Your organization has had a few recent DDoS attacks. You need to authenticate responses to domain name lookups. Which Google Cloud service should you use?
A
Reference:
https://developers.google.com/speed/public-dns/faq
Your Security team believes that a former employee of your company gained unauthorized access to Google Cloud resources some time in the past 2 months by using a service account key. You need to confirm the unauthorized access and determine the user activity. What should you do?
B
Your company requires the security and network engineering teams to identify all network anomalies within and across VPCs, internal traffic from VMs to VMs, traffic between end locations on the internet and VMs, and traffic between VMs to Google Cloud services in production. Which method should you use?
C
Reference:
https://cloud.google.com/architecture/best-practices-vpc-design
Your company has been creating users manually in Cloud Identity to provide access to Google Cloud resources. Due to continued growth of the environment, you want to authorize the Google Cloud Directory Sync (GCDS) instance and integrate it with your on-premises LDAP server to onboard hundreds of users. You are required to:
✑ Replicate user and group lifecycle changes from the on-premises LDAP server in Cloud Identity.
✑ Disable any manually created users in Cloud Identity.
You have already configured the LDAP search attributes to include the users and security groups in scope for Google Cloud. What should you do next to complete this solution?
D
Reference:
https://www.appsadmins.com/blog/your-how-to-for-provisioning-in-g-suite-part-2-users
You are troubleshooting access denied errors between Compute Engine instances connected to a Shared VPC and BigQuery datasets. The datasets reside in a project protected by a VPC Service Controls perimeter. What should you do?
C
Reference:
https://cloud.google.com/vpc-service-controls/docs/troubleshooting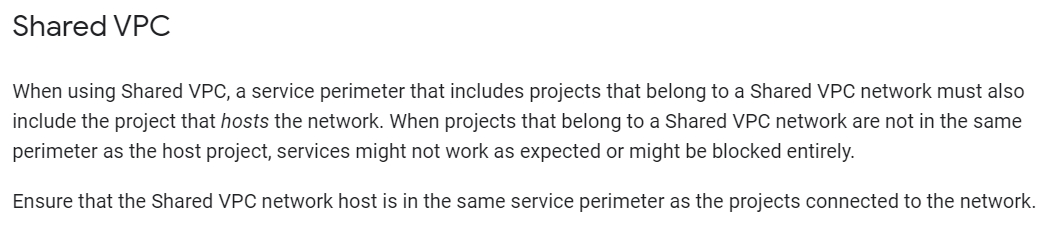
You recently joined the networking team supporting your company's Google Cloud implementation. You are tasked with familiarizing yourself with the firewall rules configuration and providing recommendations based on your networking and Google Cloud experience. What product should you recommend to detect firewall rules that are overlapped by attributes from other firewall rules with higher or equal priority?
D
Reference:
https://cloud.google.com/network-intelligence-center/docs/firewall-insights/concepts/overview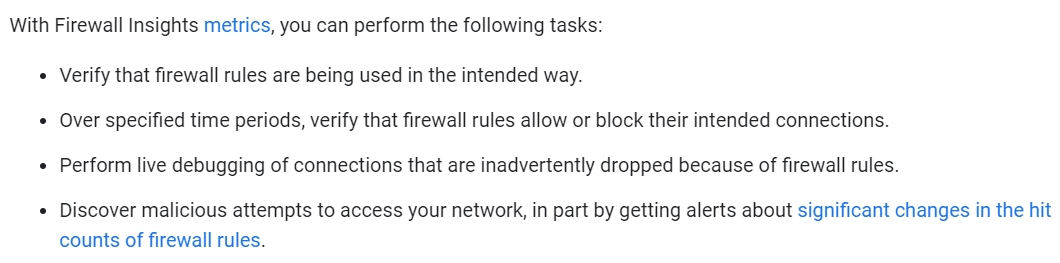
The security operations team needs access to the security-related logs for all projects in their organization. They have the following requirements:
✑ Follow the least privilege model by having only view access to logs.
✑ Have access to Admin Activity logs.
✑ Have access to Data Access logs.
✑ Have access to Access Transparency logs.
Which Identity and Access Management (IAM) role should the security operations team be granted?
B
Reference:
https://cloud.google.com/logging/docs/access-control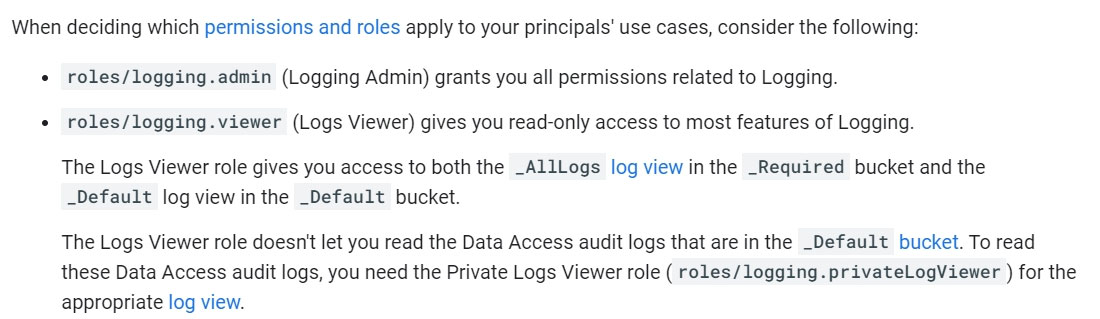
You are exporting application logs to Cloud Storage. You encounter an error message that the log sinks don't support uniform bucket-level access policies. How should you resolve this error?
A
Reference:
https://sysdig.com/blog/gcp-security-best-practices/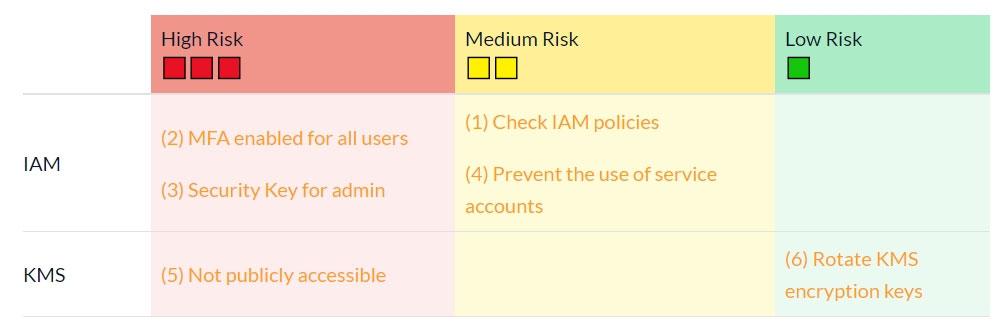
A company has been running their application on Compute Engine. A bug in the application allowed a malicious user to repeatedly execute a script that results in the Compute Engine instance crashing. Although the bug has been fixed, you want to get notified in case this hack re-occurs.
What should you do?
C
Reference:
https://cloud.google.com/logging/docs/logs-based-metrics/
Your team needs to obtain a unified log view of all development cloud projects in your SIEM. The development projects are under the NONPROD organization folder with the test and pre-production projects. The development projects share the ABC-BILLING billing account with the rest of the organization.
Which logging export strategy should you use to meet the requirements?
B