You are asked to recommend a solution to store and retrieve sensitive configuration data from an application that runs on Compute Engine. Which option should you recommend?
D
Reference:
https://www.freecodecamp.org/news/google-cloud-platform-from-zero-to-hero/
You need to implement an encryption at-rest strategy that reduces key management complexity for non-sensitive data and protects sensitive data while providing the flexibility of controlling the key residency and rotation schedule. FIPS 140-2 L1 compliance is required for all data types. What should you do?
B
Your company wants to determine what products they can build to help customers improve their credit scores depending on their age range. To achieve this, you need to join user information in the company's banking app with customers' credit score data received from a third party. While using this raw data will allow you to complete this task, it exposes sensitive data, which could be propagated into new systems.
This risk needs to be addressed using de-identification and tokenization with Cloud Data Loss Prevention while maintaining the referential integrity across the database. Which cryptographic token format should you use to meet these requirements?
B
Reference:
https://cloud.google.com/blog/products/identity-security/take-charge-of-your-data-how-tokenization-makes-data-usable-without-sacrificing-privacy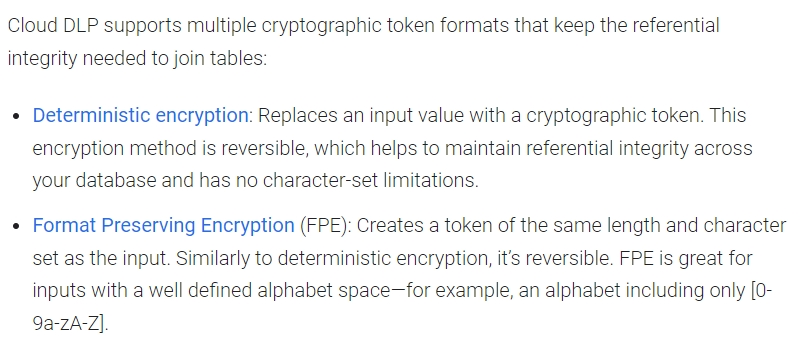
An office manager at your small startup company is responsible for matching payments to invoices and creating billing alerts. For compliance reasons, the office manager is only permitted to have the Identity and Access Management (IAM) permissions necessary for these tasks. Which two IAM roles should the office manager have? (Choose two.)
AE
Reference:
https://cloud.google.com/iam/docs/job-functions/billing
You are designing a new governance model for your organization's secrets that are stored in Secret Manager. Currently, secrets for Production and Non-
Production applications are stored and accessed using service accounts. Your proposed solution must:
✑ Provide granular access to secrets
✑ Give you control over the rotation schedules for the encryption keys that wrap your secrets
✑ Maintain environment separation
✑ Provide ease of management
Which approach should you take?
A
You are a security engineer at a finance company. Your organization plans to store data on Google Cloud, but your leadership team is worried about the security of their highly sensitive data. Specifically, your company is concerned about internal Google employees' ability to access your company's data on Google Cloud.
What solution should you propose?
D
You want to use the gcloud command-line tool to authenticate using a third-party single sign-on (SSO) SAML identity provider. Which options are necessary to ensure that authentication is supported by the third-party identity provider (IdP)? (Choose two.)
AC
Reference:
https://cloud.google.com/identity/solutions/enable-sso
You work for a large organization where each business unit has thousands of users. You need to delegate management of access control permissions to each business unit. You have the following requirements:
✑ Each business unit manages access controls for their own projects.
✑ Each business unit manages access control permissions at scale.
✑ Business units cannot access other business units' projects.
✑ Users lose their access if they move to a different business unit or leave the company.
✑ Users and access control permissions are managed by the on-premises directory service.
What should you do? (Choose two.)
BE
Your organization recently deployed a new application on Google Kubernetes Engine. You need to deploy a solution to protect the application. The solution has the following requirements:
✑ Scans must run at least once per week
✑ Must be able to detect cross-site scripting vulnerabilities
✑ Must be able to authenticate using Google accounts
Which solution should you use?
B
Reference:
https://cloud.google.com/security-command-center/docs/concepts-web-security-scanner-overview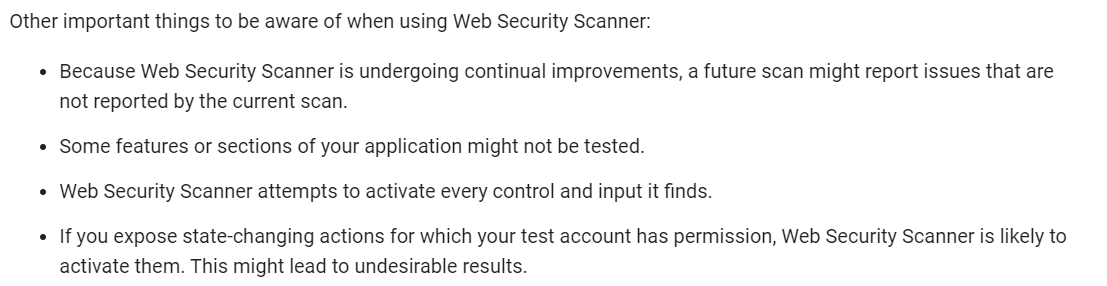
An organization is moving applications to Google Cloud while maintaining a few mission-critical applications on-premises. The organization must transfer the data at a bandwidth of at least 50 Gbps. What should they use to ensure secure continued connectivity between sites?
A
Reference:
https://cloud.google.com/architecture/migration-to-google-cloud-transferring-your-large-datasets