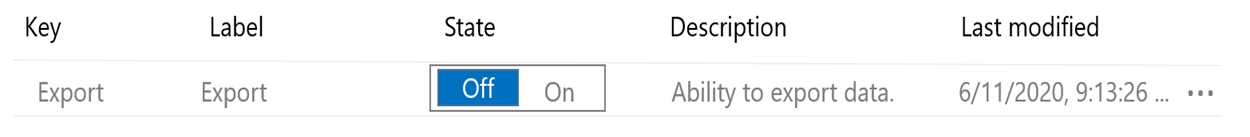
You must be able to use the feature in the app by using the following markup:
You need to update the app to use the feature flag.
Which values should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: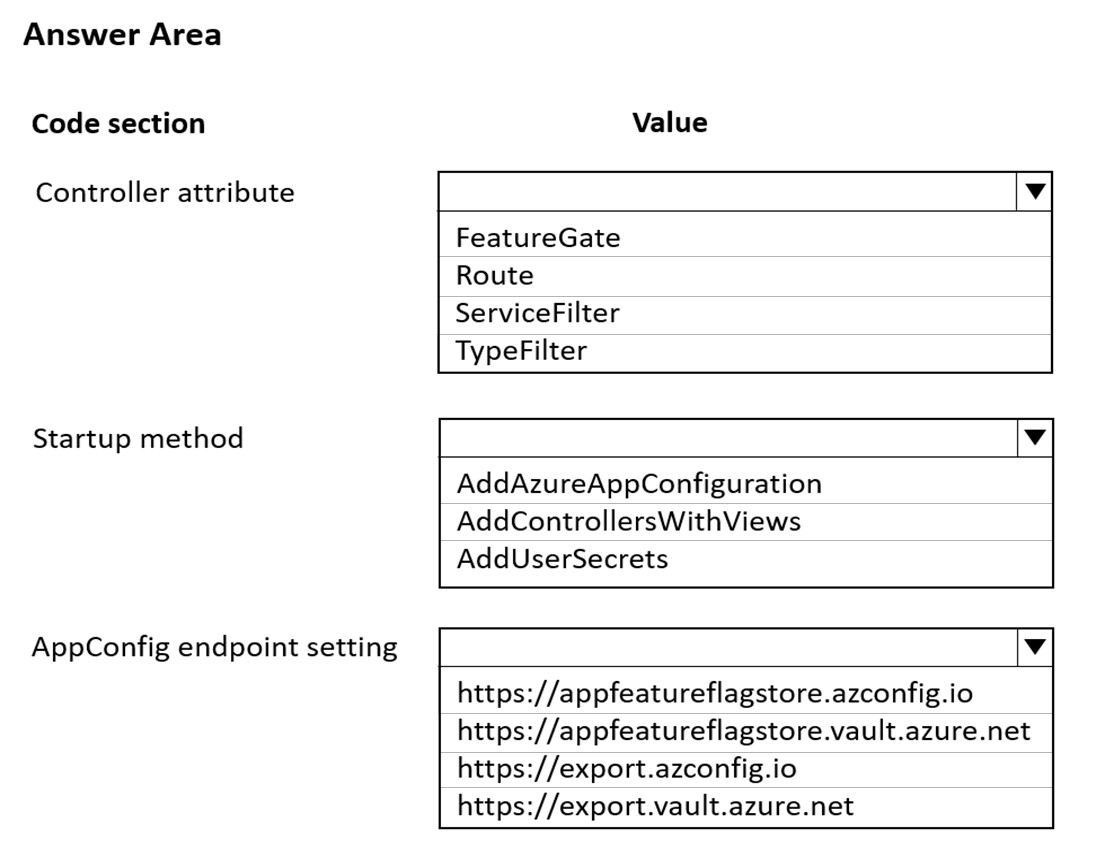
Answer:
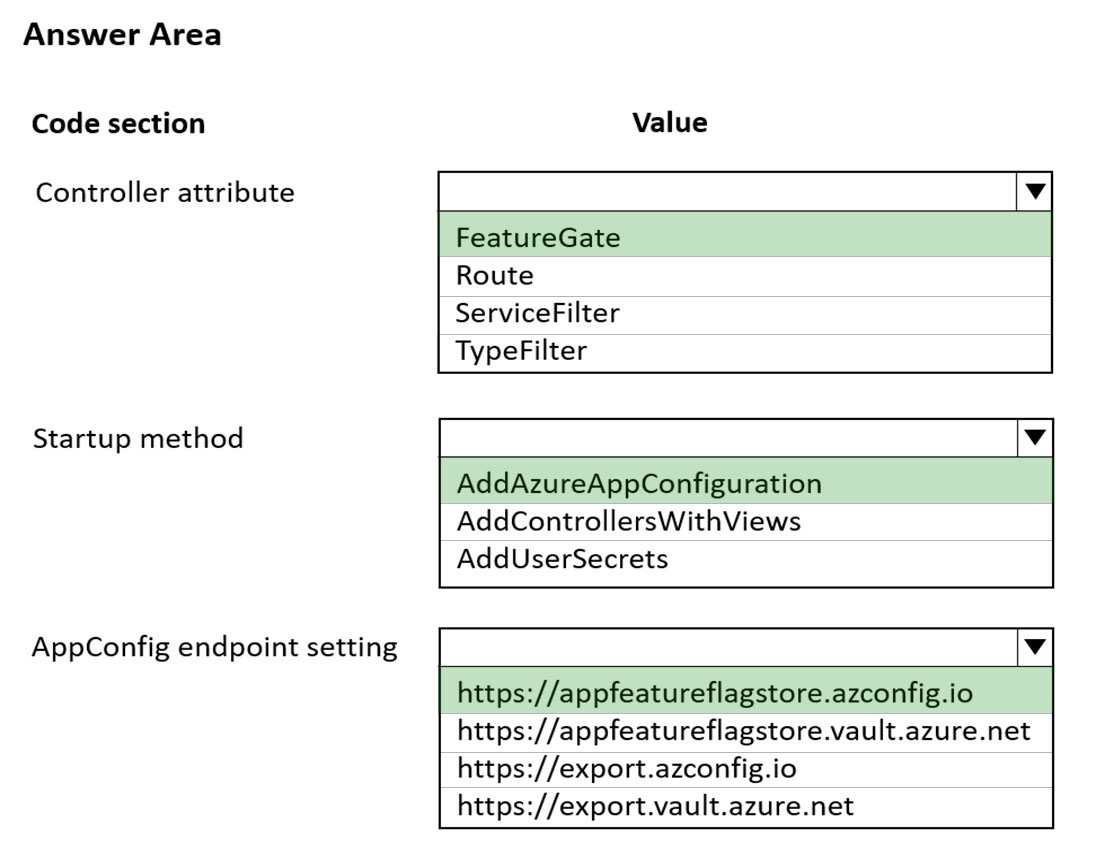
Box 1: FeatureGate -
You can use the FeatureGate attribute to control whether a whole controller class or a specific action is enabled.
Box 2: AddAzureAppConfiguration -
The extension method AddAzureAppConfiguration is used to add the Azure App Configuration Provider.
Box 3: https://appfeatureflagstore.azconfig.io
You need to request the access token with resource=https://<yourstorename>.azconfig.io
Reference:
https://docs.microsoft.com/en-us/azure/azure-app-configuration/use-feature-flags-dotnet-core https://csharp.christiannagel.com/2020/05/19/azureappconfiguration/ https://stackoverflow.com/questions/61899063/how-to-use-azure-app-configuration-rest-api
HOTSPOT -
You have a single page application (SPA) web application that manages information based on data returned by Microsoft Graph from another company's Azure
Active Directory (Azure AD) instance.
Users must be able to authenticate and access Microsoft Graph by using their own company's Azure AD instance.
You need to configure the application manifest for the app registration.
How should you complete the manifest? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: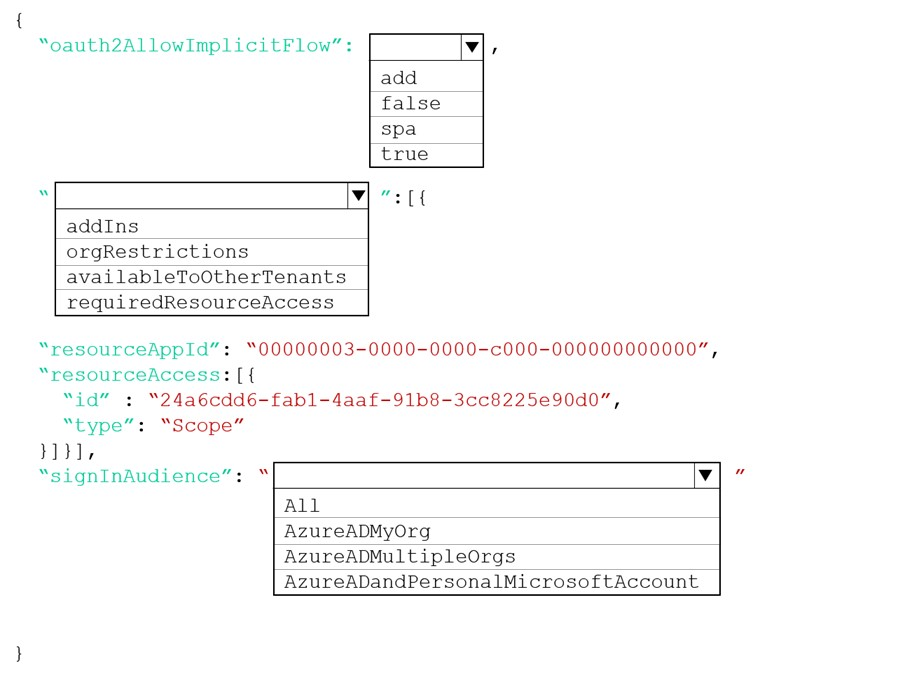
Answer:
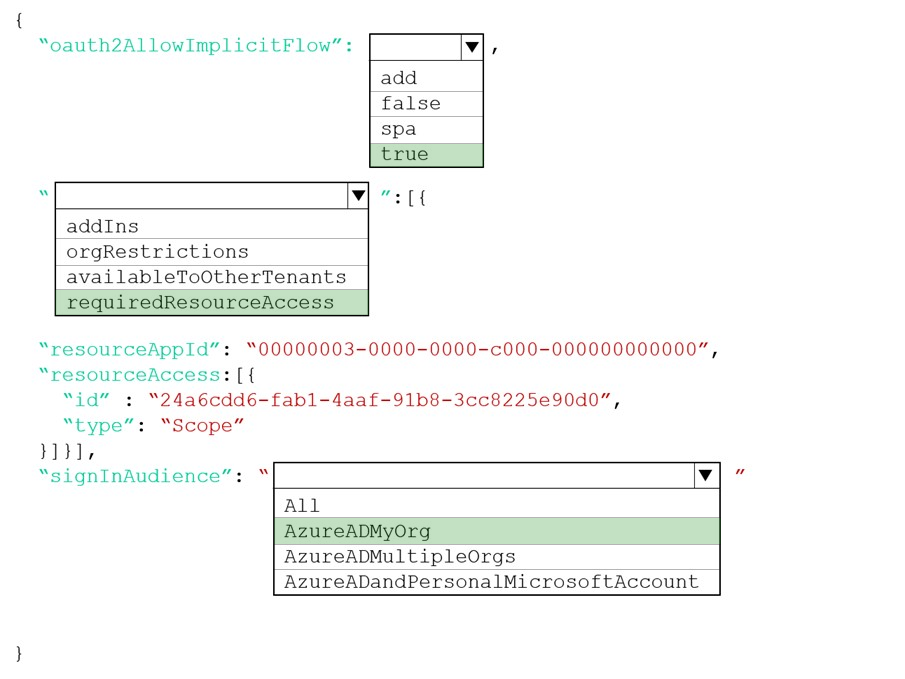
Box 1: true -
The oauth2AllowImplicitFlow attribute Specifies whether this web app can request OAuth2.0 implicit flow access tokens. The default is false. This flag is used for browser-based apps, like JavaScript single-page apps.
In implicit flow, the app receives tokens directly from the Azure Active Directory (Azure AD) authorize endpoint, without any server-to-server exchange. All authentication logic and session handling is done entirely in the JavaScript client with either a page redirect or a pop-up box.
Box 2: requiredResourceAccess -
With dynamic consent, requiredResourceAccess drives the admin consent experience and the user consent experience for users who are using static consent.
However, this parameter doesn't drive the user consent experience for the general case. resourceAppId is the unique identifier for the resource that the app requires access to. This value should be equal to the appId declared on the target resource app. resourceAccess is an array that lists the OAuth2.0 permission scopes and app roles that the app requires from the specified resource. Contains the id and type values of the specified resources.
Example:
"requiredResourceAccess": [
{
"resourceAppId": "00000002-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "311a71cc-e848-46a1-bdf8-97ff7156d8e6",
"type": "Scope"
}
]
}
],
Incorrect Answers:
✑ The legacy attribute availableToOtherTenants is no longer supported.
✑ The addIns attribute defines custom behavior that a consuming service can use to call an app in specific contexts. For example, applications that can render file streams may set the addIns property for its "FileHandler" functionality. This parameter will let services like Microsoft 365 call the application in the context of a document the user is working on.
Example:
"addIns": [
{
"id": "968A844F-7A47-430C-9163-07AE7C31D407",
"type":" FileHandler",
"properties": [
{
"key": "version",
"value": "2"
}
]
}
],
Box 3: AzureADMyOrg -
The signInAudience attribute specifies what Microsoft accounts are supported for the current application. Supported values are:
✑ AzureADMyOrg - Users with a Microsoft work or school account in my organization's Azure AD tenant (for example, single tenant)
✑ AzureADMultipleOrgs - Users with a Microsoft work or school account in any organization's Azure AD tenant (for example, multi-tenant)
✑ AzureADandPersonalMicrosoftAccount - Users with a personal Microsoft account, or a work or school account in any organization's Azure AD tenant
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/reference-app-manifest https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-implicit-grant-flow