You manage a data processing application that receives requests from an Azure Storage queue.
You need to manage access to the queue. You have the following requirements:
✑ Provide other applications access to the Azure queue.
✑ Ensure that you can revoke access to the queue without having to regenerate the storage account keys.
✑ Specify access at the queue level and not at the storage account level.
Which type of shared access signature (SAS) should you use?
Answer:
A
A service SAS is secured with the storage account key. A service SAS delegates access to a resource in only one of the Azure Storage services: Blob storage,
Queue storage, Table storage, or Azure Files.
Stored access policies give you the option to revoke permissions for a service SAS without having to regenerate the storage account keys.
Incorrect Answers:
Account SAS: Account SAS is specified at the account level. It is secured with the storage account key.
User Delegation SAS: A user delegation SAS applies to Blob storage only.
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
HOTSPOT -
You are developing an application to store and retrieve data in Azure Blob storage. The application will be hosted in an on-premises virtual machine (VM). The
VM is connected to Azure by using a Site-to-Site VPN gateway connection. The application is secured by using Azure Active Directory (Azure AD) credentials.
The application must be granted access to the Azure Blob storage account with a start time, expiry time, and read permissions. The Azure Blob storage account access must use the Azure AD credentials of the application to secure data access. Data access must be able to be revoked if the client application security is breached.
You need to secure the application access to Azure Blob storage.
Which security features should you use? To answer select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: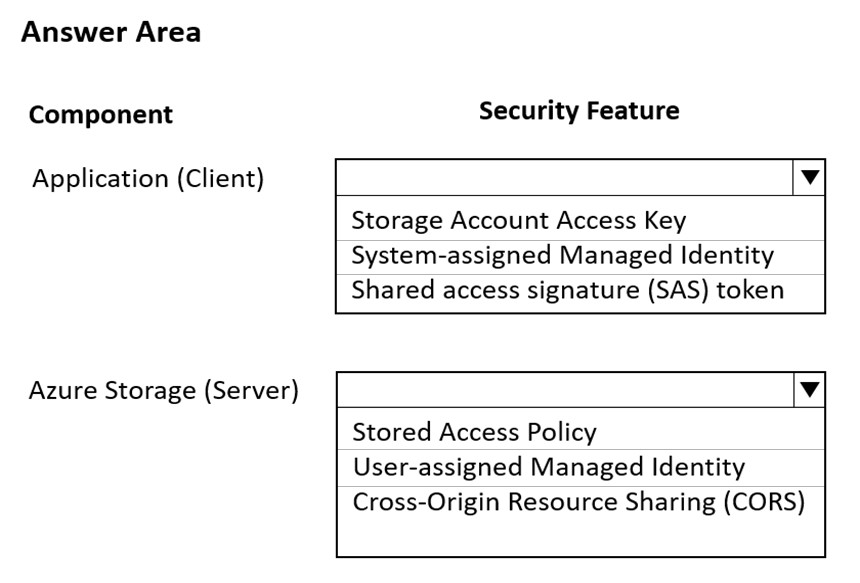
Answer:
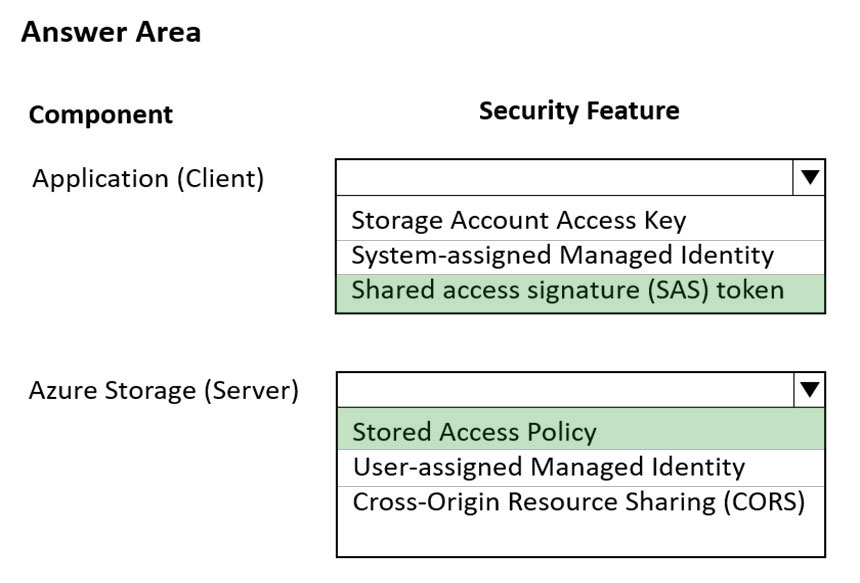
Box 1: Shared access signature (SAS) token
When your application design requires shared access signatures for access to Blob storage, use Azure AD credentials to create a user delegation SAS when possible for superior security.
Box 2: Stored access policy -
Stored access policies give you the option to revoke permissions for a service SAS without having to regenerate the storage account keys.
A shared access signature can take one of the following two forms:
✑ Service SAS with stored access policy. A stored access policy is defined on a resource container, which can be a blob container, table, queue, or file share.
The stored access policy can be used to manage constraints for one or more service shared access signatures. When you associate a service SAS with a stored access policy, the SAS inherits the constraints ג€" the start time, expiry time, and permissions ג€" defined for the stored access policy.
✑ Ad hoc SAS.
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-sas-overview
You are building a web application that uses the Microsoft identity platform for user authentication.
You are implementing user identification for the web application.
You need to retrieve a claim to uniquely identify a user.
Which claim type should you use?
Answer:
C
oid -The object identifier for the user in Azure AD. This value is the immutable and non-reusable identifier of the user. Use this value, not email, as a unique identifier for users; email addresses can change. If you use the Azure AD Graph API in your app, object ID is that value used to query profile information.
Incorrect:
Not A: aud - Who the token was issued for. This will be the application's client ID.
Reference:
https://docs.microsoft.com/en-us/azure/architecture/multitenant-identity/claims
You are developing an Azure Function that calls external APIs by providing an access token for the API. The access token is stored in a secret named token in an
Azure Key Vault named mykeyvault.
You need to ensure the Azure Function can access to the token. Which value should you store in the Azure Function App configuration?
Answer:
D
Add Key Vault secrets reference in the Function App configuration.
Syntax: @Microsoft.KeyVault(SecretUri={copied identifier for the username secret})
Reference:
https://daniel-krzyczkowski.github.io/Integrate-Key-Vault-Secrets-With-Azure-Functions/
A company maintains multiple web and mobile applications. Each application uses custom in-house identity providers as well as social identity providers.
You need to implement single sign-on (SSO) for all the applications.
What should you do?
Answer:
B
You can add Google as an identity provider for B2B guest users.
Federation with SAML/WS-Fed identity providers for guest users.
Make sure your organization's external collaboration settings are configured such that you're allowed to invite guests.
Note 1: As a user who is assigned any of the limited administrator directory roles, you can use the Azure portal to invite B2B collaboration users. You can invite guest users to the directory, to a group, or to an application. After you invite a user through any of these methods, the invited user's account is added to Azure
Active Directory (Azure AD), with a user type of Guest.
Note 2: Direct federation in Azure Active Directory is now referred to as SAML/WS-Fed identity provider (IdP) federation.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/google-federation https://docs.microsoft.com/en-us/azure/active-directory/external-identities/add-users-administrator
You develop a Python application for image rendering that uses GPU resources to optimize rendering processes. You deploy the application to an Azure
Container Instances (ACI) Linux container.
The application requires a secret value to be passed when the container is started. The value must only be accessed from within the container.
You need to pass the secret value.
What are two possible ways to achieve this goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
AE
A: Secure environment variables -
Another method (another than a secret volume) for providing sensitive information to containers (including Windows containers) is through the use of secure environment variables.
E: Use a secret volume to supply sensitive information to the containers in a container group. The secret volume stores your secrets in files within the volume, accessible by the containers in the container group. By storing secrets in a secret volume, you can avoid adding sensitive data like SSH keys or database credentials to your application code.
Reference:
https://docs.microsoft.com/en-us/azure/container-instances/container-instances-volume-secret
You are developing a user portal for a company.
You need to create a report for the portal that lists information about employees who are subject matter experts for a specific topic. You must ensure that administrators have full control and consent over the data.
Which technology should you use?
Answer:
A
Data Connect grants a more granular control and consent model: you can manage data, see who is accessing it, and request specific properties of an entity. This enhances the Microsoft Graph model, which grants or denies applications access to entire entities.
Microsoft Graph Data Connect augments Microsoft Graph's transactional model with an intelligent way to access rich data at scale. The data covers how workers communicate, collaborate, and manage their time across all the applications and services in Microsoft 365.
Incorrect:
Not B: The Microsoft Graph API is a RESTful web API that enables you to access Microsoft Cloud service resources. After you register your app and get authentication tokens for a user or service, you can make requests to the Microsoft Graph API.
A simplistic definition of a Graph API is an API that models the data in terms of nodes and edges (objects and relationships) and allows the client to interact with multiple nodes in a single request.
Not C: Microsoft Graph connectors, your organization can index third-party data so that it appears in Microsoft Search results.
With Microsoft Graph connectors, your organization can index third-party data so that it appears in Microsoft Search results.
Reference:
https://docs.microsoft.com/en-us/graph/data-connect-concept-overview
HOTSPOT -
You are a developer building a web site using a web app. The web site stores configuration data in Azure App Configuration.
Access to Azure App Configuration has been configured to use the identity of the web app for authentication. Security requirements specify that no other authentication systems must be used.
You need to load configuration data from Azure App Configuration.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: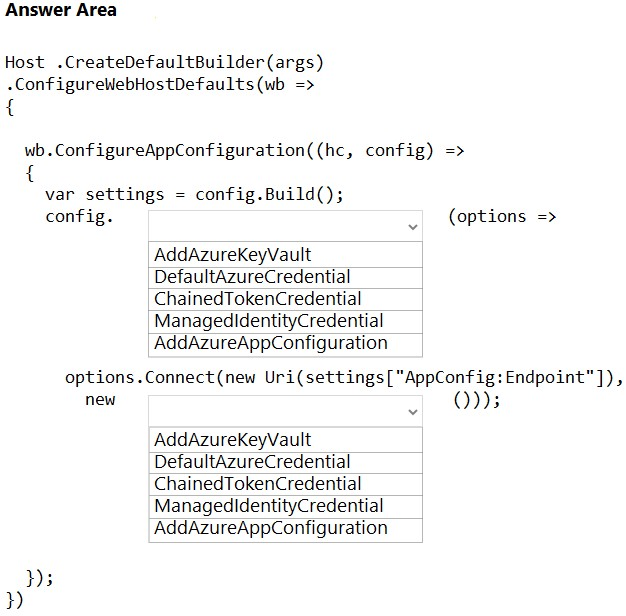
Answer:
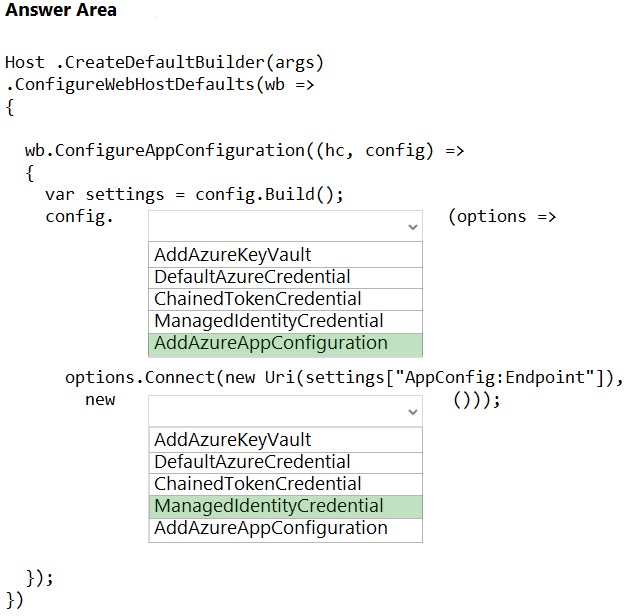
Box 1: AddAzureAppConfiguration -
Load data from App Configuration, code example:
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureWebHostDefaults(webBuilder =>
webBuilder.ConfigureAppConfiguration((hostingContext, config) =>
{
var settings = config.Build();
config.AddAzureAppConfiguration(options =>
{
Etc.
Box 2: ManagedIdentityCredential
Use managed identities to access App Configuration
If you want to use a user-assigned managed identity, be sure to specify the clientId when creating the ManagedIdentityCredential. config.AddAzureAppConfiguration(options =>
{
options.Connect(new Uri(settings["AppConfig:Endpoint"]), new ManagedIdentityCredential("<your_clientId>"))
});
Full code sample:
public static IHostBuilder CreateHostBuilder(string[] args) =>
Host.CreateDefaultBuilder(args)
.ConfigureWebHostDefaults(webBuilder =>
webBuilder.ConfigureAppConfiguration((hostingContext, config) =>
{
var settings = config.Build();
config.AddAzureAppConfiguration(options =>
options.Connect(new Uri(settings["AppConfig:Endpoint"]), new ManagedIdentityCredential()));
})
.UseStartup<Startup>());
Reference:
https://docs.microsoft.com/en-us/azure/azure-app-configuration/howto-integrate-azure-managed-service-identity?tabs=core5x&pivots=framework- dotnet
HOTSPOT -
You are building an application that stores sensitive customer data in Azure Blob storage. The data must be encrypted with a key that is unique for each customer.
If the encryption key has been corrupted it must not be used for encryption.
You need to ensure that the blob is encrypted.
How should you complete the code segment? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: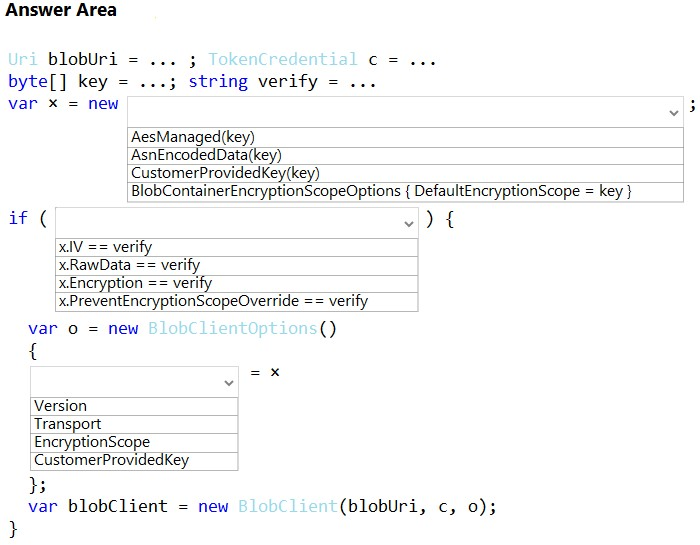
Answer:
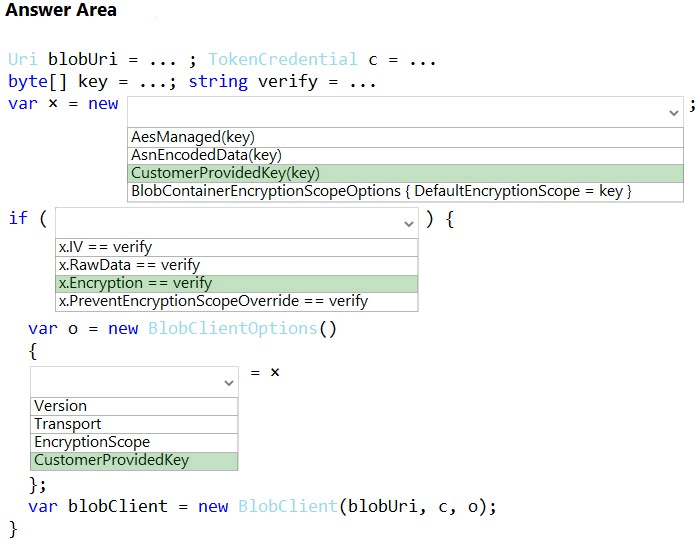
Box 1: CustomerProvidedKey(key)
The data must be encrypted with a key that is unique for each customer.
Sample code:
async static Task UploadBlobWithClientKey(Uri blobUri,
Stream data,
byte[] key,
string keySha256)
{
// Create a new customer-provided key.
// Key must be AES-256.
var cpk = new CustomerProvidedKey(key);
Box 2: Encryption -
CustomerProvidedKey.EncryptionKey Property
Sample code continued:
// Check the key's encryption hash.
if (cpk.EncryptionKeyHash != keySha256)
{
throw new InvalidOperationException("The encryption key is corrupted.");
}
Box 3: CustomerProvidedKey -
Sample code continued;
// Specify the customer-provided key on the options for the client.
BlobClientOptions options = new BlobClientOptions()
{
CustomerProvidedKey = cpk -
};
// Create the client object with options specified.
BlobClient blobClient = new BlobClient(
blobUri,
new DefaultAzureCredential(),
options);
Incorrect:
* Version - Gets the BlobClientOptions.ServiceVersion of the service API used when making requests.
Transport - The HttpPipelineTransport to be used for this client.
Reference:
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-customer-provided-key
HOTSPOT
-
You are developing a web application that uses the Microsoft Identity platform for user and resource authentication. The web application called several REST APIs.
You are implementing various authentication and authorization flows for the web application.
You need to validate the claims in the authentication token.
Which token type should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer:
